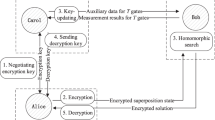
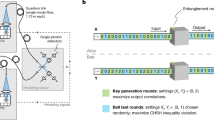
Abstract
Secure communication is crucial in the Internet Age, and quantum mechanics stands poised to revolutionize cryptography as we know it today. In this Review, we introduce the motivation and the current state of the art of research in quantum cryptography. In particular, we discuss the present security model together with its assumptions, strengths and weaknesses. After briefly introducing recent experimental progress and challenges, we survey the latest developments in quantum hacking and countermeasures against it.
This is a preview of subscription content, access via your institution
Access options
Subscribe to this journal
Receive 12 print issues and online access
$209.00 per year
only $17.42 per issue
Buy this article
- Purchase on Springer Link
- Instant access to full article PDF
Prices may be subject to local taxes which are calculated during checkout





Similar content being viewed by others
References
Rivest, R. L., Shamir, A. & Adleman, L. M. A method of obtaining digital signatures and public-key cryptosystems. Commun. ACM 21, 120–126 (1978).
Shor, P. W. Algorithms for quantum computation: discrete logarithms and factoring. in Proc. 35th Ann. Symp. Found. Comp. Sci. (ed. Goldwasser, S.) 124–134 (IEEE, 1994).
Ben-Or, M., Horodecki, M., Leung, D. W., Mayers, D. & Oppenheim, J. The universal composable security of quantum key distribution. in Theory of Cryptography (ed. Kilian, J.) 3378, 386–406 (Springer, 2005).
Renner, R. & König, R. Universally composable privacy amplification against quantum adversaries. in Theory of Cryptography (ed. Kilian, J.) 3378, 407–425 (Springer, 2005).
Yoshino, K., Ochi, T., Fujiwara, M., Sasaki, M. & Tajima, A. Maintenance-free operation of WDM quantum key distribution system through a field fiber over 30 days. Opt. Express 21, 31395–31401 (2013).
Ursin, R. et al. Entanglement-based quantum communication over 144 km. Nature Phys. 3, 481–486 (2007).
Elliott, C. et al. Current status of the DARPA Quantum Network. in Proc. SPIE (eds Donkor, E. J., Pirich, A. R. & Brandt, H. E.) 5815, 138–149 (SPIE, 2005).
Peev, M. et al. The SECOQC quantum key distribution network in Vienna. New J. Phys. 11, 075001 (2009).
Stucki, D. et al. Long-term performance of the SwissQuantum quantum key distribution network in a field environment. New J. Phys. 13, 123001 (2011).
Chen, T.-Y. et al. Field test of a practical secure communication network with decoy-state quantum cryptography. Opt. Express 17, 6540–6549 (2009).
Chen, T.-Y. et al. Metropolitan all-pass and inter-city quantum communication network. Opt. Express 18, 27217–27225 (2010).
Wang, S. et al. Field test of wavelength-saving quantum key distribution network. Opt. Lett. 35, 2454–2456 (2010).
Sasaki, M. et al. Field test of quantum key distribution in the Tokyo QKD network. Opt. Express 19, 10387–10409 (2011).
Fröhlich, B. et al. A quantum access network. Nature 501, 69–72 (2013).
Marsili, F. et al. Detecting single infrared photons with 93% system efficiency. Nature Photon. 7, 210–214 (2013).
Rosenberg, D., Kerman, A. J., Molnar, R. J. & Dauler, E. A. High-speed and high-efficiency superconducting nanowire single photon detector array. Opt. Express 21, 1440–1447 (2013).
Miki, S., Yamashita, T., Terai, H. & Wang, Z. High performance fiber-coupled NbTiN superconducting nanowire single photon detectors with Gifford-McMahon cryocooler. Opt. Express 21, 10208–10214 (2013).
Restelli, A., Bienfang, J. C. & Migdall, A. L. Single-photon detection efficiency up to 50% at 1310 nm with an InGaAs/InP avalanche diode gated at 1.25 GHz. Appl. Phys. Lett. 102, 141104 (2013).
Bennett, C. H., Bessette, F., Brassard, G., Salvail, L. & Smolin, J. Experimental quantum cryptography. J. Cryptol. 5, 3–28 (1992).
Wang, J.-Y. et al. Direct and full-scale experimental verifications towards ground-satellite quantum key distribution. Nature Photon. 7, 387–393 (2013).
Nauerth, S. et al. Air-to-ground quantum communication. Nature Photon. 7, 382–386 (2013).
Lim, C. C. W., Curty, M., Walenta, N., Xu, F. & Zbinden, H. Concise security bounds for practical decoy-state quantum key distribution. Phys. Rev. A 89, 022307 (2014).
Bennett, C. H. & Brassard, G. Quantum cryptography: public key distribution and coin tossing. in Proc. IEEE Int. Conf. Comp. Systems Signal Processing 175–179 (IEEE, 1984).
Huttner, B., Imoto, N., Gisin, N. & Mor, T. Quantum cryptography with coherent states. Phys. Rev. A 51, 1863–1869 (1995).
Gottesman, D., Lo, H.-K., Lütkenhaus, N. & Preskill, J. Security of quantum key distribution with imperfect devices. Quant. Inf. Comp. 5, 325–360 (2004).
Hwang, W.-Y. Quantum key distribution with high loss: toward global secure communication. Phys. Rev. Lett. 91, 057901 (2003).
Lo, H.-K., Ma, X. & Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504 (2005).
Wang, X.-B. Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 94, 230503 (2005).
Ma, X., Qi, B., Zhao, Y. & Lo, H.-K. Practical decoy state for quantum key distribution. Phys. Rev. A 72, 012326 (2005).
Zhao, Y., Qi, B., Ma, X., Lo, H.-K. & Qian, L. Experimental quantum key distribution with decoy states. Phys. Rev. Lett. 96, 070502 (2006).
Peng, C.-Z. et al. Experimental long-distance decoy-state quantum key distribution based on polarization encoding. Phys. Rev. Lett. 98, 010505 (2007).
Rosenberg, D. et al. Long-distance decoy-state quantum key distribution in optical fiber. Phys. Rev. Lett. 98, 010503 (2007).
Schmitt-Manderbach, T. et al. Experimental demonstration of free-space decoy-state quantum key distribution over 144 km. Phys. Rev. Lett. 98, 010504 (2007).
Yuan, Z. L., Sharpe, A. W. & Shields, A. J. Unconditionally secure one-way quantum key distribution using decoy pulses. Appl. Phys. Lett. 90, 011118 (2007).
Liu, Y. et al. Decoy-state quantum key distribution with polarized photons over 200 km. Opt. Express 18, 8587–8594 (2010).
Wehner, S., Curty, M., Schaffner, C. & Lo, H.-K. Implementation of two-party protocols in the noisy-storage model. Phys. Rev. A 81, 052336 (2010).
Hughes, R. J. et al. Network-centric quantum communications with application to critical infrastructure protection. Preprint at http://lanl.arXiv.org/abs/1305.0305 (2013).
Ekert, A. K. Quantum cryptography based on Bell's theorem. Phys. Rev. Lett. 67, 661–663 (1991).
Ma, X., Fung, C.-H. F. & Lo, H.-K. Quantum key distribution with entangled photon sources. Phys. Rev. A 76, 012307 (2007).
Treiber, A. et al. Fully automated entanglement-based quantum cryptography system for telecom fiber networks. New J. Phys. 11, 045013 (2009).
Poppe, A. et al. Practical quantum key distribution with polarization-entangled photons. Opt. Express 12, 3865–3871 (2004).
Inoue, K., Waks, E. & Yamamoto, Y. Differential phase shift quantum key distribution. Phys. Rev. Lett. 89, 037902 (2002).
Takesue, H. et al. Quantum key distribution over a 40-dB channel loss using superconducting single-photon detectors. Nature Photon. 1, 343–348 (2007).
Stucki, D. et al. High rate, long-distance quantum key distribution over 250 km of ultra low loss fibres. New J. Phys. 11, 075003 (2009).
Grosshans, F. et al. Quantum key distribution using gaussian-modulated coherent states. Nature 421, 238–241 (2003).
Qi, B., Huang, L.-L., Qian, L. & Lo, H.-K. Experimental study on the Gaussian-modulated coherent-state quantum key distribution over standard telecommunication fibers. Phys. Rev. A 76, 052323 (2007).
Jouguet, P., Kunz-Jacques, S., Leverrier, A., Grangier, P. & Diamanti, E. Experimental demonstration of long-distance continuous-variable quantum key distribution. Nature Photon. 7, 378–381 (2013).
Yuan, Z. L., Kardynal, B. E., Sharpe, A. W. & Shields, A. J. High speed single photon detection in the near infrared. App. Phys. Lett. 91, 041114 (2007).
Dixon, A. R. et al. Ultrashort dead time of photon-counting InGaAs avalanche photodiodes. Appl. Phys. Lett. 94, 231113 (2009).
Namekata, N., Sasamori, S. & Inoue, S. 800 MHz single-photon detection at 1550-nm using an InGaAs/InP avalanche photodiode operated with a sine wave gating. Opt. Express 14, 10043–10049 (2006).
Liang, X.-L. et al. Fully integrated InGaAs/InP single-photon detector module with gigahertz sine wave gating. Rev. Sci. Instrum. 83, 083111 (2012).
Wu, Q.-L., Namekata, N. & Inoue, S. Sinusoidally gated InGaAs avalanche photodiode with direct hold-off function for efficient and low-noise single-photon detection. Appl. Phys. Express 6, 062202 (2013).
Zhang, J., Thew, R., Barreiro, C. & Zbinden, H. Practical fast gate rate InGaAs/InP single-photon avalanche photodiodes. Appl. Phys. Lett. 95, 091103 (2009).
Shibata, H., Takesue, H., Honjo, T., Akazaki, T. & Tokura, Y. Single-photon detection using magnesium diboride superconducting nanowires. Appl. Phys. Lett. 97, 212504 (2010).
Pironio, S. et al. Random numbers certified by Bell's theorem. Nature 464, 1021–1024 (2010).
Williams, C. R. S., Salevan, J. C., Li, X., Roy, R. & Murphy, T. E. Fast physical random number generator using amplified spontaneous emission. Opt. Express 18, 23584–23597 (2010).
Jofre, M. et al. True random numbers from amplified quantum vacuum. Opt. Express 19, 20665–20672 (2011).
Abellán, C. et al. Ultra-fast quantum randomness generation by accelerated phase diffusion in a pulsed laser diode. Opt. Express 22, 1645–1654 (2014).
Qi, B., Chi, Y.-M., Lo, H.-K. & Qian, L. High-speed quantum random number generation by measuring phase noise of a single-mode laser. Opt. Lett. 35, 312–314 (2010).
Dixon, A. R., Yuan, Z. L., Dynes, J. F., Sharpe, A. W. & Shields, A. J. Continuous operation of high bit rate quantum key distribution. Appl. Phys. Lett. 96, 161102 (2010).
Choi, I., Young, R. J. & Townsend, P. D. Quantum key distribution on a 10Gb/s WDM-PON. Opt. Express 18, 9600–9612 (2010).
Patel, K. A. et al. Coexistence of high-bit-rate quantum key distribution and data on optical fiber. Phys. Rev. X 2, 041010 (2012).
Chapuran, T. E. et al. Optical networking for quantum key distribution and quantum communications. New J. Phys. 11, 105001 (2009).
Patel, K. A. et al. Quantum key distribution for 10 Gb/s dense wavelength division multiplexing networks. Appl. Phys. Lett. 104, 051123 (2014).
Dixon, A. R., Yuan, Z. L., Dynes, J. F., Sharpe, A. W. & Shields, A. J. Gigahertz decoy quantum key distribution with 1 Mbit/s secure key rate. Opt. Express 16, 18790–18979 (2008).
Zhang, Q. et al. Megabits secure key rate quantum key distribution. New J. Phys. 11, 045010 (2009).
Tanaka, A. et al. High-speed quantum key distribution system for 1-Mbps real-time key generation. IEEE J. Quant. Electron. 48, 542–550 (2012).
Walenta, N. et al. 1 Mbps coherent one-way QKD with dense wavelength division multiplexing and hardware key distillation. in Proc. 2nd Ann. Conf. Quantum Cryptography (2012).
Qi, B., Zhu, W., Qian, L. & Lo, H.-K. Feasibility of quantum key distribution through dense wavelength division multiplexing network. New J. Phys. 12, 103042 (2010).
Jouguet, P. et al. Experimental demonstration of the coexistence of continuous-variable quantum key distribution with an intense DWDM classical channel. in Proc. 3rd Ann. Conf. Quantum Cryptography (2013).
Raymer, M. G., Cooper, J., Carmichael, H. J., Beck M. & Smithey, D. T. Ultrafast measurement of optical-field statistics by dc-balanced homodyne detection. J. Opt. Soc. Am. B 12, 1801–1812 (1995).
Hayashi, M. & Tsurumaru, T. Concise and tight security analysis of the Bennett–Brassard 1984 protocol with finite key lengths. New J. Phys. 14, 093014 (2012).
Curty, M. et al. Finite-key analysis for measurement-device-independent quantum key distribution. Nature Commun. 5, 3732 (2014).
Lo, H.-K., Curty, M. & Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108, 130503 (2012).
Qi, B., Fung, C.-H. F., Lo, H.-K. & Ma, X. Time-shift attack in practical quantum cryptosystems. Quant. Inf. Comp. 7, 73–82 (2007).
Zhao, Y., Fung, C.-H. F., Qi, B., Chen, C. & Lo, H.-K. Quantum hacking: experimental demonstration of time-shift attack against practical quantum-key-distribution systems. Phys. Rev. A 78, 042333 (2008).
Makarov, V., Anisimov, A. & Skaar, J. Effects of detector efficiency mismatch on security of quantum cryptosystems. Phys. Rev. A 74, 022313 (2006).
Makarov, V., Anisimov, A. & Skaar, J. Erratum: effects of detector efficiency mismatch on security of quantum cryptosystems [Phys. Rev. A 74, 022313 (2006)]. Phys. Rev. A 78, 019905 (2008).
Lamas-Linares, A. & Kurtsiefer, C. Breaking a quantum key distribution system through a timing side channel. Opt. Express 15, 9388–9393 (2007).
Lydersen, L. et al. Hacking commercial quantum cryptography systems by tailored bright illumination. Nature Photon. 4, 686–689 (2010).
Yuan, Z. L., Dynes, J. F. & Shields, A. J. Avoiding the blinding attack in QKD. Nature Photon. 4, 800–801 (2010).
Lydersen, L. et al. Reply to “Avoiding the blinding attack in QKD”. Nature Photon. 4, 801 (2010).
Gerhardt, I. et al. Full-field implementation of a perfect eavesdropper on a quantum cryptography system. Nature Commun. 2, 349 (2011).
Weier, H. et al. Quantum eavesdropping without interception: an attack exploiting the dead time of single-photon detectors. New J. Phys. 13, 073024 (2011).
Jain, N. et al. Device calibration impacts security of quantum key distribution. Phys. Rev. Lett. 107, 110501 (2011).
Xu, F., Qi, B. & Lo, H.-K. Experimental demonstration of phase-remapping attack in a practical quantum key distribution system. New J. Phys. 12, 113026 (2010).
Sun, S.-H., Jiang, M.-S. & Liang, L.-M. Passive Faraday-mirror attack in a practical two-way quantum-key-distribution system. Phys. Rev. A 83, 062331 (2011).
Huang, J.-Z. et al. Quantum hacking on continuous-variable quantum key distribution system using a wavelength attack. Phys. Rev. A 87, 062329 (2013).
Tang, Y.-L. et al. Source attack of decoy-state quantum key distribution using phase information. Phys. Rev. A 88, 022308 (2013).
Jouguet, P., Kunz-Jacques, S. & Diamanti, E. Preventing calibration attacks on the local oscillator in continuous-variable quantum key distribution. Phys. Rev. A 87, 062313 (2013).
Tamaki, K., Curty, M., Kato, G., Lo, H.-K. & Azuma, K. Loss-tolerant quantum cryptography with imperfect sources. Preprint at http://lanl.arXiv.org/abs/1312.3514 (2013).
Yuan, Z. L., Dynes, J. F. & Shields, A. J. Resilience of gated avalanche photodiodes against bright illumination attacks in quantum cryptography. Appl. Phys. Lett. 98, 231104 (2011).
Lydersen, L., Makarov, V. & Skaar, J. Comment on “Resilience of gated avalanche photodiodes against bright illumination attacks in quantum cryptography”. Appl. Phys. Lett. 99, 196101 (2011).
Yuan, Z. L., Dynes, J. F. & Shields, A. J. Response to “Comment on 'Resilience of gated avalanche photodiodes against bright illumination attacks in quantum cryptography”' Appl. Phys. Lett. 99, 196102 (2011).
Honjo, T. et al. Countermeasure against tailored bright illumination attack for DPS-QKD. Opt. Express 21, 2667–2673 (2013).
Mayers, D. & Yao, A. Quantum cryptography with imperfect apparatus. in Proc. 39th Ann. Symp. Foundations Comp. Sci. 503–509 (IEEE, 1998).
Masanes, L., Pironio, S. & Acín, A. Secure device-independent quantum key distribution with causally in-dependent measurement devices. Nature Commun. 2, 238 (2011).
Reichardt, B. W., Unger, F. & Vazirani, U. Classical command of quantum systems. Nature 496, 456–460 (2013).
Vazirani, U. & Vidick, T. Fully device independent quantum key distribution. Preprint at http://lanl.arXiv.org/abs/1210.1810 (2012).
Gisin, N., Pironio, S. & Sangouard, N. Proposal for implementing device-independent quantum key distribution based on a heralded qubit amplifier. Phys. Rev. Lett. 105, 070501 (2010).
Curty, M. & Moroder, T. Heralded-qubit amplifiers for practical device-independent quantum key distribution. Phys. Rev. A 84, 10.1103/PhysRevA.84.010304 010304(R)(2011).
Biham, E., Huttner, B. & Mor, T. Quantum cryptographic network based on quantum memories. Phys. Rev. A 54, 2651–2658 (1996).
Inamori, H. Security of practical time-reversed EPR quantum key distribution. Algorithmica 34, 340–365 (2002).
Rubenok, A., Slater, J. A., Chan, P., Lucio-Martinez, I. & Tittel, W. Real-world two-photon interference and proof-of-principle quantum key distribution immune to detector attacks. Phys. Rev. Lett. 111, 130501 (2013).
Ferreira da Silva, T. et al. Proof-of-principle demonstration of measurement-device-independent quantum key distribution using polarization qubits. Phys. Rev. A 88, 052303 (2013).
Liu, Y. et al. Experimental measurement-device-independent quantum key distribution. Phys. Rev. Lett. 111, 130502 (2013).
Tang, Z. et al. Experimental demonstration of polarization encoding measurement-device-independent quantum key distribution. Phys. Rev. Lett. 112, 190503 (2014).
Briegel, H.-J., Dür, W., Cirac, J. I. & Zoller, P. Quantum repeaters: the role of imperfect local operations in quantum communication. Phys. Rev. Lett. 81, 5932–5935 (1998).
Vernam, G. S. Cipher printing telegraph systems: for secret wire and radio telegraphic communications. J. Am. Inst. Electr. Eng. 45, 109–115 (1926).
Acknowledgements
The authors thank K. Azuma, C. H. Bennett, M. Fujiwara, G. Kato, N. Matsuda, N. Namekata, T. Ochi, B. Qi, L. Qian, M. Sasaki, H. Shibata, H. Takesue, F. Xu, K. Yoshino, Q. Zhang, Y. Zhao and the anonymous referees for their valuable comments and suggestions. We specially thank C. H. Bennett and R. J. Hughes for allowing us to use photographs of the first experimental demonstration of QKD and of the first-generation, modularly integrated QKarD respectively in this Review. We thank Z. Tang for technical support in formatting our manuscript. We acknowledge support from the European Regional Development Fund (ERDF), the Galician Regional Government (projects CN2012/279 and CN 2012/260, “Consolidation of Research Units: AtlantTIC”), NSERC, the CRC program, the Connaught Innovation Award, and the project “Secure Photonic Network Technology” as part of the project UQCC by the National Institute of Information and Communications Technology (NICT) of Japan, as well as from the Japan Society for the Promotion of Science (JSPS) through its Funding Program for World-Leading Innovative R&D on Science and Technology (FIRST Program).
Author information
Authors and Affiliations
Corresponding authors
Ethics declarations
Competing interests
H.-K.L. is a named inventor on US Patent #8,554,814, “Random signal generator using quantum noise” (2013), which is related to the methods described in ref. 59. M.C. is a named inventor on patents and pending patents related to the methods described in refs 57 and 58. K.T. declares no competing financial interests other than his employment with NTT, Basic Research Lab.
Rights and permissions
About this article
Cite this article
Lo, HK., Curty, M. & Tamaki, K. Secure quantum key distribution. Nature Photon 8, 595–604 (2014). https://doi.org/10.1038/nphoton.2014.149
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1038/nphoton.2014.149
This article is cited by
-
High-dimensional single photon based quantum secure direct communication using time and phase mode degrees
Scientific Reports (2024)
-
Improved security bounds against the Trojan-horse attack in decoy-state quantum key distribution
Quantum Information Processing (2024)
-
Quantum correlation of the Heisenberg xxz Hamiltonian with nonuniform external magnetic field and Dzyaloshinskii–Moriya interaction
Indian Journal of Physics (2024)
-
Advances in device-independent quantum key distribution
npj Quantum Information (2023)
-
Multiple channelling single-photon emission with scattering holography designed metasurfaces
Nature Communications (2023)