Abstract
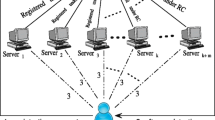
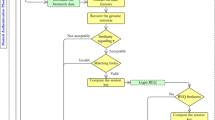
Connected health care provides new opportunities for improving financial and clinical performance. Many connected health care applications such as telecare medicine information system, personally controlled health records system, and patient monitoring have been proposed. Correct and quality care is the goal of connected heath care, and user authentication can ensure the legality of patients. After reviewing authentication schemes for connected health care applications, we find that many of them cannot protect patient privacy such that others can trace users/patients by the transmitted data. And the verification tokens used by these authentication schemes to authenticate users or servers are only password, smart card and RFID tag. Actually, these verification tokens are not unique and easy to copy. On the other hand, biometric characteristics, such as iris, face, voiceprint, fingerprint and so on, are unique, easy to be verified, and hard to be copied. In this paper, a biometrics-based user authentication scheme will be proposed to ensure uniqueness and anonymity at the same time. With the proposed scheme, only the legal user/patient himself/herself can access the remote server, and no one can trace him/her according to transmitted data.


Similar content being viewed by others
References
Wu, Z. Y., Lee, Y. C., Lai, F., Lee, H. C., and Chung, Y., A secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1529–1535, 2012.
Wei, J., Hu, X., and Liu, W., An improved authentication scheme for telecare medicine information systems. J Med Syst. doi: 10.1007/s10916-012-9835-1, 2012.
Debiao, H., Jianhua, C., and Rui, Z., A more secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1989–1995, 2012.
Pu, Q., Wang, J., and Zhao, R., Strong authentication scheme for telecare medicine information systems. J. Med. Syst. 36(4):2609–2619, 2012.
Chien, H. Y., Yang, C. C., Wu, T. C., and Lee, C. F., Two RFID-based solutions to enhance inpatient medication safety. J. Med. Syst. 35(3):369–375, 2011.
Huang, C., Lee, H., and Lee, D. H., A privacy-strengthened scheme for E-healthcare monitoring system. J. Med. Syst. 36(5):2959–2971, 2012.
Chen, C. L., and Wu, C. Y., Using RFID yoking proof protocol to enhance inpatient medication safety. J. Med. Syst. 36(5):2849–2864, 2012.
Lamport, L., Password authentication with insecure communication. Comm. ACM. 24(11):770–772, 1981.
Hwang, M. S., and Li, L. H., A new remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 46(1):28–30, 2000.
Fan, C. I., Chang, Y. C., and Zhang, Z. K., Robust remote authentication scheme with smart cards. Comput. Secur. 24(8):619–628, 2005.
Chang, Y. F., Chang, C. C., and Kuo, J. Y., A secure one-time password authentication scheme using smart cards without limiting login times. ACM SIGOPS Oper Syst Rev 38(3):80–90, 2004.
Burnett, A., Byrne, F., Dowling, T., and Duffy, A., A biometric identity based signature scheme. Int. J. Netw. Secur. 5(3):317–326, 2006.
Lee, J. S., Chang, Y. F., and Chang, C. C., A novel authentication protocol for multi-server architecture without smart cards. Int. J. Innov. Comput. I. 4(6):1357–1364, 2008.
Jain, A. Nandakumar, K., K., and Nagar, A., Biometric temple security. EURASIP J Adv Sig Pr 2008(113), 2008.
Lee, J. K., Ryu, S. R., and Yoo, K. Y., Fingerprint-based remote user authentication scheme using smart cards. Electron. Lett. 38(12):554–555, 2002.
Lin, C. H., and Lai, Y. Y., A flexible biometrics remote user authentication scheme. Comput. Stand. Inter. 27(1):19–23, 2004.
Chang, C. C., and Lin, I. C., Remarks on fingerprint-based remote user authentication scheme using smart cards. ACM SIGOPS Oper Syst Rev 38(4):91–96, 2004.
Kim, H. S., Lee, S. W., and Yoo, K. Y., ID-based password authentication scheme using smart cards and fingerprints. ACM SIGOPS Oper Syst Rev 37(4):32–41, 2003.
Scott, M., Cryptanalysis of an ID-based password authentication scheme using smart cards and fingerprints. ACM SIGOPS Oper Syst Rev 38(2):73–75, 2004.
Li, C. T., and Hwang, M. S., An efficient biometrics-based remote user authentication scheme using smart cards. J. Netw. Comput. Appl. 33(1):1–5, 2010.
Jin, A. T. B., Ling, D. N., and Goh, A., Biohashing: Two factor authentication featuring fingerprint data and tokenised random number. Pattern. Recogn. 37(11):2245–2255, 2004.
Lumini, A., and Nanni, L., An improved BioHashing for human authentication. Pattern. Recogn. 40(3):1057–1065, 2007.
Wang, R. C., Juang, W. S., and Lei, C. L., A simple and efficient key exchange scheme against the smart card loss problem. The 2007 IFIP Int. Conf. on Embedded and Ubiquitous Computing 4809:728–744, 2007.
Teoh, A. B. J., Goh, A., and Ngo, D. C. L., Random multispace quantization as an analytic mechanism for BioHashing of biometric and random identity inputs. IEEE T Pattern Anal 28:1892–1901, 2006.
Nagar, A., Nandakumar, K., and Jain, A. K., Biometric template transformation: a security analysis. Proc. of Media Forensics and Security, San Jose, 2010.
Acknowledgments
This work was supported in part by National Science Council under the grants NSC 99-2410-H-025-010-MY2 and NSC 101-2410-H-025 -009 -MY2.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chang, YF., Yu, SH. & Shiao, DR. A Uniqueness-and-Anonymity-Preserving Remote User Authentication Scheme for Connected Health Care. J Med Syst 37, 9902 (2013). https://doi.org/10.1007/s10916-012-9902-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-012-9902-7