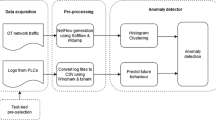
Abstract
The increasing development of cryptocurrencies has brought cryptojacking as a new security threat in which attackers steal computing resources for cryptomining. The digitization of the supply chain is a potential major target for cryptojacking due to the large number of different infrastructures involved. These different infrastructures provide information sources that can be useful to detect cryptojacking, but with a wide variety of data formats and encodings. This paper describes the semantic data aggregator (SDA), a normalization and aggregation system based on data modelling and low-latency processing of data streams that facilitates the integration of heterogeneous information sources. As a use case, the paper describes a cryptomining detection system (CDS) based on network traffic flows processed by a machine learning engine. The results show how the SDA is leveraged in this use case to obtain aggregated information that improves the performance of the CDS.














Similar content being viewed by others
Data Availability
The code of the framework can be accessed here: https://github.com/giros-dit/semantic-data-aggregator. While the data and scripts for the results can be accessed here: https://github.com/aams-eam/ALSDA.
References
Zhang D, He M, Wang X, Tehranipoor M (2017) Dynamically obfuscated scan for protecting IPs against scan-based attacks throughout supply chain. In: 2017 IEEE 35th VLSI Test symposium (VTS). pp 1–6
Heinbockel WJ, Laderman ER, Serrao GJ (2017) Supply chain attacks and resiliency mitigations. In: Guidance for system security engineers
H H2020 Fishy, a coordinated framework for cyber resilient supply chain systems. [Online]. Available: https://fishy-project.eu/
Pastor A, Mozo A, Lopez DR, Folgueira J, Kapodistria A (2018) The Mouseworld, a security traffic analysis lab based on NFV/SDN. In: Proceedings of the 13th international conference on availability, reliability and security, ARES 2018. Association for Computing Machinery New York, NY, USA
Moreno-Sancho AA, Pastor A, Martinez-Casanueva ID, González-Sánchez D, Triana LB (2023) A data infrastructure for heterogeneous telemetry adaptation. application to Netflow-based cryptojacking detection. In: 2023 26th conference on innovation in clouds, internet and networks and workshops (ICIN). pp 105–112
FISHY (2022) D6.2 it-1 fishy release validated. In: A coordinated framework for cyber resilient supply chain systems over complex ICT infrastructures
H. H2020 Palantir, practical autonomous cyberhealth for resilient SMEs & microenterprises.” [Online]. Available: https://www.palantir-project.eu/
Claise B (2004) Cisco systems Netflow services export version 9. RFC 3954, RFC Editor, 10
Soni S, Bhushan B (2019) Use of machine learning algorithms for designing efficient cyber security solutions. In: 2019 2nd international conference on intelligent computing, instrumentation and control technologies (ICICICT), vol 1. pp 1496–1501
Geneiatakis D, Kozik R, Pawlicki M, Choraś M (2018) Cost-sensitive distributed machine learning for Netflow-based botnet activity detection. Secur Commun Netw
Buczak AL, Guven E (2016) A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun Surv Tutor 18(2):1153–1176
Delplace A, Hermoso S, Anandita K (2020) Cyber attack detection thanks to machine learning algorithms
Campazas-Vega A, Crespo-Martínez IS, Guerrero-Higueras AM, Fernández-Llamas C (2020) Flow-data gathering using Netflow sensors for fitting malicious-traffic detection models. Sensors 20:24
Sarhan M, Layeghy S, Moustafa N, Portmann M (2021) Netflow datasets for machine learning-based network intrusion detection systems. In: Deze Z, Huang H, Hou R, Rho S, Chilamkurti N (eds) Big data technologies and applications. Springer International Publishing, Cham, pp 117–135
Cisco (2019) Netflow switching enhancements feature module. [Online] Available: https://web.archive.org/web/20091221041522http://www.cisco.com/en/US/docs/ios/11_2/feature/guide/netflow.html Accessed 21 Dec 2019
Cisco (2011) Netflow version 9 flow-record format. [Online]. Available: https://www.cisco.com/en/US/technologies/tk648/tk362/technologies_white_paper09186a00800a3db9.html. Accessed: March 2022
Enns R, Bjorklund M, Schoenwaelder J, Bierman A (2011) Network configuration protocol (NETCONF). RFC 6241, RFC Editor
Bjorklund M (2010) YANG - a data modeling language for the network configuration protocol (NETCONF). RFC 6020, RFC Editor
YangModels (2020) YANG vendor Cisco xr 622. [Online] Available: https://github.com/YangModels/yang/tree/main/vendor/cisco/xr/622 Accessed 2017
Cisco (2015) Cisco-ios-xr-traffmon-netflow-cfg.” [Online]. Available: https://github.com/YangModels/yang/tree/main/vendor/cisco/xr/622 Accessed 19 Nov 2015
González-Sánchez D, Martinez-Casanueva ID, Pastor A, Triana LB, Zamarro CPM, Sancho AAM, Cambronero DF, Lopez D (2022) Model-driven network monitoring using Netflow applied to threat detection. In: 2022 IEEE 8th International conference on network softwarization (NetSoft). pp 450–455
O’Kane P, Sezer S, Carlin D (2018) Evolution of ransomware. IET. Networks 7(5):321–327
Symantec C (2019) Internet security threat report 2019. [Online] Available: https://docs.broadcom.com/doc/istr-24-2019-en. Accessed: March 2022
Frankenfield J (2022) Mining pool. [Online] Available: https://www.investopedia.com/terms/m/mining-pool.asp Accessed 15 Jan 2022
Caprolu M, Raponi S, Oligeri G, Di Pietro R (2021) Cryptomining makes noise: detecting cryptojacking via machine learning. Comput Comm 171:126–139
Kharraz A, Ma Z, Murley P, Lever C, Mason J, Miller A, Borisov N, Antonakakis M, Bailey M (2019) Outguard: detecting in-browser covert cryptocurrency mining in the wild. The World Wide Web Conference, WWW ’19. Association for Computing Machinery, New York, NY, USA, pp 840–852
Yulianto AD, Sukarno P, Warrdana AA, Makky MA (2019) Mitigation of cryptojacking attacks using taint analysis,” In: 2019 4th International conference on information technology, information systems and electrical engineering (ICITISEE). pp 234–238
Tanana D (2020) Behavior-based detection of cryptojacking malware. In: 2020 Ural symposium on biomedical engineering, radioelectronics and information technology (USBEREIT). pp 0543–0545
Mani G, Pasumarti V, Bhargava B, Vora FT, MacDonald J, King J, Kobes J (2020) Decrypto pro: deep learning based cryptomining malware detection using performance counters. In: 2020 IEEE International conference on autonomic computing and self-organizing systems (ACSOS). pp 109–118
Tahir R, Durrani S, Ahmed F, Saeed H, Zaffar F, Ilyas S (2019) The browsers strike back: countering cryptojacking and parasitic miners on the web. In: IEEE INFOCOM 2019 - IEEE Conference on computer communications. pp 703–711
Petrov I, Invernizzi L, Bursztein E (2020) CoinPolice: detecting hidden cryptojacking attacks with neural networks
Cunha Neto HN, Martin Andreoni L, Fernandes NC, Mattos DMF (2020) MineCap: super incremental learning for detecting and blocking cryptocurrency mining on software-defined networking. Ann Telecommun
Rodriguez JDP, Posegga J (2018) RAPID: Resource and API-based detection against in-browser miners. In: Proceedings of the 34th annual computer security applications conference, ACSAC ’18. Association for Computing Machinery, New York, NY, USA pp 313–326
Ning R, Wang C, Xin C, Li J, Zhu L, Wu H (2019) CapJack: capture in-browser crypto-jacking by deep capsule network through behavioral analysis. In: IEEE INFOCOM 2019 - IEEE conference on computer communications. pp 1873–1881
Kelton C, Balasubramanian A, Raghavendra R, Srivatsa M (2020) Browser-based deep behavioral detection of web cryptomining with CoinSpy. In: Workshop on measurements, attacks, and defenses for the web (MADWeb) 2020. pp 1–12
Li Z, Hou J, Wang H, Wang C, Kang C, Fu P (2019) Ethereum behavior analysis with Netflow data. In: 2019 20th Asia-Pacific network operations and management symposium (APNOMS). pp 1–6
Zayuelas i Muñoz J, Suárez-Varela J, Barlet-Ros P (2019) Detecting cryptocurrency miners with Netflow/IPFIX network measurements. In: 2019 IEEE International symposium on measurements & networking (M &N). pp 1–6
Pastor A, Mozo A, Vakaruk S, Canavese D, López DR, Regano L, Gómez-Canaval S, Lioy A (2020) Detection of encrypted cryptomining malware connections with machine and deep learning. IEEE Access 8:158036–158055
AS Foundation. Apache flink. [Online]. Available: https://flink.apache.org/. Accessed May 2011
netsampler. Goflow2. [Online]. Available: https://github.com/netsampler/goflow2/releases Accessed 26 May2021
OpenDaylight. Yang tools. [Online]. Available: https://docs.opendaylight.org/en/stable-sulfur/developer-guides/yang-tools.html
mbj4668. Pyang. [Online]. Available: https://github.com/mbj4668/pyang Accessed 14 Jan 2020
openconfig. ygot. [Online]. Available: https://github.com/openconfig/ygot. Accessed 11 June 2019
DIT-UPM G. SDA tool source code. [Online]. Available: https://github.com/giros-dit/semantic-data-aggregator. Accessed 30 June 2022
Qin J, Kruber N. Getting into low-latency gears with apache Flink - part one. [Online]. Available: https://flink.apache.org/2022/05/18/latency-part1.html. Accessed 18 May 2022
Polito. TStat (TCP statistic and analysis tool). [Online]. Available: http://tstat.polito.it/. Accessed 30 May 2016
Acknowledgements
The research leading to these results received funding from the European Union’s Horizon 2020 research and innovation program under grant agreement no. 952644 (FISHY) and no. 883335 (PALANTIR). The paper reflects only the author view. The Commission is not responsible for any use that may be made of the information it contains.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no competing interests.
Disclaimer
The paper reflects only the authors’ view. The commission is not responsible for any use that may be made of the information it contains.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Moreno-Sancho, A.A., Pastor, A., Martinez-Casanueva, I.D. et al. A data infrastructure for heterogeneous telemetry adaptation: application to Netflow-based cryptojacking detection. Ann. Telecommun. 79, 241–256 (2024). https://doi.org/10.1007/s12243-023-00991-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12243-023-00991-6