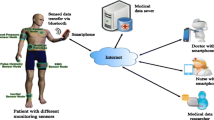
Abstract
Mobile health (m-Health) system architectures are typically based on mobile and wireless communications, and use mobile devices with data exchange supported by Web services (WS). Although m-Health systems offer mobility as a potential and precious resource they also present several challenged issues and constraints, such as, battery and storage capacity, broadcast constraints, interferences, disconnections, noises, limited bandwidths, and network delays. Furthermore, constant mobility and often-required Internet connectivity also exposes and compromises the privacy and confidentiality of the m-Health system information. This paper proposes a novel data encryption solution for mobile health systems, considering a novel and early-proposed cooperation strategy. This encryption solution, tries to guarantee the best confidentiality, integrity, and authenticity of m-Health systems users data. The paper also presents a performance evaluation study comparing the performance an m-Health application with and without the DE4MHA.
















Similar content being viewed by others
References
Akter, S., D’Ambra, J., & Ray, P. (2010). User perceived service quality of mHealth services in developing countries. In European conference on information systems (ECIS 2010), South Africa, June 6–9, 2010 (pp 1–12).
Akter, S., & Ray, P. (2010). mHealth—An ultimate platform to serve the unserved. IMIA yearbook of medical informatics—Biomedical informatics: Building capacity worldwide (pp. 94–100). Stuttgart: Schattauer.
Antoniou, G., & Batten, L. (2011). e-Commerce: Protecting purchaser privacy to enforce trust. Electronic Commerce Research, 11(4), 421–456.
Agrawal, M., & Mishra, P. (2012). A comparative survey on symmetric key encryption techniques. International Journal on Computer Science and Engineering, 4, 877–882.
Bannon, L., & Hughes, J. (1993). The context of CSCW. In K. Schmidt (Ed.), Report of COST14 “CoTech”. Working Group 4 (1991–1992).
Batten, L. (2013). Public key cryptography. Hoboken: Wiley.
Biryukov, A., Nakahara, J., Preneel, B., & Vandewalle, J. (2002). New weak key classes of IDEA. Lecture Notes in Computer Science (Vol. 2513, pp. 315–326).
Biswas, G. (2008). Diffie–Hellman technique: Extended to multiple two-party keys and one multi-party key. IET Information Security, 2(1), 12–18.
Bleumer, G. (1994). Security for decentralized health information systems. International Journal of Bio-Medical Computing, 35, 139–145.
Boonyarattaphan, A., Bai, Y., Chung, S. (2009). A security framework for e-Health service authentication and e-Health data transmission. In 9th international symposium on communications and information technology (ISCIT 2009), September 28–29 (pp. 1213–1218).
Buttyán, L., & Hubaux, J.-P. (2003). Stimulating cooperation in self-organizing mobile ad hoc networks. Mobile Networks and Applications, 8(5), 579–592.
Chan, V., Ray, P., & Parameswaran, N. (2008). Mobile e-Health monitoring: An agent-based approach. IET Communications, 2(2), 223–230.
Chang, H. (2013). The security service rating design for IT convergence services. Electronic Commerce Research. https://doi.org/10.1007/s10660-013-9115-2.
Chen, Y., & Ku, W. (2009). Self-encryption scheme for data security in mobile devices. In Proceedings of the 6th IEEE conference on consumer communications and networking conference (pp. 850–854).
Cochran, M. (2008). Cryptographic hash functions. Ann Arbor: ProQuest.
Cubic, I., Markota, I., & Benc, I. (2010). Application of session initiation protocol in mobile health systems. In Proceedings of the 33rd international convention MIPRO. Opatija, Croatia, May 24–28 (pp. 367–371).
Déglise, C., Suggs, L., & Odermatt, P. (2012). Short message service (SMS) applications for disease prevention in developing countries. Journal of Medical Internet Research, 14(1), e3. http://www.jmir.org/2012/1/e3/.
Diffie, W. (1988). The first ten years of public-key cryptography. Proceedings of the IEEE, 76(5), 560–577.
Eastlake, D., & Jones, P. (2001). US secure hash algorithm 1. http://www.ietf.org/rfc/rfc3174.txt. Accessed 12 January 2013.
Elgamal, T. (1985). A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Transactions on Information Theory, 31(4), 469–472.
Fayn, J., & Rubel, P. (2010). Towards a personal health society in cardiology. IEEE Transactions on Information Technology in Biomedicine, 14(2), 401–409.
Federal Information Processing Standards Publication. (2013). Data encryption standard (DES). http://www.itl.nist.gov/fipspubs/fip46-2.htm. Accessed 12 January 2013.
Ferguson, N., Schneier, B., & Kohno, T. (2012). Cryptography engineering. Hoboken: Wiley. ISBN 978-0-470-47424-2.
Goldreich, O. (2005). Foundations of cryptography. Hanover: Now Publishers Inc.
Gritzalis, S., Zhan, J. Z., & Jeong, K. (2013). IT convergence and security. Electronic Commerce Research. https://doi.org/10.1007/s10660-013-9114-3.
Gupta, A. (2008). Challenges of mobile computing. In Proceedings of 2nd national conference on challenges and opportunities in information technology, March 29 (pp. 86–90).
Housley, R. (2001). Triple-DES and RC2 key wrapping. http://www.ietf.org/rfc/rfc3217.txt. Accessed 12 January 2013.
Istepanian, R., & Lacal, J. (2003). Emerging mobile communication technologies for health: Some imperative notes on m-Health. In Proceedings of the 25th annual international conference of the IEEE Engineering in Medicine and Biology Society (Vol. 2, pp. 1414–1416).
Isaac, J. T., Zeadally, S., & Cámara, J. S. (2012). A lightweight secure mobile payment protocol for vehicular ad-hoc networks (VANETs). Electronic Commerce Research, 12(1), 97–123.
Jaganathan, K., Zhu, L., & Brezak, J. (2006). The RC4-HMAC Kerberos Encryption Types. http://tools.ietf.org/html/rfc4757/. Accessed 12 January 2013.
Jara, A., Zamora, M., & Skarmeta, A. (2011). An Internet of things-based personal device for diabetes therapy management in ambient assisted living (AAL). Personal and Ubiquitous Computing, 15(4), 431–440.
Jonsson, J., & Kaliski, B. (2003). Public-key cryptography standards (PKCS) #1: RSA cryptography specifications version 2.1. http://tools.ietf.org/html/rfc3447. Accessed 12 January 2013.
Kramer, G., Maric, I., & Yates, R. D. (2007). Cooperative communications (foundations and trends in networking). Hanover: Now Publishers Inc.
Kollmann, A., Riedl, M., Kastner, P., Schreier, G., & Ludvik, B. (2007). Feasibility of a mobile phone-based data service for functional insulin treatment of type 1 diabetes mellitus patients. Journal of Medical Internet Research, 9(5) e36. http://www.jmir.org/2007/5/e36/.
Koukopoulos, D., & Styliaras, G. (2013). Design of trustworthy smartphone-based multimedia services in cultural environments. Electronic Commerce Research, 13(2), 129–150.
Lacuesta, R., Lloret, J., Garcia, M., & Peñalver, L. (2013). A secure protocol for spontaneous wireless ad hoc networks creation. IEEE Transactions on Parallel and Distributed Systems, 24(4), 629–664. https://doi.org/10.1109/TPDS.2012.168.
Laxminarayan, S., Istepanian, R., & Pattichis, C. S. (2006). m-Health: Emerging mobile health systems. Berlin: Springer.
Lin, C. T., Chang, K. C., Lin, C. L., Chiang, C. C., Lu, S. W., Chang, S. S., et al. (2010). An intelligent telecardiology system using a wearable and wireless ECG to detect atrial fibrillation. IEEE Transactions on Information Technology in Biomedicine, 14(3), 726–733.
Martin, K. (2012). Everyday cryptography. Oxford: OUP.
Moullee, B., & Ray, P. (2009). Issues in e-Health cost impact assessment. In IFMBE proceeding of the world congress on medical physics and biomedical engineering (pp. 223–226). Berlin: Springer.
Mougiakakou, S., Bartsocas, C., Bozas, E., Chaniotakis, N., Iliopoulou, D., Kouris, I., et al. (2010). SMARTDIAB: A communication and information technology approach for the intelligent monitoring, management and follow-up of type 1 diabetes patients. IEEE Transactions on Information Technology in Biomedicine, 14(3), 622–633.
Paar, C., & Pelzl, J. (2010). The data encryption standard (DES) and alternatives. Understanding cryptography. A textbook for students and practitioners (pp. 55–86). Berlin: Springer.
Pachghare, V. K. (2009). Cryptography and information security. New Delhi: PHI Learning Pvt. Ltd. ISBN 978-81-203-3521-9.
Pare, G., Moqadem, K., Pineau, G., & St-Hilaire, C. (2010). Clinical effects of home telemonitoring in the context of diabetes, asthma, heart failure and hypertension: a systematic review. Journal of Medical Internet Research, 12(2), e21. http://www.jmir.org/2010/2/e21/.
Patrick, K., Raab, F., Adams, M., Dillon, L., Zabinski, M., Rock, C., Griswold, W., & Norman, G. (2009). A text message-based intervention for weight loss: Randomized controlled trial. Journal of Medical Internet Research, 11(1), e1. http://www.jmir.org/article/citations/1100.
Pollak, J., Gay, G., Byrne, S., Wagner, E., Retelny, D., & Humphreys, L. (2010). It’s time to eat! Using mobile games to promote healthy eating. IEEE Pervasive Computing, 9(2), 21–27.
Qiang, Z., & Yamamichi, M. (2012). Mobile applications for the health sector. http://siteresources.worldbank.org/INFORMATIONANDCOMMUNICATIONANDTECHNOLOGIES/Resources/mHealth_report.pdf. Accessed 12 January 2013.
Raeburn, K. (2005) Advanced encryption standard (AES) Encryption for Kerberos 5. http://www.ietf.org/rfc/rfc3962.txt. Accessed 12 January 2013.
Ray, P., Parameswaran, N., Chan, V., & Yu, W. (2008). Awareness modeling in collaborative mobile e-Health. Journal of Telemedine and Telecare, 14(7), 381–385.
Raychaudhuri, K., & Ray, P. (2010). Privacy challenges in the use of eHealth systems for public health management. International Journal of e-Health and Medical Communications, 1(2), 12–23.
Rivest, R. (1992). The MD5 message-digest algorithm. http://www.ietf.org/rfc/rfc1321.txt. Accessed 12 January 2013.
Rodrigues, J., Oliveira, M., & Vaidya, B. (2010). New trends on ubiquitous mobile multimedia applications. EURASIP Journal on Wireless Communications and Networking, 2010(10), 1–12.
Rodrigues, J., Lopes, I., Silva, B., & Torre, I. (2013). A new mobile ubiquitous computing application to control obesity: SapoFit. Informatics for Health and Social Care, 38(1), 37–53.
SapoFit. (2013). http://itunes.apple.com/pt/app/sapo-fit/id438487775?mt=8. Accessed 12 January 2013.
Schneier, B. (1994). The Blowfish encryption algorithm. Dr Dobb’s Journal-Software Tools for the Professional Programmer, 19(4), 38–43.
Schneier, B. (1996). Applied cryptography: Protocols, algorithms, and source code in C. New York: Wiley.
Shanmugam, M., Thiruvengadam, S., Khurat, A., & Maglogiannis, I. (2006). Enabling secure mobile access for electronic health care applications. In Pervasive health conference and workshops, Innsbruck, Austria, November 29 to December 1 (pp. 1–8).
Silva, B. M. C., Rodrigues, J. J. P. C., Lopes, I. M. C., Machado, T. M. F., & Zhou, L. (2013). A novel cooperation strategy for mobile health applications. IEEE Journal on Selected Areas in Communications (JSAC), Special Issue on Emerging Technologies in Communications - eHealth, IEEE Communications Society, 31(9), 28–36. https://doi.org/10.1109/JSAC.2013.SUP.0513003.
Silva, B., Lopes, I., Rodrigues, J., & Ray, P. (2011). SapoFitness: A mobile health application for dietary evaluation. In 13th IEEE international conference on e-Health networking applications and services (Healthcom 2011), Columbia, Missouri, USA, June 13–15 (pp. 375–380).
Smith, R. (2005). Introduction to multilevel security. Handbook of information security. Hoboken: Wiley.
Sulaiman, R., Sharma, D., Ma, W., & Tran, D. (2008). A security architecture for e-Health services. In 10th international conference on advanced communication technology, Gangwon-Do, South Korea (Vol. 2, pp. 99–104).
Tachakra, S., Wang, X., Istepanian, R., & Song, Y. (2003). Mobile e-Health: The unwired evolution of telemedicine. Telemedicine Journal and e-Health, 9(3), 247–257.
Tillich, S., & Herbst, C. (2008). Attacking state-of-the-art software countermeasures—A case study for AES. In Proceedings of the 10th international workshop on cryptographic hardware and embedded systems, Washington, DC, USA, August 10–13 (pp. 228–243).
Watson, A., Bickmore, T., Cange, A., Kulshreshtha, A., & Kvedar, J. (2012). An internet-based virtual coach to promote physical activity adherence in overweight adults: randomized controlled trial. Journal of Medical Internet Research, 14(1), e1. http://www.jmir.org/2012/1/e1/.
Whittaker, R., Dorey, E., Bramley, D., Bullen, C., Denny, S., & Elley, C., et al. (2011). A theory-based video messaging mobile phone intervention for smoking cessation: randomized controlled trial. Journal of Medical Internet Research, 13(1), 1–12. http://www.jmir.org/2011/1/e10/.
Yong-Xia, Z., & Ge, Z. (2010). MD5 research. In Second international conference on multimedia and information technology, Kaifeng, China, April 24–25 (Vol. 2, pp. 271–273).
Zheng, P., & Ni, L. (2005). Smart phone and next generation mobile computing. San Francisco: Morgan Kaufmann.
Zhu, F., Bosch, M., Woo, I., Kim, S., Boushey, C., Ebert, D., et al. (2010). The use of mobile devices in aiding dietary assessment and evaluation. IEEE Journal of Selected Topics in Signal Processing, 4(4), 756–766.
Acknowledgements
This work has been partially supported by National Funding from the FCT - Fundação para a Ciência e a Tecnologia through the PEst-OE/EEI/LA0008/2013 Project; by the AAL4ALL (Ambient Assisted Living for All), project co-funded by COMPETE under FEDER via QREN Programme; by Brazilian National Council for Research and Development (CNPq) via Grant No. 309335/2017-5; and by FINEP, with resources from Funttel, Grant No. 01.14.0231.00, under the Centro de Referência em Radiocomunicações - CRR project of the Instituto Nacional de Telecomunicações (Inatel), Brazil.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Silva, B.M.C., Rodrigues, J.J.P.C., Canelo, F. et al. Towards a cooperative security system for mobile-health applications. Electron Commer Res 19, 629–654 (2019). https://doi.org/10.1007/s10660-018-9296-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10660-018-9296-9