Abstract
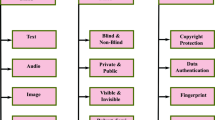
This paper describes security and privacy issues for multimedia database management systems. Multimedia data includes text, images, audio and video. It describes access control for multimedia database management systems and describes security policies and security architectures for such systems. Privacy problems that result from multimedia data mining are also discussed.
Similar content being viewed by others
References
Agrawal R, Srikant R (2000) Privacy-preserving data mining. In: Proceedings of the ACM SIGMOD Conference, Dallas, TX, May
Banerjee J et al (1987) A data model for object-oriented applications. ACM Trans Off Inf Sys, pp. 3–26, April
Berners Lee T et al The semantic web. Sci Am, pp. 28–37, May
Bertino E, Ferrari E, Squicciarini AC (2003) X-TNL: An XML-based language for trust negotiations. Proceedings of the IEEE POLICY Workshop, Lake Como, Italy
Bertino E et al (2004) Secure third party publishing of XML documents. IEEE Trans Knowl Data Eng, pp. 1263–1278, October
Clifton C et al (2002) Defining privacy for data mining. In: Next Generation Data Mining Workshop, Baltimore, MD, November
Dobra A et al (2002) Processing complex aggregate queries over data streams. In: Proceedings of the 2002 ACM Sigmod international conference on management of data, Madison, WI, June
Evfimievski A et al (2002) Privacy preserving mining of association rules. In: Proceedings of the eighth ACM SIGKDD international conference on knowledge discovery and data mining. Edmonton, Alberta, Canada, July
Ferrari E, Thuraisingham B (2000) Database security, Artech House, October (editors: M. Piattini and O. Diaz), pp. 160–180
Gehrke J (2002) Research problems in data stream processing and privacy-preserving data mining. In: Proceedings of the next generation data mining workshop, Baltimore, MD, November
Thuraisingham N (ed) (1996) Proceedings of the 1st IEEE Metadata Conference. Silver Spring, MD, April
Ghosh A (1998) E-Commerce Security: weak links, best defenses. John Wiley, Mississauga, Ontario, Cananda
Perrig A et al (2003) SIA: secure information aggregation in sensor networks. Technical report, Carnegie Melon University, April
Prabhakaran B (1997) Multimedia database systems. Kluwer, MA, June
Berra B, Nowsu K, Thuraisingham B (eds) (1994) Proceedings of the ACM multimedia conference workshop on multimedia database management systems, San Francisco, CA, October 1994
Bayard H, Lavander B, Kerchner M, Thuraisingham B, Zemankova M (eds) (1994) Proceedings of the massive digital data systems workshop. Community Management Staff, Washington D.C., February 1994
Ghafoor A, Little T (eds) (1993) Special issue on multimedia database systems. IEEE Trans Knowl Data Eng, April 1993
SQL3 (1992) American National Standards Institute, Draft, December
Thuraisingham B (1990) Multilevel security for multimedia database systems. In: Proceedings of the IFIP database security conference, Halifax, UK, September
Thuraisingham B (1994) Security issues for federated database management. Computers and Security, December
Thuraisingham B (1998) Data mining: technologies, techniques, tools and trends. CRC, December
Thuraisingham B (2001) Managing and mining multimedia databases. CRC, June
Thuraisingham B (2002) Data and applications security: developments and directions. In: Proceedings of the IEEE COMPSAC conference, Oxford, UK, August
Thuraisingham B (2003) Data mining, national security, privacy and civil liberties, SIGKDD Explorations, January
Thuraisingham B (2003) Management and mining multimedia databases. International Journal of Tools in Artificial Intelligence, volume 13, September 2004, pp. 730–749
Thuraisingham B (2003) Privacy constraints processing in a privacy enhanced database management system. Data Knowl Eng (in press)
Thuraisingham B (2003) Web data mining technologies and their applications to business intelligence and counter-terrorism. CRC, June
Thuraisingham B (2004) Database and applications security: integrating data management and applications security. CRC, December
Thuraisingham B (2005) Secure sensor information management. IEEE Signal Process Mag, pp. 14–19, May
Thuraisingham B, Ford W (1995) Security constraint processing in a distributed database management system. IEEE Trans Knowl Data Eng, pp. 274–293, April
Thuraisingham B, Maurer J (1999) Survivability of real-time command and control systems. IEEE Trans Knowl Data Eng, pp. 228–238, January
Thuraisingham B et al (1993) Design and implementation of a database inference controller. Data Knowl Eng, pp. 271–288, December
Woelk D et al (1986) An object-oriented approach to multimedia databases. In: Proceedings of the ACM SIGMOD conference, Washington DC, June
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Thuraisingham, B. Security and privacy for multimedia database management systems. Multimed Tools Appl 33, 13–29 (2007). https://doi.org/10.1007/s11042-006-0096-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-006-0096-1