Abstract
In recent times, energy related issues have become challenging with the increasing size of data centers. Energy related issues problems are becoming more and more serious with the growing size of data centers. Green cloud computing (GCC) becomes a recent computing platform which aimed to handle energy utilization in cloud data centers. Load balancing is generally employed to optimize resource usage, throughput, and delay. Aiming at the reduction of energy utilization at the data centers of GCC, this paper designs an energy efficient resource scheduling using Cultural emperor penguin optimizer (CEPO) algorithm, called EERS-CEPO in GCC environment. The proposed model is aimed to distribute work load amongst several data centers or other resources and thereby avoiding overload of individual resources. The CEPO algorithm is designed based on the fusion of cultural algorithm (CA) and emperor penguin optimizer (EPO), which boosts the exploitation capabilities of EPO algorithm using the CA, shows the novelty of the work. The EERS-CEPO algorithm has derived a fitness function to optimally schedule the resources in data centers, minimize the operational and maintenance cost of the GCC, and thereby decrease the energy utilization and heat generation. To ensure the improvised performance of the EERS-CEPO algorithm, a wide range of experiments is performed and the experimental outcomes highlighted the better performance over the recent state of art techniques.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
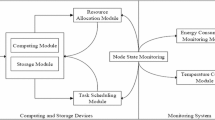
Cloud computing (CC), a sub-region of ICT, is the research topic on the environment. There are views and arguments against and for this technology. Excepting the interests shown by the provider of cloud type services and products [1, 2], there is significant pressure from the government organization for reducing negative effects on the environments. The growth of Green Cloud Computing (GCC) is highly associated with the development of green datacentres since the data centers are the essence of the CC environment. As [3] the power expended by the datacentres in 2010 was 1.3% of the overall consumptions. The study reported by GeSI [4], i.e., deliberated “one of the well-recognized and most comprehensive snapshots of the Internet power demands around the world”, evaluates a rise in the share of overall carbon dioxide (CO2) emissions from ICT from 1.3% of global emission in 2002 to 2.3% in 2020. Using power utilization and CC environment, a set of authors at Lawrence Berkeley National Laboratory and North-western University proposed a modelling equipment named the Cloud Energy and Emissions Research Model (CLEER). Such server’s farm creates the cloud. The result estimates that the productivity software and Customer Relationship Management software, primary energy footprint of email could be minimized as 87% when each business user in the US moved to CC platform [5]. Also when the model doesn’t consider each variable, it could demonstrate beneficial as a result energetic efficacy in the datacentres that belong to Internet Company. It can guarantee a rise in energetic transparency and notify consumers for enabling them to select a better offer. The advantages of CC environment are very important for environmental protection when datacentres are based on green computing principles. Figure 1 depicts the task scheduling (TS) process in GCC.
Datacentre consumes around 1.3% of the overall global electrical energy supplies, i.e., anticipated to rise up to 8% in 2020 [6, 7]. Hence, CO2 significantly increases that directly impacts the environment. Unfortunately, huge amount of electricity is exhausted by the server at the time of lower task [8]. The Quality of Service (QoS) constraints play a significant role among users and mobile cloud service provider. Hence, the major problem is to minimalize energy utilization of mobile cloud datacentres when fulfilling QoS requirement [9]. The hardware virtualization technologies transform conventional hardware into a novel model. Such technologies consolidate tasks, named virtual machine (VM) consolidation, and exploit lower power hardware state. One of the present researches has minimalized the total power consumptions via 2 commonly employed methods like dynamic server provisioning and VM consolidation. Dynamic server provisioning method reduces energy utilization by decreasing the computation resource at the time of lower tasks [10]. These reductions mean turning the redundant server to sleep mode while the task demands decrease. Likewise, while data storage demand and processing increase, this server is reactivate based on the requirement. The servers share its resource amongst many efficiently isolated environments named VM with the help of hypervisor technique.
Resource utilization in cloud is based on the sequence and type of resources and tasks. Workflow technology is employed for handling data-intensive applications, increasing complex data, analysis, and simulations. Also, this technology is employed for scheduling computation tasks on allocated resources, for managing dependencies between tasks and stage datasets to and out of implementation site. This workflow is applied for modelling computation in various fields. Several TS algorithms are presented in this study, i.e., mainly categorized to Level-by-level scheduling, list scheduling algorithm, duplication based scheduling, batch scheduling, batch dependency scheduling technique, dependency scheduling, hybrid algorithm and Genetic Algorithm (GA) based scheduling technique. List scheduling algorithms create a list of tasks when accounting task dependencies. The task in the lists is treated for their existence in the task list. The efficacy of these algorithms is relatively better compared to other classifications of techniques. Level-by-level scheduling algorithm considers task of single level in task graph thus the task deliberated are independent of one another.
This paper presents an energy efficient resource scheduling using Cultural emperor penguin optimizer (CEPO) algorithm, called EERS-CEPO in GCC environment. The CEPO algorithm incorporates the cultural algorithm (CA) into emperor penguin optimizer (EPO) in order to boost the exploitation capabilities of EPO algorithm. The EERS-CEPO algorithm has derived a fitness function for optimal resource scheduling in data centers, minimize the operational and maintenance cost of the GCC, and thereby decreases the energy utilization and heat generation. To ensure the improvised performance of the EERS-CEPO algorithm, a wide range of experiments is performed.
2 Literature review
Zong [11] integrates GA and ACO algorithms for proposing a dynamic fusion TS approach. Thus decreasing the power utilization of computing centres and CC datacentres. The experimental result shows that the presented method could considerably decrease the time and overall power utilization of CC systems. Jena [12] focus on TSCSA method for optimizing processing and energy time. The results attained using TSCSA technique were inspired by a public domain source cloud environment (CloudSim). Lastly, the outcomes are related to the present scheduling algorithm and establish that the presented method offers an optimum balance result for many objectives.
Thaman and Singh [13] proposed a strong hybrid planning approach, RHEFT method to bind tasks for VM. The distribution of tasks to VM is depending upon a new task matching approach named Interior Scheduling. Yuan et al. [14] presented an STSRO approach for minimizing the overall cost of their providers by cost-efficiently scheduling each incoming task of heterogeneous application for meeting task’ delay-bound limitations. STSRO approach exploits spatial diversity in DGCDC. In every time slot, the cost reduction problems for DGCDC are created as a constraint optimization one and resolved by the presented SBA approach.
Ranjan et al. [15] proposed a GCTA method on the basis of enhanced BPSO algorithm. The major contributions of this study are to avoid matrix operation with the help of pipelined amounts for VMs and re-determining the velocity and position of particles. Experimental results show that the presented method has lesser implementation time, and decreases resource utilization consequently. Yuan et al. [16] consider the trade-offs among energy cost minimization and profit maximization for the GCDC provider when encountering the delay constraint of each task. The present TS method fails to take the advantage of spatial variation in various aspects for example amount of electrical energy and accessibility of renewable power production at geographic distributed GCDC locations. Consequently, it can be fail for performing each task of heterogeneous application within their delay bound in a lower power cost and higher revenue manner. In this study, a multi-objective optimization algorithm tackles the disadvantage of the present method is presented.
Mishra et al. [17] examined the power utilization in CC environments depending on variety of services and attained the provision for promoting GCC. This would assist to retain total power consumption of the scheme. Task distribution in the CC environments is a familiar problem and using these problems, could enable GCC. Also, they have presented an adaptive task allocation method for the heterogeneous CC environments. The study employed presented method for minimizing the makespan of the cloud scheme and reduces the power utilization. Yuan et al. [18] adapt a G/G/1 queueing scheme for analyzing the efficiency of the server in DGC. Depending on it, a single objective constrained optimization problems are solved and formulated by a presented SBA approach finding SBA method could minimalize the power costs of DGC providers by optimally assigning task of heterogeneous applications amongst many DGCs, and specify the operating speed of every server and the amount of powered-on servers in every GC when severely meet the response time limit of task of each application.
Abualigah and Diabat [19] projected a new hybrid antlion optimization approach using elite based differential evolution to solve multiobjective TS challenges in CC environment. The antlion optimization approach has been improved with the help of elite-based differential evolution as a local search approach for improving its exploitation capability and prevent from getting trapped in local optimal. In Shu et al. [20], robust agile response TS optimization algorithms are presented based on the peak energy utilization of datacentres and the time span of TS. Also, agile response optimization technique is adapted. From the perception of task failure rate, the presented method could be employed for investigating the robust agile response optimization method, request a timeout for avoiding network congestions, and probability density function of the task request queue overflow.
Peng et al. [21] presented an effective real time deterministic scheduling (RTDS) model. Primarily, the SSDT can be mathematically formulated as a multi-way flow scheduling issue. Next, the RTDS designed scheduling request pre-processing (SRP) and greedy based multi-channel time slot allocation (GMT) to schedule in an optimal way. Yang et al. [22] presented a smart trust cloud management approach, which includes a trust cloud updating scheme. The experimental outcome demonstrated that the presented model can proficiently resolve the trust uncertainty problem and enhance the detection rate of the malicious devices. Wang et al. [23] presented a delay aware secured non-orthogonal multiple access (NOMA) transmission model with high altitude platform (HAP) and low altitude platform (LAP) collaborated to steadily offer delay sensitive healthcare services. An efficient AP-LAP secure transmission model has been presented for offering NOMA communication services for many hotspots. With the restricted energy as well as spectrum, privacy information delay can be reduced.
Ding et al. [24] developed a generative adversarial network for image restoration among distinct kinds of deprivation. The presented model presented an effective model with an inverse and a reverse module for addressing extra attributes among the image styles. With secondary data, the restoration can be highly accurate. Besides, a loss function can be developed for the stabilization of adversarial training with improved training performance. Tan et al. [25] proposed a blockchain enabled security as well as privacy protection model with traceable and direct revocation for COVID-19 healthcare data. Here, the blockchain is employed for uniform identity authentication and every public key, revocation list, and so on are saved on a blockchain. The system manager server has the responsibility of generate system parameters and published the private key for COVID-19 healthcare professionals.
3 Problem formulation
LB is a widely employed approach to maximize throughput, optimize resource utilization, ensure fault-tolerant configuration, and reduce latency. In GCC infrastructure, LB is an approach applied for spreading workloads amongst numerous datacenters or other resource nodes, thus no individual resource is over-loaded. For better describing the scheme of the LB, dynamic, power utilization optimization methods could be provided in the following. Datacenters are usually made up of many resources sites shared in distinct geographical places in GCC. Actually, every subtask \({t}_{i}\) \(\left(i=\mathrm{1,2}, \dots , m\right)\) could attain a resource site \({R}_{j}\) for meeting the fundamental execution condition, where \(n\) signifies the amount of resources for meeting the subtask \({t}_{i}\). The Poisson distributions are appropriate to describe the amount of arbitrary actions arising within a unit time (or space). Hence, the dynamic procedure of TS and RA in CC infrastructure could be deliberated as a Poisson distribution.
Definition 1 Consider that GCC method \(GCloud=\left(D, T, P, G\right)\), \(D=\left\{{D}_{1}, {D}_{2}, {D}_{d}\right\}\) is a set of \(d\) cloud server datacenters, \(T\) represents the correspondence matrix among computing node and random task, \({T}_{ij}\) signifies the task \({t}_{i}\) is performed on node \(j\). Pi denotes the power of node \(i\) while it can be idle, and \({G}_{i}\) means the peak power of node [26].
Definition 2 Consider that the network bandwidth matrix of all datacenters is \(B\) in GCC, \({b}_{ij}\) represents the broadcast bandwidth of every node in the datacenter.
For minimizing the power utilization in the cost constrained energy optimization, is for estimating the cost of power utilization in the procedure of the accomplishment of the CC.
Definition 3 Consider that \({Q}_{i}\) signifies the amount of instruction of tasks\({t}_{i}\), \({\mu }_{i}\) denotes the usage rate of node \(i,\) \({f}_{i}\) indicates the frequency of node \(i\), the runtime of task \({t}_{i}\) on node \(i\) is \({Q}_{i}/{V}_{j}^{i}\). The energy of server perform the task \({t}_{i}\) could be expressed by
where, \(i=1, 2,\dots , m,\) \(j=1, 2,\dots , {n}_{i}\).
Reducing the power utilization of computing nodes could be understood by decreasing the percentage of idle nodes \(X\). The power utilization of GCC environment is provided below
With the rapid growth of CC, the server scale of cloud datacenter is continually increasing each year that causes enormous energy utilization. Moreover, unreasonable scheduling policy leads to power waste, make the datacenter functioning cost constantly expanding.
4 The proposed resource scheduling technique
EPO is a new optimized technique projected by Dhiman and Kumar in 2018 [27] that is simulated as budding performance of emperor penguins. The hybrid technique is called CEPO was presented for solving the real numbers optimized issues that are with the use of cultural technique. An important idea of CEPO is for obtaining problem solving technique in the budding performance of emperor penguins and create utilize of data for guiding the development of emperor penguins population from returned. Assume that CEPO has been planned to common minimal optimized issue:
where \({\mathrm{x}}_{i}=\left({x}_{i1},{x}_{i2}, \dots ,{x}_{iD}\right)\) refers the place of \({i}^{th}\) emperor penguin from \(D\) dimension search space,\({x}_{j}^{\mathrm{min}}<{x}_{ij}<{x}_{j}^{\mathrm{max}},\left(j=\mathrm{1,2}, . . . , D\right)\). \(f\left(\right)\) represents the objective functions, and \(f\left({\mathrm{x}}_{i}\right)\) indicates the objective value of place\({\mathrm{x}}_{i}\). \({x}_{j}^{\mathrm{min}}\) and \({x}_{j}^{\mathrm{max}}\) implies the lower as well as upper boundary of the place of emperor penguin from the \(jth\) dimensional.
A detailed space of emperor penguins’ population in \({t}^{th}\) generation determined as provided by \({\mathrm{s}}^{t}\) and \({\mathrm{N}}_{j}^{t}\), in which \({\mathrm{s}}^{t}\) refers the situational knowledge modules. \({\mathrm{N}}_{j}^{t}\) refers the normative knowledge that signifies the value space data to all parameters from \(jth\) dimensional and in \(tth\) generation. \({\mathrm{N}}_{j}^{t}\) stands for \(I\), \(L\), \(U\). \({\mathrm{I}}_{j}^{t}=[{l}_{j}^{t}, {u}_{j}^{t}]\), where \({\mathrm{I}}_{j}^{t}\) demonstrates the interval of normative knowledge from \(jth\) dimensional. The lower boundary \({l}_{j}^{t}\) and upper boundary \({u}_{j}^{t}\) are adjusted based on value range of variables provided as this issue. \({L}_{j}^{t}\) implies the objective value of lower boundary \({l}_{j}^{j}\) of \(jth\) parameter, and \({U}_{j}^{t}\) implies the objective value of upper boundary \({u}_{j}^{t}\) of \(jth\) parameter. The acceptance function has been utilized for selecting the emperor penguin is directly controls the present confidence space. Figure 2 illustrates the process involved in CEPO technique.
The situational knowledge \({\mathrm{s}}^{t}\) is upgraded as update function:
where \({\mathrm{x}}_{\mathrm{best}}^{t+1}\) implies the optimum place of emperor penguin population space from \(\left(t+1\right)\mathrm{th}\) generation. Considered that, for the \(qth\) cultural individuals, an arbitrary variable \({\theta }_{q}\) lies in the range of 0 and 1 has formed [28]. The \(qth\) cultural individuals affect the lower boundary of normative knowledge from \(jth\) dimensional if \({\theta }_{q}<0.5\) has been fulfilled. The normative knowledge \({\mathrm{N}}_{j}^{t}\) is upgraded by update function:
The qth cultural differences affect the upper boundary of normative knowledge from jth dimensional if \({\theta }_{q}\ge 0.5\) is fulfilled:
The situational and normative knowledge is utilized for guiding emperor penguin population development by control functions. In CEPO algorithm, a selective operator \(\beta \) has been created for selecting one of two approaches for controlling the of development emperor penguin populations:
where \({\mathrm{Max}}_{\mathrm{iteration}}\) refers the maximal number of iterations. Considered that for ith emperor penguins, an arbitrary variable \({\lambda }_{i}\) that lies from the range of 0 and 1 has been created. An initial method is for updating the place of emperor penguin with altering the search size and way of difference with confidence space that is executed if fulfilled \({\lambda }_{i}\le \beta \). The place of emperor penguin from jth dimensional is upgraded as:
where \(N(0, 1)\) implies the arbitrary number exposing to typical normal distribution. size \(\left({\mathrm{I}}_{j}^{t}\right)\) represents the length of adaptable interval of jth parameter from confidence space from tth generation. \(\eta \) fixed to be in the range of 0.01 and 0.61. Another manner is a series of steps from EPO that are huddle boundary generation, temperature profile on the huddle calculating, the distance computation amongst emperor penguin, and the place upgrade of emperor penguin that is implemented if the achieved \({\lambda }_{i}>\beta .\) The particular steps are demonstrated as:
where \({T}^{\prime}\) implies the temperature profile about the huddle, \(T\) refers the time to determine optimum solution, and \(R\) indicates the arbitrary variable that lies from the range of 0 and 1\(.\)
where \({\mathrm{D}}_{\mathrm{ep}}^{t}\) stands for the distance amongst emperor penguin as well as optimum solution, \({\mathrm{x}}_{\mathrm{best}}^{t}\) refers the present optimum solution initiate in emperor penguins population space from tth generation, \({S}_{\mathrm{ep}}\) implies the social force of emperor penguins which is responsible for convergence nearby the optimum solution, \({A}^{t}\) and \({B}^{t}\) are utilized for avoiding the collision amongst adjoining emperor penguin, and \({B}^{t}\) indicates the arbitrary variable that lies from range of 0 and 1. \({A}^{t}\) is calculated as:
where \(M\) refers the effort parameter that hold the gap amongst emperor penguin to collision avoidance and \({P}_{\text{grid}}^{t}\) (Accuracy) determines the absolute variance with relating the variance amongst emperor penguin. \({S}_{\mathrm{ep}}\left({A}^{t}\right)\) in Eq. (28) was calculated as:
where \(e\) demonstrated the base of natural logarithm. \(\varepsilon \) and \(\rho \) are 2 influence parameters to optimum exploration as well as exploitation that is in the range of [1.5, 2] and [2, 3]. Eventually, the place of emperor penguins is upgraded as:
The EERS-CEPO algorithm is derived to reduce energy usage via optimal allocation of resources in GCC. Power utilization of the resource utilization and computing devices have a stronger relationship with the power wattage equation as follows.
In which the Power is estimated using \(\mathrm{P}\), number of times calculated using \(\mathrm{T}\), and energy estimated by E. The difference among energy and power is very important because decrease in energy consumption doesn’t end in time to cut the expended power [29]. For storing the number of energy expended by the cloud resource is determined using the green cloud environment. The cloud resource has several classifications of servers, nodes, network topology, process units, storage facility, and power contribution unit the taken as full energy consumption at the cloud environment could be provided below
EN-Energy Consume from node, ECR-Cloud Resources energy, ES-Energy consumes from the server, EN-Energy Consume form network, EO-Energy consumes ES-Energy consumes from storage device, from another electrical equipment’s. The overall energy exploitations of physical resources include 2 components as \({\mathrm{E}}_{\mathrm{VM}} \mathrm{and}\) Estatic. The Estatic is the secured energy of a server despite working VM or not and \({\mathrm{E}}_{\mathrm{VM}}\) is the dynamic energy i.e., determined by VM working on it. Assume that there are \(\mathrm{nVM}\)
\({\mathrm{E}}_{\mathrm{VMi}}\) could be further rotten keen on the power utilization of devices like memory, IO, and CPU represented as VMI, Ecpu, EIO VMI, Emem VMI. The EIO VMI consists of the general power cost of each device which involves I/O Operations like network data transfer and disk. The power utilization of VMI is
The task of cloud assets such as disk storage, network interface, and CPU builds depiction on shift node \(\mathrm{on}/\) off to decrease the common power utilization. The cloud networks switch units of measurements using dynamism reconfigured for changing the action of the server when needed. The power utilization is decreased by shifting inactive to energy saving modes (hibernation, sleep).
5 Performance validation
For examining the improved efficacy of the EERS-CEPO technique, a sample GCC environment is considered with 6physcial machines (PMs) and every machine holds eight CPUs with the capacity power of 10,000 MIPS. The EERS-CEPO technique is simulated using CloudSim tool with job dispatcher, resource planner, cloud, and VM instances. Table 1 and Fig. 3 demonstrate the response time analysis of the EERS-CEPO technique with existing techniques under distinct tasks. The results portrayed that the EERS-CEPO technique has accomplished effective outcomes with least response time under all tasks. For instance, with 50 tasks, the EERS-CEPO technique has offered a reduced response time of 236 ms whereas the CCS, ICSA, and CSRSA techniques have obtained a raised response time of 249 ms, 241 ms, and 287 ms respectively. Similarly, with 200 tasks, the EERS-CEPO technique has provided a lower response time of 597 ms whereas the CCS, ICSA, and CSRSA techniques have attained a higher response time of 969 ms, 807 ms, and 1031 ms respectively.
Meanwhile, with 400 tasks, the EERS-CEPO technique has achieved a decreased response time of 12646 ms whereas the CCS, ICSA, and CSRSA techniques have resulted in an increased response time of 1713 ms, 1558 ms, and 1457 ms respectively. Furthermore, with 600 tasks, the EERS-CEPO technique has exhibited a minimum response time of 1860 ms whereas the CCS, ICSA, and CSRSA techniques have demonstrated a maximum response time of 2604 ms, 2287 ms, and 2124 ms respectively.
Table 2 and Fig. 4 illustrate the response time analysis of the EERS-CEPO approach with recent methods under different iterations. The outcomes showcased that the EERS-CEPO approach has accomplished effective results with least response time under all iterations. For instance, with 25 iterations, the EERS-CEPO manner has accessible a reduced response time of 1867 ms whereas the CCS, ICSA, and CSRSA techniques have obtained a raised response time of 2503 ms, 2564 ms, and 2121 ms correspondingly. In line with, 75 iterations, the EERS-CEPO manner has provided a lesser response time of 1236 ms whereas the CCS, ICSA, and CSRSA algorithms have attained a superior response time of 1979 ms, 2025 ms, and 1419 ms respectively. Meanwhile, with 175 iterations, the EERS-CEPO method has reached a minimum response time of 641 ms whereas the CCS, ICSA, and CSRSA manners have resulted in an improved response time of 962 ms, 839 ms, and 753 ms respectively. Eventually, with 250 iterations, the EERS-CEPO technique has outperformed a minimal response time of 654 ms whereas the CCS, ICSA, and CSRSA techniques have portrayed an increased response time of 845 ms, 824 ms, and 789 ms correspondingly.
Table 3 and Fig. 5 illustrate the execution time analysis of the EERS-CEPO method with state-of-art techniques under distinct tasks. The results portrayed that the EERS-CEPO manner has accomplished effective outcomes with least execution time under all tasks. For sample, with 50 tasks, the EERS-CEPO technique has offered a decreased execution time of 1515 ms whereas the CCS, ICSA, and CSRSA techniques have reached an increased execution time of 2064 ms, 1782 ms, and 2001 ms correspondingly. Also, with 200 tasks, the EERS-CEPO technique has given a lower execution time of 3287 ms whereas the CCS, ICSA, and CSRSA systems have attained a higher execution time of 3851 ms, 3678 ms, and 3537 ms respectively. In the meantime, with 400 tasks, the EERS-CEPO method has reached a decreased execution time of 4415 ms whereas the CCS, ICSA, and CSRSA techniques have resulted in an increased execution time of 5277 ms, 5105 ms, and 5011 ms respectively. Furthermore, with 600 tasks, the EERS-CEPO technique has displayed a minimum execution time of 5403 ms whereas the CCS, ICSA, and CSRSA methodologies have outperformed a higher execution time of 6547 ms, 6328 ms, and 5936 ms correspondingly.
Table 4 and Fig. 6 depicts the energy consumption analysis of the EERS-CEPO technique with recent algorithms under different t cycle. The results portrayed that the EERS-CEPO technique has accomplished effective outcomes with least energy consumption under all cycles. For instance, with 1 cycle, the EERS-CEPO technique has offered a decreased energy consumption of 1.76 KWh whereas the CCS, ICSA, and CSRSA manners have attained an increased energy consumption of 2.32 KWh, 2.21 KWh, and 1.92 KWh correspondingly. Likewise, with 3 cycles, the EERS-CEPO manner has given a lesser energy consumption of 1.79 KWh whereas the CCS, ICSA, and CSRSA algorithms have attained a higher energy consumption of 2.51 KWh, 2.58 KWh, and 1.95 KWh correspondingly. Followed by, with 5 cycles, the EERS-CEPO technique has gained a minimal energy consumption of 1.59 KWh whereas the CCS, ICSA, and CSRSA approaches have resulted in improved energy consumption of 1.88 KWh, 1.90 KWh, and 1.74 KWh respectively. Eventually, with 8 cycles, the EERS-CEPO technique has exhibited a minimum energy consumption of 2.45 KWh whereas the CCS, ICSA, and CSRSA techniques have outperformed a superior energy consumption of 2.91 KWh, 2.74 KWh, and 2.58 KWh correspondingly.
Table 5 and Fig. 7 showcases the average energy consumption (AEC) analysis of the EERS-CEPO manner with existing approaches under varying tasks. The results showcased that the EERS-CEPO technique has accomplished effective outcomes with least AEC under all tasks. For instance, with 50 tasks, the EERS-CEPO manner has presented a minimum AEC of 1.53 kJ whereas the CCS, ICSA, and CSRSA techniques have achieved a maximum AEC of 2.04 kJ, 1.85 kJ, and 1.85 kJ respectively. Similarly, with 200 tasks, the EERS-CEPO technique has provided a lower AEC of 2.89 kJ whereas the CCS, ICSA, and CSRSA approaches have attained a higher AEC of 3.61 kJ, 3.42 kJ, and 3.22 kJ respectively. Meanwhile, with 400 tasks, the EERS-CEPO system has reached a lower AEC of 5.08 kJ whereas the CCS, ICSA, and CSRSA techniques have resulted in an increased AEC of 6.93 kJ, 6.65 kJ, and 5.59 kJ correspondingly. Also, with 600 tasks, the EERS-CEPO manner has exhibited a minimum AEC of 7.69 kJ whereas the CCS, ICSA, and CSRSA algorithms have demonstrated a maximum AEC of 9.88 kJ, 9.49 kJ, and 8.57 kJ respectively.
Table 6 and Fig. 8 portray the average executive power (AEP) analysis of the EERS-CEPO method with existing techniques under distinct tasks. The results portrayed that the EERS-CEPO technique has accomplished effective outcomes with least AEP under all tasks. For instance, with 50 tasks, the EERS-CEPO technique has offered a reduced AEP of 1231 W whereas the CCS, ICSA, and CSRSA techniques have obtained a raised AEP of 1553 W, 1400 W, and 1676 W respectively.
Similarly, with 200 tasks, the EERS-CEPO technique has provided a lower AEP of 1998 W whereas the CCS, ICSA, and CSRSA techniques have obtained an increased AEP of 2366 W, 2244 W, and 2213 W respectively. At the same time, with 400 tasks, the EERS-CEPO manner has reached a lower AEP of 3348 W whereas the CCS, ICSA, and CSRSA algorithms have resulted in an increased AEP of 3916 W, 3839 W, and 3655 W respectively.
Finally, with 600 tasks, the EERS-CEPO methodology has exhibited a minimal AEP of 4376 W whereas the CCS, ICSA, and CSRSA methods have demonstrated a maximal AEP of 6170 W, 5787 W, and 4729 W respectively. The simulation results demonstrated that the EERS-CEPO technique has resulted in increased performance over the recent state of art schedulers in the GCC environment. The improved performance is due to the hybridization of EPO algorithm with CA.
6 Conclusion
This study has designed a new EERS-CEPO algorithm to reduce the energy utilization at the data centers of GCC. The proposed model has effectually allotted the load between distinct data centers or other resources and thereby avoiding overload of individual resources. The CEPO algorithm is designed by the integration of the EPO algorithm with the CA. The EERS-CEPO algorithm has derived a fitness function to optimally schedule the resources in data centers, thereby minimize the operational cost, energy utilization, heat generation, and maintenance cost of the GCC. An extensive simulation analysis is carried out to ensure the betterment of the EERS-CEPO algorithm. The simulation results demonstrated that the EERS-CEPO technique has resulted in increased performance over the recent state of art schedulers in the GCC environment. In future, VM migration techniques and fault tolerant approaches can be designed to maximize the efficiency of the GCC.
Data Availability
Data sharing not applicable to this article as no datasets were generated during the current study.
References
Radu, L.D.: Green cloud computing: a literature survey. Symmetry 9(12), 295 (2017)
Kumar, A.S., Venkatesan, M.: Task scheduling in a cloud computing environment using HGPSO algorithm. Clust. Comput. 22(1), 2179–2185 (2019)
Ghafari, R., Kabutarkhani, F.H., Mansouri, N.: Task scheduling algorithms for energy optimization in cloud environment: a comprehensive review. Cluster Comput (2022). https://doi.org/10.1007/s10586-021-03512-z
Rahimikhanghah, A., Tajkey, M., Rezazadeh, B., Rahmani, A.M.: Resource scheduling methods in cloud and fog computing environments: a systematic literature review. Cluster Comput (2021). https://doi.org/10.1007/s10586-021-03467-1
Masanet, E., Shehabi, A., Ramakrishnan, L., Liang, J., Ma, X., Walker, B., Hendrix, V., Mantha, P.: The energy efficiency potential of cloud-based software: a U.S. case study. (2013)
Yadav, R., Zhang, W.: MeReg: managing energy-SLA tradeoff for green mobile cloud computing. Wireless Commun. Mob. Comput. (2017). https://doi.org/10.1155/2017/6741972
Lambert, S., Van Heddeghem, W., Vereecken, W., Lannoo, B., Colle, D., Pickavet, M.: Worldwide electricity consumption of communication networks. Opt. Express 20(26), B513–B524 (2012)
Barroso, L.A., Holzle, U.: The case for energy-proportional ¨ computing. Comput. J. 40(12), 33–37 (2007)
Corradi, A., Fanelli, M., Foschini, L.: VM consolidation: a real case based on OpenStack Cloud. Futur. Gener. Comput. Syst. 32(1), 118–127 (2014)
Dashti, S.E., Rahmani, A.M.: Dynamic VMs placement for energy efficiency by PSO in cloud computing. J. Exp. Theor. Artif. Intell. 28(1–2), 97–112 (2016)
Zong, Z.: An improvement of task scheduling algorithms for green cloud computing. In: 2020 15th International Conference on Computer Science & Education (ICCSE), August (pp. 654–657). IEEE (2020)
Jena, R.K.: Energy efficient task scheduling in cloud environment. Energy Procedia 141, 222–227 (2017)
Thaman, J., Singh, M.: Green cloud environment by using robust planning algorithm. Egypt. Informat. J. 18(3), 205–214 (2017)
Yuan, H., Bi, J., Zhou, M.: Spatial task scheduling for cost minimization in distributed green cloud data centers. IEEE Trans. Autom. Sci. Eng. 16(2), 729–740 (2018)
Ranjan, A., Kaur, I., Bhardwaj, A., Sharma, V.: A Review of PSO-Based Task and Workflow Scheduling Analysis in Cloud Environment. SSRN J. (2021). https://doi.org/10.2139/ssrn.3842717
Yuan, H., Liu, H., Bi, J., Zhou, M.: Revenue and energy cost-optimized biobjective task scheduling for green cloud data centers. IEEE Trans. Autom. Sci. Eng. 18(2), 817–830 (2020)
Mishra, S.K., Puthal, D., Sahoo, B., Jena, S.K., Obaidat, M.S.: An adaptive task allocation technique for green cloud computing. J. Supercomput. 74(1), 370–385 (2018)
Yuan, H., Zhou, M., Liu, Q., Abusorrah, A.: Fine-grained resource provisioning and task scheduling for heterogeneous applications in distributed green clouds. IEEE/CAA J. Automat. Sin. 7(5), 1380–1393 (2020)
Abualigah, L.M., Diabat, A.: A novel hybrid antlion optimization algorithm for multi-objective task scheduling problems in cloud computing environments. Clust. Comput. 24(1), 205–223 (2021)
Shu, W., Cai, K., Xiong, N.N.: Research on strong agile response task scheduling optimization enhancement with optimal resource usage in green cloud computing. Future Generat. Comput. Syst. 124, 12–20 (2021)
Peng, Y., Jolfaei, A., Yu, K.: A novel real-time deterministic scheduling mechanism in industrial cyber-physical systems for energy internet. IEEE Trans. Industr. Inf. (2021). https://doi.org/10.1109/TII.2021.3139357
Yang, L., Yu, K., Yang, S.X., Chakraborty, C., Liu, Y., Guo, T.: An intelligent trust cloud management method for secure clustering in 5G enabled internet of medical things. IEEE Trans. Industr. Inf. (2021). https://doi.org/10.1109/TII.2021.3128954
Wang, D., He, Y., Yu, K., Srivastava, G., Nie, L., Zhang, R.: Delay sensitive secure NOMA transmission for hierarchical HAP-LAP medical-care IoT networks. IEEE Trans. Industr. Inf. (2021). https://doi.org/10.1109/TII.2021.3117263
Ding, F., Yu, K., Gu, Z., Li, X., Shi, Y.: Perceptual enhancement for autonomous vehicles: restoring visually degraded images for context prediction via adversarial training. IEEE Trans. Intell. Transport. Syst. (2021). https://doi.org/10.1109/TITS.2021.3120075
Tan, L., Yu, K., Shi, N., Yang, C., Wei, W., Lu, H.: Towards secure and privacy-preserving data sharing for COVID-19 medical records: a Blockchain-empowered approach. IEEE Trans. Netw. Sci. Eng. (2021). https://doi.org/10.1109/TNSE.2021.3101842
Lu, Y., Sun, N.: An effective task scheduling algorithm based on dynamic energy management and efficient resource utilization in green cloud computing environment. Clust. Comput. 22(1), 513–520 (2019)
Dhiman, G., Kumar, V.: Emperor penguin optimizer: a bio-inspired algorithm for engineering problems. Knowl. Based Syst. 159, 20–50 (2018)
Yang, J., Gao, H.: Cultural emperor penguin optimizer and its application for face recognition. Math. Problems Eng. (2020). https://doi.org/10.1155/2020/9579538
Karuppasamy, M., Balakannan, S.P.: Energy saving from cloud resources for a sustainable green cloud computing environment. J. Cyber Secur. Mobil. 7, 95–108 (2018)
Acknowledgements
Taif University Researchers Supporting Project Number (TURSP-2020/216), Taif University, Taif, Saudi Arabia.
Funding
Funding provided by The Science, Technology & Innovation Funding Authority (STDF) in cooperation with The Egyptian Knowledge Bank (EKB)
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest. The manuscript was written through contributions of all authors. All authors have given approval to the final version of the manuscript.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Mansour, R.F., Alhumyani, H., Khalek, S.A. et al. Design of cultural emperor penguin optimizer for energy-efficient resource scheduling in green cloud computing environment. Cluster Comput 26, 575–586 (2023). https://doi.org/10.1007/s10586-022-03608-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-022-03608-0