Abstract
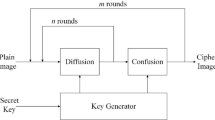
Due to the interesting nonlinear dynamic properties of chaotic maps, recently chaos-based encryption algorithms have gained much attention in cryptographic communities. However, many encryption schemes do not fulfil the minimum key space requirement, which is an essential concern in many secure data applications. In this paper, an efficient chaos-based image encryption scheme with higher key space is presented. Even with a single round of encryption, a significantly larger key space can be achieved. The proposed scheme removes correlation among image pixels via random chaotic sequences, simply by XOR and addition operations. In order to resist against numerous attacks, we apply the affine transformation to get the final ciphertext image. The security of the proposed scheme is proved through histogram, contrast, PSNR, entropy, correlation, key space, key sensitivity and differential attack analysis. Many significant properties of chaotic maps, sensitivity to initial condition and control parameters, structure and attack complexity, make the anticipated scheme very reliable, practical and robust in various secure communication applications.
















Similar content being viewed by others
References
Ahmad M, Ahmad F (2015) Cryptanalysis of image encryption based on permutation-substitution using chaotic map and latin square image cipher. In: Proceedings of the 3rd international conference on frontiers of intelligent computing: theory and applications (FICTA) 2014. Springer, Berlin, pp 481–488
Ahmad J, Ahmed F (2012) Efficiency analysis and security evaluation of image encryption schemes. IJENS 23:18–31
Akhavan A, Samsudin A, Akhshani A (2015) Cryptanalysis of an improvement over an image encryption method based on total shuffling. Opt Commun 350:77–82
Alvarez G, Li S (2006) Some basic cryptographic requirements for chaos-based cryptosystems. Int J Bifurcation Chaos 16(08):2129–2151
Anees A, Siddiqui AM, Ahmed F (2014) Chaotic substitution for highly autocorrelated data in encryption algorithm. Commun Nonlinear Sci Numer Simul 19 (9):3106–3118
Ashtiyani M, Birgani PM, Hosseini HM (2008) Chaos-based medical image encryption using symmetric cryptography. In: 3rd international conference on information and communication technologies: from theory to applications, 2008. ICTTA 2008. IEEE, pp 1–5
Askar S, Karawia A, Alshamrani A (2015) Image encryption algorithm based on chaotic economic model. Mathematical Problems in Engineering
Ahmed F, Anees A, Abbas VU, Siyal M (2014) A noisy channel tolerant image encryption scheme. Wirel Pers Commun 77(4):2771–2791
Behnia S, Akhshani A, Mahmodi H, Akhavan A (2008) A novel algorithm for image encryption based on mixture of chaotic maps. Chaos, Solitons & Fractals 35(2):408–419
Chen G., Mao Y, Chui CK (2004) A symmetric image encryption scheme based on 3d chaotic cat maps. Chaos, Solitons Fractals 21(3):749–761
Chen J-X, Zhu Z-L, Fu C, Zhang L-B, Zhang Y (2014) Cryptanalysis and improvement of an optical image encryption scheme using a chaotic baker map and double random phase encoding. J Opt 16(12):125403
Chen J -x, Zhu Z -l, Fu C, Zhang L -b, Zhang Y (2014) An image encryption scheme using nonlinear inter-pixel computing and swapping based permutation approach, Communications in Nonlinear Science and Numerical Simulation
Elashry IF, Allah OSF, Abbas AM, El-Rabaie S, El-Samie FEA (2009) Homomorphic image encryption. J Electron Imaging 18(3):033002–033002
El-lskandarani M, Darwish S, Abuguba S (2008) A robust and secure scheme for image transmission over wireless channels. In: 42nd Annual IEEE international Carnahan conference on security technology, ICCST 2008, pp 51–55. IEEE
Fridrich J (1998) Symmetric ciphers based on two-dimensional chaotic maps. Int J Bifurcation Chaos 8(06):1259–1284
Fu-lai W (2010) A universal algorithm to generate pseudo-random numbers based on uniform mapping as homeomorphism. Chinese Physics B 19(9):090505
Gao H, Zhang Y, Liang S, Li D (2006) A new chaotic algorithm for image encryption. Chaos, Solitons Fractals 29(2):393–399
Hasler M, Maistrenko YL (1997) An introduction to the synchronization of chaotic systems: coupled skew tent maps. IEEE Trans Circuits Syst I, Fundam Theory Appl 44(10):856–866
Hu Y, Zhu C, Wang Z (2014) An improved piecewise linear chaotic map based image encryption algorithm. Sci World J 2014
Huang R, Rhee K, Uchida S (2012) A parallel image encryption method based on compressive sensing. Multimedia Tools and Applications:1–23
Hussain I, Shah T, GondalMA (2013) Application of s-box and chaotic map for image encryption. Math Comput Model 57(9):2576–2579
Kanso A, Ghebleh M (2015) An efficient and robust image encryption scheme for medical applications. Commun Nonlinear Sci Numer Simul 24(1):98–116
Khan MK, Kumari S (2014) Cryptanalysis and improvement of an efficient and secure dynamic id-based authentication scheme for telecare medical information systems. Security and Communication Networks 7(2):399–408
Kun Z, Xing-an F (2012) Color image encryption algorithm based on tangent-delay ellipse reflecting cavity map system. In: 2012 International conference on image analysis and signal processing (IASP). IEEE, pp 1–4
Li C, Xie T, Liu Q, Cheng G (2014) Cryptanalyzing image encryption using chaotic logistic map. Nonlinear Dyn 78(2):1545–1551
Lian S, Sun J, Wang Z (2005) Security analysis of a chaos-based image encryption algorithm. Physica A: Statistical Mechanics and its Applications 351(2):645–661
Lian S, Sun J, Wang Z (2005) A block cipher based on a suitable use of the chaotic standard map. Chaos, Solitons Fractals 26(1):117–129
Liu H, Wang X (2010) Color image encryption based on one-time keys and robust chaotic maps. Comput Math Appl 59(10):3320–3327
Liu H, Wang X (2013) Triple-image encryption scheme based on one-time key stream generated by chaos and plain images. J Syst Softw 86(3):826–834
Li-Yuan S, Li-Ling C, Ke-Hui S, Jiang W (2005) Pseudo-random number generator based on td-ercs chaos and its statistic characteristics analysis. Acta Phys Sin 54(9):4031–4037
Li-Yuan S, Ke-Hui S, Chuan-Bing L (2004) Study of a discrete chaotic system based on tangent-delay for elliptic reflecting cavity and its properties. Acta Phys Sin 53(9):2871–4037
Mao Y, Chen G, Lian S (2004) A novel fast image encryption scheme based on 3d chaotic baker maps. International Journal of Bifurcation and Chaos 14(10):3613–3624
Norouzi B, Seyedzadeh SM, Mirzakuchaki S, Mosavi M R (2013) A novel image encryption based on row-column, masking and main diffusion processes with hyper chaos, Multimedia Tools and Applications
Pisarchik A, Zanin M (2008) Image encryption with chaotically coupled chaotic maps. Physica D: Nonlinear Phenomena 237(20):2638–2648
Shannon C E (1949) Communication theory of secrecy systems*. Bell System Technical Journal 28(4):656–715
Tang Z, Zhang X, Lan W (2014) Efficient image encryption with block shuffling and chaotic map. Multimedia Tools and Applications, pp 1–20
Tran M-T, Bui DK, Duong AD (2008) Gray S-Box for advanced encryption standard. In: International conference on computational intelligence and security, 2008. CIS’08. IEEE, vol 1, pp 253–258
Wang X-Y, Gu S-X, Zhang Y-Q (2015) Novel image encryption algorithm based on cycle shift and chaotic system. Opt Lasers Eng 68:126–134
Wang Y, Wong K-W, Liao X, Chen G (2011) A new chaos-based fast image encryption algorithm. Appl Soft Comput 11(1):514–522
Yang Y-G, Pan Q-X, Sun S-J, Xu P (2015) Novel image encryption based on quantum walks. Sci Report 5
Ye C, Xiong Z, Ding Y, Zhang X, Wang G, Xu F (2015) Joint fingerprinting/encryption for medical image security. International Journal of Security and Its Applications 9(1):409–418
Zaibi G, Peyrard F, Kachouri A, Fournier-Prunaret D, Samet M (2014) Efficient and secure chaotic s-box for wireless sensor network. Security and Communication Networks 7(2):279–292
Zhang K, Fang J-b (2015) Color image encryption algorithm based on td-ercs system and wavelet neural network. Mathematical problems in engineering
Zhao J, Wang S, Chang Y, Li X (2015) A novel image encryption scheme based on an improper fractional-order chaotic system. Nonlinear Dyn 80(4):1721–1729
Zhang Y, Wen W, Su M, Li M (2014) Cryptanalyzing a novel image fusion encryption algorithm based on dna sequence operation and hyper-chaotic system. Optik-International Journal for Light and Electron Optics 125(4):1562–1564
Zhang Y, Xiao D, Wen W, Nan H (2014) Cryptanalysis of image scrambling based on chaotic sequences and vigenère cipher. Nonlinear Dyn 78(1):235–240
Zhang L-B, Zhu Z-L, Yang B-Q, Liu W-Y, Zhu H-F, Zou M-Y (2015) Cryptanalysis and improvement of an efficient and secure medical image protection scheme. Mathematical Problems in Engineering, vol 2015
Zhu C (2012) A novel image encryption scheme based on improved hyperchaotic sequences. Opt Commun 285(1):29–37
Acknowledgments
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (2014R1A1A2054174). This research was also supported by the MSIP (Ministry of Science, ICT and Future Planning), Korea, under the Global IT Talent support program (NIPA-2014-H0905-14-1004) supervised by the NIPA (National IT Industry Promotion Agency).
Author information
Authors and Affiliations
Corresponding author
Electronic supplementary material
Below is the link to the electronic supplementary material.
Rights and permissions
About this article
Cite this article
Ahmad, J., Hwang, S.O. A secure image encryption scheme based on chaotic maps and affine transformation. Multimed Tools Appl 75, 13951–13976 (2016). https://doi.org/10.1007/s11042-015-2973-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-015-2973-y