Abstract
Optimal security reductions for unique signatures (Coron, Eurocrypt 2002) and their generalization, i.e., efficiently re-randomizable signatures (Hofheinz et al. PKC 2012 & Bader et al. Eurocrypt 2016) have been well studied in the literature. Particularly, it has been shown that under a non-interactive hard assumption, any security reduction (with or without random oracles) for a unique signature scheme or an efficiently re-randomizable signature scheme must loose a factor of at least \(q_s\) in the security model of existential unforgeability against chosen-message attacks (EU-CMA), where \(q_s\) denotes the number of signature queries. Note that the number \(q_s\) can be as large as \(2^{30}\) in practice. All unique signature schemes and efficiently re-randomizable signature schemes are concluded to be accompanied with loose reductions from these impossibility results.
Somewhat surprisingly, in contrast to previous impossibility results (Coron, Eurocrypt 2002; Hofheinz et al. PKC 2012; Bader et al. Eurocrypt 2016), in this work we show that without changing the assumption type and security model, it is not always the case that any security reduction must loose a factor of at least \(q_s\). As a counterexample, we propose a unique signature scheme with a tight reduction in the EU-CMA security model under the Computational Diffie-Hellman (CDH) assumption. Precisely, in the random oracle model, we can program a security reduction with a loss factor of at most \(nq^{1/{n}}\), where n can be any integer independent of the security parameter for the scheme construction and q is the number of hash queries to random oracles. The loss factor in our reduction can be very small. Considering \(n=25\) and \(q=2^{50}\) as an example, the loss factor is of at most \(nq^{1/{n}}=100\) and therefore our security reduction is tight.
Notice that the previous impossibility results are derived from proofs via a so-called meta-reduction technique. We stress that instead of indicating any flaw in their meta-reduction proofs, our counterexample merely demonstrates that their given meta-reduction proofs fail to capture all security reductions. More precisely, we adopt a reduction called query-based reduction, where the reduction uses a hash query from the adversary to solve an underlying hard problem. We show that the meta-reduction proofs break down in our query-based reduction. The query-based reduction is not a new notion and it has been adopted for encryption proofs, but this work is the first seminal approach for applying query-based reduction in digital signatures.
The given counterexample in this work is of an independent interest as it implies a generic way of constructing a digital signature scheme (including unique signatures) with a tight reduction in the random oracle model from a digital signature scheme with a loose reduction. Although our proposed methodology is somewhat impractical due to the inefficiency of signature length, it introduces a completely new approach for tight proofs that is different from traditional approaches using a random salt.
You have full access to this open access chapter, Download conference paper PDF
1 Introduction
Security reduction is the fundamental method for proving provable security in cryptosystems. In a security reduction, if there exists an efficient adversary who can break a newly proposed scheme, we prove that a generally believed-to-be-hard mathematical problem can be efficiently solvable with the help of this adversary. This, however, contradicts with the hardness assumption and hence we conclude that the proposed scheme is secure. Suppose the adversary can break a digital signature scheme in t polynomial time with a non-negligible probability \(\epsilon \). Generally speaking, a security reduction will solve an underlying hard problem in \(t+T\) time with probability \(\frac{\epsilon }{L}\). Here T refers to the time cost of reduction while L refers to the loss factor (or security loss), which means the success probability of reduction is \(\frac{1}{L}\) only. When the loss factor is linear in the number of signature queries denoted by \(q_s\) from the adversary, the security reduction is said to be a loose reduction because the number of signature queries can be as larger as \(2^{30}\). When the loss factor L is constant and small, the security reduction is said to be a tight reduction. In concrete security [4, 17], a tight reduction is essential for constructing an efficient scheme without increasing the security parameter to compensate the loss factor.
A significant number of digital signature schemes have been proposed in the literature. Many of them, such as [2, 5, 6, 9, 11, 14, 17, 19], are provably secure with tight reductions. In this work, a security reduction for a signature scheme refers to a reduction from a non-interactive computational hard problem under the security model of existential unforgeability against chosen-message attacks (EU-CMA) [12]. In a security reduction, we say a signature is simulatable if the signature can be simulated by the simulator without knowing the corresponding secret (signing) key and a signature is reducible if the signature can be reduced to solve a hard problem. The difficulty of achieving a tight reduction in the literature is due to the fact that we need to program the reduction with a high success probability without knowing which messages whose signatures should be programmed as simulatable and which messages whose signatures should be programmed as reducible. To overcome this difficulty, all known signature schemes with tight reductions to date use a random salt (number) in the signature generation such that a signature of a given message can be either simulatable or reducible depending on the choice of the random salt. The simulator relies on this functionality to obtain a high success probability of reduction, especially without abortion during signature queries.
Unique signatures are one special type of digital signatures which do not use any random salt in the signature generation. The signature for each message therefore is unique. As a consequence, we cannot switch the functionality (simulatable or reducible) of each unique signature in the security reduction. Therefore, it seems any security reduction for a unique signature scheme cannot be tight. In fact, optimal security reductions for unique signatures or their generalization have been studied in [3, 10, 15]. They showed that it is impossible to program a better security reduction with a loss factor of less than \(q_s\) for a unique signature scheme or an efficiently re-randomizable signature scheme, where \(q_s\) is the number of signature queries. To be precise, in Eurocrypt 2002, Coron [10] described a meta-reduction proof to prove the impossibility of tight reductions for certain digital signatures including unique signatures. Coron claimed the success probability of any security reduction for a unique signature scheme cannot substantially exceed \(\epsilon _\mathcal{F}/ (e q_s)\). That is, the loss factor is of at least \(e\cdot q_s\). Here e is the base of the natural logarithm and \(\epsilon _\mathcal{F}\) is the adversary’s advantage (probability) of forging a valid signature in the EU-CMA security model. Ten years later, in Eurocrypt 2012, Kakvi and Kiltz [16] found and fixed a subtle technical flaw in the Coron’s impossibility result. They showed the optimal security reduction for the RSA-FDH (Full Domain Hash) signature scheme cannot be guaranteed, if public keys are not certified. In PKC 2012, Hofheinz, Jager and Knapp [15] extended the meta-reduction proof for a slightly more general signature notion, namely efficiently re-randomizable signatures. They proved and claimed that any black-box security reduction for a signature scheme with efficiently re-randomizable signatures must have a reduction loss of at least \(\varOmega (q_s)\); otherwise, the underlying hardness assumption is false. In Eurocrypt 2016, Bader, Jager, Li and Schäge [3] improved the impossibility result of [10, 15, 16] with simpler proofs and bound, where the minimum loss factor is \(q_s\). Particularly, they introduced the notion of efficiently re-randomizable relations to overcome the subtle issue discovered by Kakvi and Kiltz [16] and further generalized the notion of efficiently re-randomizable signatures [15].
In short, the aforementioned impossibility results (Coron, Eurocrypt 2002; Hofheinz et al. PKC 2012; Bader et al. Eurocrypt 2016) have shown that any security reduction for a unique signature scheme or an efficiently re-randomizable signature scheme must loose a factor of \(q_s\), which is the number of signature queries. That is, in all corresponding security reductions, the success probability of reduction is of at most \(\frac{1}{q_s}\).
Our contributions. In contrast to previous impossibility results, in this work, we show that not all security reductions for unique signature schemes or efficiently re-randomizable signature schemes must loose a factor of \(q_s\). As a counterexample, we construct a special unique signature scheme with a tight reduction under the Computational Diffie-Hellman (CDH) assumption in the EU-CMA security model. In our security proof with random oracles, we program the security reduction to solve the CDH problem with a loss factor of at most \(n q^{\frac{1}{n}}\). Here, n is an integer decided by the scheme designer independent of the security parameter for the scheme construction and q is the number of hash queries to the random oracle. Although our loss factor is associated with q but it can be very small. Taking the example of \(n=25, q=2^{50}\) and \(q_s=2^{30}\), the loss factor in our security reduction for the given counterexample is of \(n q^{\frac{1}{n}}=100\) only, which is significantly reduced compared to \(q_s=2^{30}\). Hence, we claim that our security reduction is a tight reduction from a non-interactive computational hard problem in the standard EU-CMA security model. We note that our unique signature scheme is the first realFootnote 1 unique signature scheme with a tight reduction.
We stress that our counterexample does not indicate any flaw in the given proofs [3, 10, 15]. Instead, we found their proofs fail to capture all security reductions. More precisely, in the traditional security reduction for digital signatures, the reduction uses a forged signature from the adversary that cannot be efficiently computed by the simulator to solve a computational hard problem. We call this reduction forgery-based reduction. The tight security reduction in our given example is completely different and we name it as query-based reduction, where the reduction uses one of hash queries from the adversary to solve a computational hard problem. We analyze the reason why there is a gap in the proofs of impossibilities when using the query-based reduction in Sect. 1.4. Notice that the query-based reduction is not a completely new notion because it has been used in enabling provable security for encryption under computational hard problems in the indistinguishability security model, such as the hashed ElGamal encryption scheme [1]. However, this is the first time of applying query-based reduction in proving security for digital signatures.
The given counterexample is of an independent interest in terms of exploring generic approaches for signature scheme constructions with tight reductions. It implies a methodology of constructing a digital signature scheme including unique signatures with a tight reduction in the random oracle model from a digital signature scheme with a loose reduction. Our proposed methodology has to increase the signature length by n times and hence it is somewhat impractical even taking the loss factor into account. However, we stress that our idea is theoretically interesting as it, for the first time, introduces how to obtain a tight proof for digital signatures without the use of a random salt in the signature generation.
Remark 1
The authors in [3, 10, 15] claimed that the impossibility of tight reductions holds for any security reduction. From what they have proved (i.e., given theorems), we found that their “security reduction” refers to the following two types.
-
Any security reduction without the use of random oracles for a signature scheme.
-
Any security reduction with random oracles for a hash-and-sign signature scheme [10], such as a full domain hash signature scheme.
We note that our query-based reduction with random oracles is proposed to prove a unique signature scheme, whose structure is different from the hash-and-sign signature defined in [10]. Our signature scheme can be seen as a hash-and-sign structure repeated for n times. Therefore, our given example is not included in the above two types of reductions.
1.1 Overview of Our Counterexample and Security Reduction
In this section, we propose a simplified counterexample with \(n=2\) and show how to program the reduction with a loss factor of at most \(2q^{\frac{1}{2}}\) under the CDH assumption in the EU-CMA security model. Here, q is the number of hash queries to the random oracle made by the adversaryFootnote 2. The given scheme and reduction can be naturally extended to a full scheme with a loss factor of \(nq^{\frac{1}{n}}\), where each signature in the full signature scheme contains \(n+1\) group elements. We admit that the proposed scheme is less efficient compared to other unique signature schemes such as [7] especially with the growth of n. We emphasize that the proposed scheme is merely for demonstrating that there indeed exists a unique signature scheme with a tight reduction.

The structure of our unique signature is similar to the blockchain [8, 18]. Each component \(\sigma _i\) in our signature scheme is a block signature of a given message m to be signed together with all previous block signatures. The block signature is generated using the BLS signature [7]. In this simplified scheme, each signature \(\varSigma _m\) is composed of three block signatures \((\sigma _1, \sigma _2, \sigma _3)\). The full unique signature scheme will be composed of \(n+1\) block signatures. We note that the block signature does not have to use the BLS signature and can be instantiated using a different unique signature from other schemes such as [20]Footnote 3. Our proposed signature scheme can also be seen as a variant of the BLS signature scheme towards a tight reduction.
For the security proof of the simplified unique signature scheme, we will program the security reduction in the random oracle model, where H is set as the random oracle. The reduction is an interaction between an adversary who can break the proposed scheme and a simulator who simulates both the real scheme and the random oracle for the adversary. Different from the forgery-based security reduction, the constructed simulator in our reduction will use one of hash queries generated by the adversary instead of a forged signature from the adversary to solve the CDH problem. Therefore, the random oracle plays the most important role in this type of reduction. The reduction is much more complex compared to that for the BLS signature scheme especially in the simulation of the random oracle. Before showing how to program the reduction, we give three preliminaries to help understanding the core of this security reduction.
In this paper, we say an adversary makes a hash query H(x) to the random oracle meaning that the adversary sends x to the random oracle in order to know what H(x) is. Without querying H(x) to the random oracle, H(x) is random and unknown to the adversary, such that the adversary has no advantage in computing \(H(x)^{\alpha }\) even it knows \(\alpha \). In our simplified scheme, due to the “chain” structure, the adversary who does not know the signature \(\varSigma _m\) of a message m must first query H(m), then query \( H(m||\varSigma _{m}^1)\), and finally query \(H(m||\varSigma _{m}^2)\) to the random oracle. This sequence is essential because \(\varSigma _{m}^1\) contains the block signature \(H(m)^{\alpha }\) requiring to know H(m) first, and \(\varSigma _{m}^2\) contains the block signature \( H(m||\varSigma _{m}^1)^{\alpha }\) requiring to know \( H(m||\varSigma _{m}^1)\) first. Therefore, each signature generation is required to make three hash queries to the random oracle and these three hash queries must be made sequentially. This is the first preliminary about sequential hash queries on the same message without having its signature.
The adversary could launch hash queries associated with the same message m in the following four cases before querying its signature or without its signature query.
-
In the first case, the adversary never queries \(H(m), H(m||\varSigma _m^1)\), \(H(m||\varSigma _m^2)\) to the random oracle.
-
In the second case, the adversary queries H(m) only to the random oracle. That is, the adversary never queries \(H(m||\varSigma _m^1)\), \(H(m||\varSigma _m^2)\) to the random oracle.
-
In the third case, the adversary queries H(m) and \(H(m||\varSigma _m^1)\) to the random oracle. That is, the adversary never queries \(H(m||\varSigma _m^2)\) to the random oracle.
-
In the fourth case, the adversary queries all \(H(m), H(m||\varSigma _m^1), H(m||\varSigma _m^2)\) to the random oracle. Hash queries associated with the message \(m^*\) to be forged by the adversary falls into this case. Otherwise, at least one hash value is random and unknown to the adversary, such that it cannot forge a valid signature of \(m^*\) with a non-negligible advantage.
These four cases are also summarized in Table 1. We stress that as an example, if the adversary first queries H(m) to the random oracle, then queries the signature \(\varSigma _m\) of m to the simulator, and thereafter queries \(H(m||\varSigma _m^1), H(m||\varSigma _m^2)\) to the random oracle for signature verification, we have the message m belongs to the second case not the fourth case. For a message m belonging to the third case, we note that the adversary must compute \(\varSigma _{m}^1\) first before the hash query \(H(m||\varSigma _m^1)\). For a message m belonging to the fourth case, the adversary must compute \(\varSigma _{m}^1\) and \(\varSigma _m^2\) first before the hash queries \(H(m||\varSigma _m^1), H(m||\varSigma _m^2)\). To forge a valid signature, the adversary must compute \(\varSigma _{m^*}^1\) and \(\varSigma _{m^*}^2\) for hash queries \(H(m^*), H(m^*||\varSigma _{m^*}^1), H(m^*||\varSigma _{m^*}^2)\) in order to forge the signature \(\varSigma _{m^*}\) of \(m^*\). Therefore, there must exist one message belonging to the fourth case. Notice that the adversary could make hash queries associated with other messages belonging to the third case or the fourth case. In our reduction, the simulator shall use these special hash queries for reduction and these queries require the adversary to compute block signatures first. When one of block signatures is reducible, the simulator can then use the corresponding block signature to solve a computational hard problem. This is the second preliminary explaining how our query-based reduction works.
In the query-based reduction, we need to identify who (either the adversary or the simulator) first time submits a query to the random oracle. We note that the above four cases are only those queries first time generated and submitted by the adversary to the random oracle. Besides these hash queries, the simulator could add some other hash queries to the random oracle. Considering the above example where the adversary first queries H(m) to the random oracle and then queries the signature \(\varSigma _m\) to the simulator. The simulator has to program hash queries \(H(m||\varSigma _m^1)\) and \(H(m||\varSigma _m^2)\) before the signature simulation on m, where these two queries could be made by the adversary again for the signature verification purpose. These two queries therefore are first time made by the simulator and the simulator should be able to compute \(\varSigma _m^1\) and \(\varSigma _m^2\). Notice that the simulator cannot solve the underlying hard problem using one hash query first time submitted to the random oracle by itself. Otherwise, the simulator can solve the hard problem without the adversary. It is therefore important to identify who first time makes a query to the random oracle and we focus on those queries first time generated by the adversary. This is the supplementary of the second preliminary.
The query input to the random oracle can be any arbitrary string adaptively chosen by the adversary. In this work, we assume the concatenation notation “||” will not appear within messagesFootnote 4, such that it is easy for the simulator to distinguish the input structure of each query denoted by x. Furthermore, the simulator can run the pairing computation to verify the correctness of each block signature. Therefore, for each query x first time generated by the adversary, we define
-
x is a query belonging to Type 0 if x is equal to m without the notation “||”.
-
x is a query belonging to Type 1 if x is equal to \(m||\varSigma _m^1\) with one block signature.
-
x is a query belonging to Type 2 if x is equal to \(m||\varSigma _m^2\) with two block signatures.
-
x is a query belonging to Type D if x is different from the above three types. For example, x is equal to a message concatenated with invalid block signatures or more than two block signatures.
We define three message sets \(\mathcal {M}_0, \mathcal {M}_1, \mathcal {M}_2\) during the random oracle simulation as follows to include all messages in those queries generated by the adversary and belonging to Type 0, Type 1 or Type 2. We are not interested in queries belonging to Type D because they are not used for signature generations. Before the adversary starts making hash queries to the random oracle, these three message sets are initialized with empty sets. These three message sets are managed by the simulator and it adds messages into them when a query from the adversary satisfies the following conditions.
-
If x is a query belonging to Type 0, the message m in x will be added into the message set \(\mathcal {M}_0\). Let \(\mathcal {M}_0=\{m_{0,1}, m_{0,2}, \cdots , m_{0,q_0}\}\) where \(|\mathcal {M}_0|=q_0\).
-
If x is a query belonging to Type 1, the message m in x will be added into the message set \(\mathcal {M}_1\). Let \(\mathcal {M}_1=\{m_{1,1}, m_{1,2}, \cdots , m_{1,q_1}\}\) where \(|\mathcal {M}_1|=q_1\).
-
If x is a query belonging to Type 2, the message m in x will be added into the message set \(\mathcal {M}_2\). Let \(\mathcal {M}_2=\{m_{2,1}, m_{2,2}, \cdots , m_{2,q_2}\}\) where \(|\mathcal {M}_2|=q_2\).
For easy understanding, all messages in the message sets are added sequentially. That is, \(m_{i,1}\) is first added to the message set \(\mathcal {M}_i\) followed by the message \(m_{i,2}\).
Suppose the total number of hash queries made by the adversary is q and the adversary ever queries \(H(m^*), H(m^*||\varSigma _{m^*}^1), H(m^*||\varSigma _{m^*}^2)\) for a message \(m^*\) in order to forge its signature. According to the first preliminary and Table 1, we have the following important observation
The above relationship is always correct and independent of what messages are selected for hash queries, what messages are selected for signature queries and which message is selected for signature forgery. This is the third preliminary about the relationship of messages in those hash queries generated by the adversary.
Now, we are ready to describe how to program the security reduction for the simplified scheme. Suppose there exists an adversary who can break the signature scheme in the EU-CMA security model. The simulator programs the simulation as follows. Given a random instance of the CDH problem \((g,g^a,g^b)\) under a pairing group \(\mathbb {PG}\), the simulator sets \(\mathbb {PG}\) as the system parameters and \(h=g^a\) in the public key simulation, where the secret key \(\alpha =a\) is unknown to the simulator. The simulator simulates the random oracle for H instead of giving the hash function to the adversary. During the random oracle simulation, the simulator programs the instance \(g^b\) in one of H(x) such that \(H(x)^{\alpha }\) containsFootnote 5 the CDH solution \(g^{ab}\). For all other queries, the simulator computes H(y) in the way that \(H(y)^\alpha \) is computable by the simulator. The core of oracle simulation is which query should be responded using \(g^b\). We name this query as target query and the corresponding message as target message denoted by \(\hat{m}\). In our simulation, the simulator firstly chooses a random integer \(c^*\in \{0,1\}\) and then it works as follows.
-
If \(c^*=0\), it randomly chooses another integer \(k^*\in [1, q^{1-\frac{c^*}{2}}]\), where the range is equal to [1, q]. In this case, the target query is the one whose message will be the \(k^*\)-th message added into the message set \(\mathcal {M}_0\), if such a message exists in the message set. Otherwise, aborts. That is, the target query is
$$\begin{aligned} m_{c^*,k^*}=\hat{m}. \end{aligned}$$We have \(H(\hat{m})\) contains \(g^b\). When the message \(\hat{m}\in \mathcal {M}_0\) also appears in the message set \(\mathcal {M}_1\), it means the adversary ever submitted the following query to the random oracle
$$\begin{aligned} \hat{m}||\varSigma _{\hat{m}}^1, \end{aligned}$$where the block signature \(\sigma _1\) in \(\varSigma _{\hat{m}}\) is equal to \(H(\hat{m})^{\alpha }\) containing the solution \(g^{ab}\) to the hard problem. That is, the simulator embeds \(g^b\) in the response to one of Type 0 queries and will use a Type 1 query to solve the underlying hard problem.
-
If \(c^*=1\), it randomly chooses another integer \(k^*\in [1, q^{1-\frac{c^*}{2}}]\) (Note: this range is different from the first case), where the range is equal to \([1,q^{\frac{1}{2}}]\). In this case, the target query is the query whose message will be the \(k^*\)-th message added into the message set \(\mathcal {M}_1\), if such a message exists in the message set. Otherwise, aborts. That is, the target query is
$$\begin{aligned} m_{c^*,k^*}||\varSigma _{m_{c^*,k^*}}^1=\hat{m}||\varSigma _{\hat{m}}^1. \end{aligned}$$We have \(H(\hat{m}||\varSigma _{\hat{m}}^1)\) contains \(g^b\). When the message \(\hat{m}\in \mathcal {M}_1\) also appears in the message set \(\mathcal {M}_2\), it means the adversary ever submitted the following query to the random oracle
$$\begin{aligned} \hat{m}||\varSigma _{\hat{m}}^2, \end{aligned}$$where the second block signature \(\sigma _2\) in \(\varSigma _{\hat{m}}^2\) is equal to \(H(\hat{m}||\varSigma _{\hat{m}}^1)^{\alpha }\) containing the solution \(g^{ab}\) to the hard problem. That is, the simulator embeds \(g^b\) in the response to one of Type 1 queries and will use a Type 2 query to solve the underlying hard problem.
We emphasize that the target message \(\hat{m}\) does not have to be equal to the message \(m^*\) for the signature forgery. This is the main reason why our security reduction has a small loss factor. This completes the core of our simulation.
Now, we analyze the loss factor of our reduction. Let \(\Pr [Success]\) be the success probability of reduction when the adversary can successfully forge a valid signature. According to the simulation setting, the reduction is successful when one of hash queries contains the solution to the hard problem. We claim the loss factor is of at most \(2q^{\frac{1}{2}}\). A compact probability analysis is given as follows.
First, since \(c^*\in \{0,1\}\) is randomly chosen, we have
We calculate one of conditional probabilities only, which is decided by \(q_1\) as follows.
-
If \(q_1\ge q^{\frac{1}{2}}\), we calculate \( \Pr [Success|c^*=0]\) only where
$$\begin{aligned} q_{0}<q=q^{1-\frac{0}{2}}~~~\text{ and }~~~q_{1}\ge q^{\frac{1}{2}}=q^{1-\frac{1}{2}}. \end{aligned}$$ -
Otherwise, \(q_1< q^{\frac{1}{2}}\), we calculate \( \Pr [Success|c^*=1]\) only where
$$\begin{aligned} q_{1}<q^{\frac{1}{2}}=q^{1-\frac{1}{2}}~~~\text{ and }~~~q_{2}\ge 1=q^{1-\frac{2}{2}}. \end{aligned}$$
One can note that no matter \(q_1\ge q^{\frac{1}{2}}\) or \(q_1< q^{\frac{1}{2}}\), there exists an integer \(i^*\in [0, 1]\) (i.e. \(i^*\in \{0,1\}\)) such that
Then, we prove \( \Pr [Success|c^*=i^*]\ge 1/q^{\frac{1}{2}}\). The target query is associated with a target message from the message set \(\mathcal {M}_{c^*}\), where the target message is \(m_{c^*, k^*}\) denoted by \(\hat{m}\). When \(c^*=i^*\), we have
such that each message in \(\mathcal {M}_{c^*}\) will be chosen as the target message \(\hat{m}\) with probability \(1/q^{1-\frac{i^*}{2}}\). Furthermore, we have
such that
Finally, we have
This completes the high level description of our security reduction for the simplified unique signature scheme where \(n=2\).
1.2 Examples
We give four simple examples to verify the success probability. In these examples, suppose \(q=9\) and the message chosen by the adversary for signature forgery is \(m^*=m_3\). No matter what the adversary has queried to the random oracle, we must have all queried messages satisfy \(m_3\in \mathcal {M}_2\subseteq \mathcal {M}_1 \subseteq \mathcal {M}_0.\) According to our simulation result, we should have that the loss factor is of at most \(2\cdot 9^{\frac{1}{2}}=6\). That is, we should have
Recall that messages in all message sets are in sequence and they are added according to their orders. For instance, the second and the third messages added into the message set \(\mathcal {M}_1\) in the Example 2 are \(m_4\) and \(m_1\), respectively. Furthermore,
-
A message m is added to the message set \(\mathcal {M}_0\) meaning that the adversary generated and submitted the Type 0 query \(x=m\) to the random oracle.
-
A message m is added to the message set \(\mathcal {M}_1\) meaning that the adversary generated and submitted the Type 1 query \(x=m||\varSigma _m^1\) to the random oracle.
-
A message m is added to the message set \(\mathcal {M}_2\) meaning that the adversary generated and submitted the Type 2 query \(x=m||\varSigma _m^2\) to the random oracle.
If the message m under Type 0 and Type 1 is queried and \(g^b\) is embedded in the response to the Type 0 query m, we can use the Type 1 query \(m||\varSigma _m^1\) to solve the underlying hard problem because \(\varSigma _m^1\) is equal to \(H(m)^{\alpha }\). Similarly, if the message m under Type 1 and Type 2 is queried and \(g^b\) is embedded in the response to the Type 1 query \(m||\varSigma _m^1\), we can use the Type 2 query \(m||\varSigma _m^2\) to solve the underlying hard problem because \(\sigma _2\) in \(\varSigma _m^2\) is equal to \(H(m||\varSigma _m^1)^{\alpha }\) (Table 2).
According to the setting of \((c^*, k^*)\), the \(k^*\)-th message in the message set \(\mathcal {M}_{c^*}\) is chosen as the target message \(\hat{m}=m_{c^*, k^*}\), where \(g^b\) will be embedded in the element \(H(m_{c^*, k^*}||\varSigma _{m_{c^*, k^*}}^{c^*})\). Notice that the integer \(k^*\) is randomly chosen from [1, 9] when \(c^*=0\) and randomly chosen from [1, 3] when \(c^*=1\). In the following examples, we only need to consider one case (\(c^*=0\) or \(c^*=1\)), whose success probability is at least \(1/9^{\frac{1}{2}}=1/3\).
-
1.
In the first example, the adversary makes the hash queries \(H(m), H(m||\varSigma _m^1)\), \(H(m||\varSigma _m^2)\) for messages \(\{m_1, m_2, m_3\}\). When \(c^*=0\), \(k^*\) is randomly chosen from [1, 9]. According to the queried messages, we have the reduction is successful if \(c^*=0\) and \(k^*\in \{1,2,3\}\), because the message \(m_{c^*, k^*}\) under Type 0 and Type 1 will be both queried. Since \(k^*\) is randomly chosen from [1, 9], we therefore have
$$\begin{aligned} \Pr [Success]\ge \Pr [k^*\in \{1,2, 3\}]\cdot \Pr [c^*=0]=\frac{3}{9}\cdot \frac{1}{2}=\frac{1}{6}. \end{aligned}$$ -
2.
In the second example, the adversary makes the hash query H(m) for messages \(\{m_1, m_2, m_3, m_4\}\), the hash query \(H(m||\varSigma _m^1)\) for messages \(\{m_2, m_4,m_1,m_3\}\) and the hash query \(H(m||\varSigma _m^2)\) for the message \(m_3\) only. When \(c^*=0\), \(k^*\) is randomly chosen from [1, 9]. According to the queried messages, we have the reduction is successful if \(c^*=0\) and \(k^*\in \{1,2,3,4\}\), because the message \(m_{c^*, k^*}\) under Type 0 and Type 1 will be both queried. Since \(k^*\) is randomly chosen from [1, 9], we therefore have
$$\begin{aligned} \Pr [Success]\ge \Pr [k^*\in \{1,2, 3,4\}]\cdot \Pr [c^*=0]=\frac{4}{9}\cdot \frac{1}{2}\ge \frac{1}{6}. \end{aligned}$$ -
3.
In the third example, the adversary makes the hash query H(m) for messages \(\{m_1, m_2, m_3, m_4, m_5\}\), the hash queries \(H(m||\varSigma _m^1), H(m||\varSigma _m^2)\) for messages \(\{m_3\), \(m_5\}\) only. When \(c^*=1\), \(k^*\) is randomly chosen from [1, 3]. According to the queried messages, we have the reduction is successful if \(c^*=1\) and \(k^*\in \{1,2\}\), because the message \(m_{c^*, k^*}\) under Type 1 and Type 2 will be both queried. Since \(k^*\) is randomly chosen from [1, 3], we therefore have
$$\begin{aligned} \Pr [Success]\ge \Pr [k^*\in \{1,2\}]\cdot \Pr [c^*=1]=\frac{2}{3}\cdot \frac{1}{2}\ge \frac{1}{6}. \end{aligned}$$ -
4.
In the fourth example, the adversary makes the hash query H(m) for messages \(\{m_1, m_2, m_3, m_4, m_5,m_6,m_7\}\), the hash queries \(H(m||\varSigma _m^1), H(m||\varSigma _m^2)\) for the message \(m_3\) only. When \(c^*=1\), \(k^*\) is randomly chosen from [1, 3]. According to the queried messages, we have the reduction is successful if \(c^*=1\) and \(k^*=1\), because the message \(m_{c^*, k^*}\) under Type 1 and Type 2 will be both queried. Since \(k^*\) is randomly chosen from [1, 3], we therefore have
$$\begin{aligned} \Pr [Success]\ge \Pr [k^*=1]\cdot \Pr [c^*=1]=\frac{1}{3}\cdot \frac{1}{2}= \frac{1}{6}. \end{aligned}$$
1.3 Security Reduction for the Full Scheme and Other Discussions
The above reduction is programmed for the simplified unique signature scheme, where each signature is composed of three block signatures only. The reduction for the full unique signature scheme with \(n+1\) block signatures is more complex but similar, which is given in Sect. 5. In the corresponding reduction, \(n+1\) message sets \(\mathcal {M}_0, \mathcal {M}_1, \mathcal {M}_2\), \(\cdots , \mathcal {M}_n\) will be defined which also satisfy
Similarly, we prove there exists an integer \(i^*\in [0,n-1]\) such that
In the corresponding simulation, the random values \((c^*, k^*)\) will be chosen from the following ranges
When \(g^b\) is programmed in the response to the target query \(\hat{m}||\varSigma _{\hat{m}}^{i^*}\) for the message \(\hat{m}\in \mathcal {M}_{i^*}\) and the target message \(\hat{m}\) also appears in the message set \(\mathcal {M}_{i^*+1}\) (i.e. the adversary also submits the hash query \(\hat{m}||\varSigma _{\hat{m}}^{i^*+1}\) to the random oracle), we have the hash query \(\hat{m}||\varSigma _{\hat{m}}^{i^*+1}\) contains the solution to the CDH problem. The success reduction requires that \(c^*\) happens to be equal to \(i^*\) mentioned above. Since \(|\mathcal {M}_{i^*}|< q^{1-\frac{i^*}{n}}\) and \(k^*\in [1, q^{1-\frac{i^*}{n}}]\), we have \(H(m||\varSigma _{m}^{i^*})\) for any message m in \(\mathcal {M}_{i^*}\) will be responded using \(g^{b}\) with probability \(1/q^{1-\frac{i^*}{n}}\). Furthermore, since \(\mathcal {M}_{i^*+1}\subseteq \mathcal {M}_{i^*}\) and \(|\mathcal {M}_{i^*+1}|=q_{i^*+1}\ge q^{1-\frac{i^*+1}{n}}\), \(\hat{m}\) can be any one of \(q_{i^*+1}\) messages within \(\mathcal {M}_{i^*+1}\). Therefore, we have the success probability
This completes the overview of our counterexample with a tight reduction.
Our proposed scheme can select other signature schemes to generate block signatures. The security reduction is still tight as long as only the block signature of the message \(m_{c^*,k^*}\in \mathcal {M}_{c^*}\) is reducible and the block signatures of other messages are simulatable. The proposed signature structure and the reduction method towards a tight reduction are independent of the block signatures and hence are universal.
Comparison of reductions. For easy understanding of the query-based reduction, we compare it with the traditional forgery-based reduction according to the above reduction as follows.
-
The forgery-based reduction utilizes a forged signature from the adversary to solve an underlying hard problem, while the query-based reduction utilizes one of hash queries from the adversary to solve an underlying hard problem.
-
In the forgery-based reduction, the solution must be associated with the message of forged signature. While in the query-based reduction, the solution does not have to be related to the message for signature forgery.
-
In the forgery-based reduction, the simulator cannot stop the simulation before it receives a forged signature from the adversary. While in the query-based reduction, the simulator can stop the simulation immediately after receiving a query containing the solution to the underlying hard problem.
-
In the forgery-based reduction, the simulator cannot compute the forged signature from the adversary. While in the query-based reduction, the simulator can compute signatures on all messages as long as the adversary’s hash queries have already contained the solution to the underlying hard problem.
-
The forgery-based reduction can be with or without random oracles, while the query-based reduction must be with random oracles.
Remark 2
In our given signature scheme, each signature comprises of three block signatures in the simplified scheme and \(n+1\) block signatures in the full signature scheme. The last block signature is not used in our security reduction, except forcing the adversary to make at least a Type 2 query or a Type n query (full scheme). We note that the number of block signatures can be reduced by one if we partially adopt the forgery-based reduction. Taking the simplified scheme as an example. It will be composed of two block signatures instead of three, such that there is no Type 2 query. When \(c^*=1\), \(g^b\) is programmed in the response to a Type 1 query. That is, the target query is
We have that \(H(\hat{m}||\varSigma _{\hat{m}}^1)\) contains \(g^b\). When the message \(\hat{m}\in \mathcal {M}_1\) is chosen as the message \(m^*\) to be forged, we have the second block signature in the forged signature is \(H(\hat{m}||\varSigma _{\hat{m}}^1)^{\alpha }\) which contains the solution to the CDH problem. That is, we use the forged signature to solve the underlying hard problem. We stress that this reduction is also correct. However, we do not adopt this method because it is relatively simpler to use only query-based reduction in the security proof.
1.4 The Gap in the Proofs of Impossibilities
We explain why our query-based reduction for the counterexample cannot be captured by the meta-reduction proofs [3, 10, 15]. Specifically, we would like to clarify the gap in the existing proofs for the impossibilities of tight reductions. We start with briefly recalling the notion of meta-reduction, which is the main technique adopted to derive their impossibility results. It is worth mentioning that Bader et al. [3] proposed a different meta-reduction to derive more generalized impossibility results. However, we note that they have the same principle. We provide more details as follows.
The meta-reduction proof for impossibilities. Roughly speaking, a meta-reduction is associated with the following three entities.
-
The reducer \(\mathcal R\) who can reduce a forged signature to solving an underlying hard problem. Let \(\epsilon _\mathcal{R}\) be the success probability of solving the underlying hard problem.
-
The real forger (adversary) \(\mathcal F\) who is able to forge a valid signature. Let \(\epsilon _\mathcal{F} \) be the advantage (probability) of forging a valid signature.
-
The simulated forger \(\mathcal{\overline{F}}\) who cannot forge a valid signature and aims to solve an underlying hard problem with the help of \(\mathcal R\) but without the help of \(\mathcal F\).
In the traditional security reduction, the interaction is between \(\mathcal R\) and \(\mathcal F\), while in the meta-reduction, the interaction is between \(\mathcal{\overline{F}}\) and \(\mathcal R\) only without the real forger. Specifically, in the meta-reduction, a simulated forger \(\mathcal{\overline{F}}\) is constructed to solve a hard problem with the help of the reducer \(\mathcal R\). Precisely, \(\mathcal{\overline{F}}\) firstly asks \(\mathcal R\) to sign a number of messages and then rewinds \(\mathcal R\) to the state before signature queries and re-starts the security game with \(\mathcal R\). Finally, it forges a valid signature using one of the signed message/signature pairs (say (\(m^*,\varSigma _{m^*}\))) obtained before the rewinding. When the simulated forger \(\mathcal{\overline{F}}\) is indistinguishable from the real forger \(\mathcal {F}\), the reducer \(\mathcal R\) should be able to output a solution to the underlying hard problem with a certain probability. It has been proved in [10] that through the above meta-reduction, \(\mathcal{\overline{F}}\) can obtain a solution to the underlying hard problem from the reducer \(\mathcal R\) with a success probability at least
for \(q_s\) number of signature queries to the reducer \(\mathcal R\).
If \(\epsilon _\mathcal{\overline{F}}\) is positive and non-negligible, it means we can efficiently solve a hard problem using the simulated forger \(\mathcal{\overline{F}}\) without the help of the real forger. This would contradict with the underlying hardness assumption. It therefore implies that \(\epsilon _\mathcal{R}\) must be no more than \(\epsilon _\mathcal{F}/\varOmega (q_s)\) for all security reductions. Hence, the loss factor in any security reduction is of at least \(q_s\).
The central argument in the meta-reduction requires that the simulated forger \(\mathcal{\overline{F}}\) is indistinguishable from the real forger \(\mathcal {F}\). To achieve this, the forged signature generated by the simulated forger must be indistinguishable from the forged signature generated by the real forger, such that \(\mathcal R\) is convinced that it is interacting with a real forger and thus outputs a solution to the hard problem. In the literature, unique signatures [10] and efficiently re-randomizable signatures [3, 15] are shown to be able to capture this indistinguishability.
The gap in the proofs. One could note that the existing work [3, 10, 15] implicitly claimed that the aforementioned meta-reduction works as long as the simulated forger \(\mathcal{\overline{F}}\) outputs a correctly distributed signature (and hence indistinguishable from a real forged signature) to convince \(\mathcal R\) that it is a real forger. In fact, this is the central argument for the existing meta-reductions in proving the impossibility results for unique signatures and their generalization. Let \(\varSigma (pk,m)\) be the set of signatures \(\varSigma _m\) with regards to the message m and the public key pk under the system parameters. During the proofs [3, 10, 15], they are silently assumed that this signature set \(\varSigma (pk,m)\) in the simulation is determined by pk, m and possibly by additional random oracle queries that are assumed to be efficiently computable. However, this assumption does not necessarily hold in all security reductions. In our example, each useful hash query except Type 0 requires to compute a block signature that is not efficiently computable without knowing the signing key. Any successful (real) forger \(\mathcal {F}\) must make some non-efficiently computable hash queries to the random oracle. This is the reason why the meta-reduction requiring that all hash queries are efficiently computable will fail to simulate the forger.
More precisely, as shown in our query-based reduction for the simplified scheme, a successful reduction essentially relies on the fact that the real forger must at least generate hash queries to random oracle satisfying \(q_2\ge 1\) (or \(q_n\ge 1\) in the full scheme). This is guaranteed by the assumption that the real forger is able to forge a valid signature. Suppose the aforementioned meta-reduction utilizes our constructed reducer \(\mathcal R'\). We stress that the simulated forger \(\mathcal{\overline{F}}\) is not able to generate hash queries satisfying \(q_2\ge 1\). Otherwise, it will be the real forger. During the first round before rewinding, the simulated forger \(\mathcal{\overline{F}}\) should make some hash queries and signature queries. When the simulated forger \(\mathcal{\overline{F}}\) rewinds the interaction, it is worth noting that \(\mathcal{\overline{F}}\) must rewind \(\mathcal R'\) to the state after the hash queries. This is because if it rewinds \(\mathcal R'\) to the state before the hash queries, all hash values before and after the rewinding will be completely different in the random oracle model and hence the simulated forger \(\mathcal{\overline{F}}\) cannot use one of queried signatures to derive the forged signature. That is, all previous hash queries are not changed and the simulated forger \(\mathcal{\overline{F}}\) could query more. Finally, even the simulated forger \(\mathcal{\overline{F}}\) returns a valid signature indistinguishable from the one generated by the real forger, we still have that the hash queries do not satisfy the requirement of \(q_2\ge 1\). In this case, the reducer \(\mathcal R'\) fails and the meta-reduction breaks down, because the simulated forger \(\mathcal{\overline{F}}\) cannot solve an underlying hard problem.
2 Preliminaries
2.1 Definition of Digital Signatures
A digital signature scheme \(\mathsf{Sig=(SysGen, KeyGen, Sig, Verify)}\) consists of the following four algorithms:
SysGen \( (1^{\lambda }) \). Taking as input a security parameter \(1^ \lambda \), this system generation algorithm returns the system parameters params.
KeyGen(params). Taking as input the system parameters params, this key generation algorithm returns a public/secret key pair (pk, sk).
Sign (params, sk, m). Taking as input the system parameters params, a secret key sk and a message m, this signing algorithm returns a signature of m denoted by \(\varSigma _m\).
Verify \((params, pk, \varSigma _m,m)\). Taking as input the system parameters params, a public key pk, a signature \(\varSigma _m\) and a message m, this verification algorithm outputs 0 (reject) or 1 (accept).
We say that a signature is \(valid \) if \(\mathbf{Verify}(params, pk,\varSigma _m,m)=1\) for all generated system parameters params, public key pk and any message m. In the rest of paper, we omit the input of the system parameters params in the signing algorithm and the verification algorithm unless otherwise stated explicitly.
2.2 Definition of Unique Signatures and Efficiently Re-Randomizable Signatures
Given a public key pk and a message m, we denote
as the set of signatures \(\varSigma _m\) with regards to the message m and the public key pk under the system parameters params. In particular, this signature set could be associated with specific instantiations of hash functions adopted as part of system parameters. This notion was introduced in [3] to define unique signatures and re-randomizable signatures.
Definition 1
(Unique Signatures). A signature scheme is unique if
holds for all public keys under the system parameters params and all messages.
Definition 2
(Efficiently Re-Randomizable Signatures). A signature scheme is efficiently re-randomizable with t-re-randomizable, if there exists an efficient algorithm \(\mathsf{ReRand}\) running in polynomial time at most t, such that for all \((pk, \varSigma _m, m)\) under the system parameters params with \( \mathbf{Verify}(pk,\varSigma _m,m)=1 \) holds that the output distribution of
is identical to the uniform distribution over \( \varSigma (pk,m) \).
Unique signatures are a particular case of efficiently re-randomizable signatures where
Therefore, the efficiently re-randomizable signatures can be seen as the generalization of unique signatures. An important requirement of efficiently re-randomizable signatures is the uniform distribution over \(\varSigma (pk,m)\). Generally speaking, efficiently re-randomizable signatures are signatures whose random salts used in signature generations can be changed uniformly without the knowledge of the secret key, such that we cannot use a random salt to switch signatures between simulatable and reducible. That is, all signatures on the same message must be either simulatable or reducible. Therefore, all efficiently re-randomizable signatures are believed to have optimal security reductions with a loss factor of at least \(q_s\), same as unique signatures.
2.3 Security Model
We recall the notion of existential unforgeability against chosen message attacks (EU-CMA) played between a challenger and an adversary \(\mathcal {A}\).
Setup: The challenger runs the SysGen algorithm to generate the system parameters params and runs the KeyGen algorithm to generate a key pair (pk, sk). The system parameters and the public key pk are sent to the adversary.
Signature-Query: The adversary sequentially asks the signature of any message that is adaptively chosen by the adversary. To query the signature of m, \(\mathcal {A}\) submits the message m to the challenger. The challenger runs the Sign algorithm and returns a signature \(\varSigma _{m}\) of m to the adversary.
Forgery: The adversary outputs a message \(m^*\) and the corresponding signature \(\varSigma _{m^*}\). It wins the game if \( \varSigma _{m^*} \) is a valid signature of \(m^*\) and \(m^*\) has never been queried for its signature.
We refer to such adversary as an EU-CMA adversary and define the advantage of \(\mathcal {A}\) in winning the above game as
Definition 3
We say that a signature scheme \(\mathsf{Sig}\) is \((t,q_s,\epsilon )\)-secure in the EU-CMA security model if any PPT adversary \(\mathcal {A}\) who runs in t polynomial time and makes at most \(q_s\) signature queries has advantage at most \(\epsilon \) in winning the game, where \(\epsilon \) is negligible function of the input security parameter.
2.4 Complexity Assumption
Let \(\mathbb {PG}=(\mathbb {G},\mathbb {G}_T, p,e, g)\) be a pairing group where p is the order of the groups \(\mathbb {G}, \mathbb {G}_T\), \(e: \mathbb {G}\times \mathbb {G}\rightarrow \mathbb {G}_T\) is the bilinear map and g is a generator of \(\mathbb {G}\). Our proposed unique signature scheme is based on the BLS signature scheme in the symmetric pairing stated in \(\mathbb {PG}\). The underlying hard assumption for our scheme is the Computational Diffie-Hellman (CDH) assumption, which says it is hard to compute \(g^{ab}\) from a given instance \((g,g^a, g^b)\) in the pairing group \(\mathbb {PG}\), where a, b are unknown and uniformly chosen from the space \(\mathbb {Z}_p\). The formal definition of the CDH assumption is omitted here.
3 The Full Counterexample of Unique Signature Scheme
Our full unique signature scheme is described as follows.
SysGen: The system generation algorithm takes as input a security parameter \(1^\lambda \) and a small integer n. It chooses a pairing group \(\mathbb {PG}=(\mathbb {G},\mathbb {G}_T, p,e, g)\) and a cryptographic hash function \(H:\{0,1\}^*\rightarrow \mathbb {G}\) that will be viewed as a random oracle in the security proof. The system parameters params are composed of (\(\mathbb {PG}\), H, n). A signature will be composed of \(n+1\) block signatures.
KeyGen: The key generation algorithm randomly chooses \(\alpha \in \mathbb {Z}_p\) and computes \(h=g^{\alpha }\). The algorithm returns a public/secret key pair \((pk,sk)=(h, \alpha )\).
Sign: The signing algorithm takes as input the system parameters params, a message \(m\in \{0,1\}^*\) and the secret key sk. It returns the signature \(\varSigma _m\) on m as
where \(\varSigma _m^i=(\sigma _1, \sigma _1, \cdots , \sigma _{i})\) and the final signature \(\varSigma _m\) is equivalent to \(\varSigma _m^{n+1}\).
Verify: The verification algorithm takes as input the system parameters params, a signed message \((m,\varSigma _m)\) and the public key pk. It accepts the signature if and only if the \(n+1\) pairing computations are correct. That is, \(e(\sigma _1,g)=e(H(m), h)\) and \(e(\sigma _{i+1}, g)=e(H(m||\varSigma _m^i), h)\) holds for all \(i=1,2,\cdots , n\).
4 Two Essential Lemmas for Security Reduction
Let \(m\in \{0,1\}^*\) be a message and \(\mathcal {M}_0, \mathcal {M}_1, \mathcal {M}_2, \cdots , \mathcal {M}_n\) be \(n+1\) message sets defined as follows.
-
The message set \(\mathcal {M}_{i+1}\) is a subset of \(\mathcal {M}_{i}\) for all \(i=0,1,2,\cdots , n-1\).
$$\begin{aligned} \mathcal {M}_{n}\subseteq \mathcal {M}_{n-1}\subseteq \mathcal {M}_{n-2} \subseteq \cdots \subseteq \mathcal {M}_{1}\subseteq \mathcal {M}_0. \end{aligned}$$ -
The set \(\mathcal {M}_i\) has \(q_i\) distinct messages and is composed of \(\{m_{i,1}, m_{i, 2}, \cdots , m_{i,q_i}\}\).
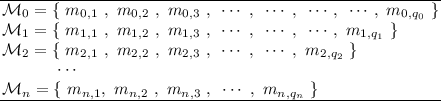
We have the following two essential lemmas based on the above message set definitions for our security reduction. The first lemma is proposed for proving the second lemma.
Lemma 1
(Range Lemma). Suppose \(q_0< q\) and \(q_n\ge 1\). There exists an integer \(i^*\in [0,n-1]\) satisfying
Proof of Lemma 1. We use a proof via contradiction to prove the existence of \(i^*\). If the integer \(i^*\) does not exist, it means
holds for all \(i=0, 1,2,3, \cdots , n-1\).
For any integer \(j\in [1,n-1]\), we have
-
When \(i=j-1\), it means
$$\begin{aligned} q_{j-1}\ge q^{1-\frac{j-1}{n}} \text{ or } q_{j}< {q^{1-\frac{j}{n}}}. \end{aligned}$$ -
When \(i=j\), it means
$$\begin{aligned} q_{j}\ge q^{1-\frac{j}{n}} \text{ or } q_{j+1}< {q^{1-\frac{j+1}{n}}}. \end{aligned}$$
That is, we have
It indicates that
When \(i=n-1\), we also have
Since \( q_{n}< {q^{1-\frac{n}{n}}}=1\) contradicts with the assumption \(q_n\ge 1\), we therefore have \(q_{n-1}\ge q^{1-\frac{n-1}{n}}\) and deduct
The deduction \(q_0\ge q^{1-\frac{0}{n}}=q\) contradicts with the assumption \(q_0<q\). Therefore, the assumption at the beginning of the proof is wrong and hence the integer \(i^*\in [0, n-1]\) exists. This completes the proof. \(\Box \)
Lemma 2
(Probability Lemma). Suppose \(q_0< q\) and \(q_n\ge 1\). If we randomly choose two integers \((c^*, k^*)\) satisfying \(c^*\in [0,n-1]\) and \(k^*\in [1, q^{1-\frac{c^*}{n}}]\), then the target message \(m_{c^*, k^*}\in \mathcal {M}_{c^*}\) will appear in the message set \(\mathcal {M}_{c^*+1}\) with probability at least
for any \(n+1\) defined message sets \(\mathcal {M}_0, \mathcal {M}_1, \mathcal {M}_2, \cdots , \mathcal {M}_n\). Here, if the chosen message \(m_{c^*, k^*}\notin \mathcal {M}_{c^*}\) (the size of message set is less than \(k^*\)), we define \(m_{c^*, k^*}\notin \mathcal {M}_{c^*+1}\).
Proof of Lemma 2. Let \(\Pr [Success]\) be the success probability that the chosen message \(m_{c^*, k^*}\in \mathcal {M}_{c^*}\) also appears in the message set \(\mathcal {M}_{i^*+1}\). We are going to prove
The success probability is associated with the choice of \((c^*, k^*)\), where \(c^*\) is randomly chosen from \([0,n-1]\). Hence, we have \(\Pr [c^*=i]=\frac{1}{n}\) for any \(i\in [0,n-1]\). According to the setting, we have
where \(i^*\) is the integer defined in Lemma 1.
According to Lemma 1, we have
When \(c^*=i^*\), the target message \(m_{c^*, k^*}\) is chosen from the \(k^*\)-th message of the message set \(\mathcal {M}_{i^*}\). Since \(|\mathcal {M}_{i^*}|< q^{1-\frac{i^*}{n}}\) and \(k^*\) is randomly chosen from \([1, q^{1-\frac{i^*}{n}}]\), any message in \(\mathcal {M}_{i^*}\) will be selected as the target message with probability \(1/q^{1-\frac{i^*}{n}}\). Furthermore, since \(\mathcal {M}_{i^*+1}\subseteq \mathcal {M}_{i^*}\), the success event will happen when \(m_{c^*, k^*}\) also appears in \(\mathcal {M}_{i^*+1}\). There are \(q_{i^*+1}\) messages in \(\mathcal {M}_{i^*+1}\) and hence we have the success probability
This completes the proof. \(\Box \)
5 Security Proof with a Tight Reduction
In this section, we prove the proposed full unique signature scheme is secure under the CDH assumption in the EU-CMA security model with a tight reduction, where H is set as a random oracle in the security proof.
Theorem 1
Let H be a random oracle and q be the number of queries to the random oracle. If the proposed full signature scheme can be broken with \((t, q_s, \epsilon )\) in the EU-CMA model, the CDH problem is solvable with
Proof. Suppose there exists an adversary \(\mathcal {A}\) who can break the signature scheme in the EU-CMA model. We construct a simulator \(\mathcal {B}\) that uses one of hash queries generated by the adversary to solve the CDH problem. Given as input the instance \((g,g^a,g^b)\) in the pairing group \(\mathbb {PG}\), the simulator aims to compute \(g^{ab}\). \(\mathcal {B}\) interacts with the adversary as follows.
Setup: The system parameters are the pairing group \(\mathbb {PG}\) and the integer n, where H is set as a random oracle controlled by the simulator. For the key pair, the simulator sets \(\alpha =a\) and hence the public key \(h=g^{\alpha }=g^a\) is available from the instance. The system parameters and the public key are sent to the adversary.
Hash-Query: We state how to simulate the random oracle here. The adversary can access the random oracle any time, such as after the signature query. We note that the random oracle simulation is the core of our proof for having a tight reduction.
Before simulating the random oracle, the simulator firstly chooses a random integer \(c^*\in [0,n-1]\) and then chooses another random value \(k^*\) from the range
In particular, we have the range is [1, q] when \(c^*=0\) and the range is \([1,q^{\frac{1}{n}}]\) when \(c^*=n-1\). The size of range for \(k^*\) is dependent on the integer \(c^*\).
Let \(\mathcal {L}\) be the list which records all queries and responses. Each query and its response are stored in a tuple. For each tuple, the format is
which is explained as follows.

For a query on x, if there already has a tuple \((x, ~I_x,~T_x, O_x,~U_x,~z_x)\) in the list, the simulator responds with \(U_x\). Otherwise, the simulator responds to this new query as follows.
Response of object \(I_x\). The object \(I_x\) is to identify who first time generates and submits x to the random oracle. For easy understanding, we comprehend the query in the way that both the adversary and the simulator can query to the random oracle, although the random oracle is controlled by the simulator. If a query on x is first time generated and submitted by the adversary, we say this query is made by the adversary and set \(I_x=\mathcal {A}\). Otherwise, we set \(I_x=\mathcal {B}\).
Taking a new message m as the example. Suppose the adversary firstly queries H(m), \(H(m||\varSigma ^1_m), H(m||\varSigma ^2_m)\) to the random oracle and then queries the signature of m to the simulator. Notice that the signature generation on the message m requires to know all the following values
The hash list does not record how to respond to hash queries \(H(m||\varSigma _m^i)\) for all \(i=3,4, \cdots , n\). Therefore, the simulator must add all these hash queries to the random oracle first before generating its signature. Notice that the hash queries \(H(m||\varSigma _m^3), \cdots \), \(~H(m||\varSigma _m^n)\) could be made by the adversary again for signature verification, but they are first time generated and made by the simulator. Hence, we define
-
For any \(x\in \{m, ~m||\varSigma _m^1, ~m||\varSigma _m^2\}\), the corresponding \(I_x\) for x is \(I_x=\mathcal {A}\).
-
For any \(x\in \{m||\varSigma _m^3, \cdots , m ||\varSigma _m^n\}\), the corresponding \(I_x\) for x is \(I_x=\mathcal {B}\).
Response of object \(T_x\). We assume “||” is a concatenation notation that will never appear within messages after encoding (See the footnote in the introduction section to know how to achieve it.). The simulator can also run the verification algorithm to verify whether each block signature is correct or not. Therefore, it is easy to distinguish the input structure of all hash queries. We define \(n+2\) types of hash queries to the random oracle.
- Type i.:
-
\(x=m||\varSigma _m^i\). Here, \(\varSigma _m^i\) denotes the first i block signatures of m and i refers to any integer \(i\in [0,n]\). We assume \(m||\varSigma _m^0=m\) without “||” in x for easy analysis.
- Type D.:
-
x is a query different from the previous \(n+1\) types. For example, \(x=m||R_m\) but \(R_m \ne \varSigma _m^i\) for any \(i\in [1,n]\), or \(x=m||\varSigma _m^{i'}\) for any \(i'\ge n+1\).
The object \(T_x\) is set as follows.
-
If \(I_x=\mathcal {B}\), then \(T_x=\bot \).
-
Otherwise, suppose \(I_x=\mathcal {A}\). Then, the simulator can run the verification algorithm to know which type x belongs to and set
$$ T_x=\left\{ \begin{array}{cl} i &{}~~~~ \text{ if } \text{ x } \text{ belongs } \text{ to } \text{ Type } \text{ i } \text{ for } \text{ any } i\in [0,n] \\ \bot &{}~~~~\text{ otherwise } \text{ x } \text{ belongs } \text{ to } \text{ Type } \text{ D } \end{array} \right. {.} $$
We emphasize that \(T_x\) and \(O_x\) are used to mark “valid” queries generated by the adversary only, which will be used in signature generation. We define Type D is to match the truth that the adversary can generate any arbitrary string as a query to the random oracle. Notice that the last type of queries will never be used in signature generation or signature forgery.
Response of object \(O_x\). The object \(O_x\) is set as follows.
-
If \(T_x=\bot \), then \(O_x=\bot \).
-
Otherwise, suppose \(T_x=c\). Then, \(O_x=k\) if x is the k-th new query added into the list \(\mathcal {L}\) in those queries where \(T_x=c\).
To calculate the integer k for the new query x, the simulator must count how many queries have been added in \(\mathcal {L}\), where only those queries with the same \(T_x\) will be counted. We emphasize that the setting of \(O_x\) needs to know the value \(T_x\) first.
For the objects \(I_x, T_x\) and \(O_x\) on the query x, there are only three cases in all tuples in the list.
where \(c\in [0,n]\) and \(k\in [1, q]\).
Response of objects \((U_x,z_x)\). Let \((I_x, T_x, O_x)\) be the response to the query x according to the above description. The simulator randomly chooses \(z_x\in \mathbb {Z}_p\) and sets the response \(U_x\) to x according to the chosen \((c^*, k^*)\) as follows.
We use \(z_x\) to denote the secret for response to x. In the following, if the query x needs to be written as \(x=m||\varSigma _m^i\), the corresponding secret will be rewritten as \(z_{m}^i\).
Finally, the simulator adds the defined tuple \((x, I_x, T_x, O_x, U_x, z_x)\) for the new query x to the list. This completes the description of the hash query and its response.
For the tuple \((x, I_x, T_x, O_x, U_x, z_x)\), we have \(H(x)^{\alpha }=U_x^a=(g^a)^{z_x}\) is computable by the simulator for any query x as long as \((T_x, O_x)\ne (c^*, k^*)\). Notice that when \((T_x, O_x)=(c^*, k^*)\), we have
For the tuple \((x, I_x, T_x, O_x, U_x, z_x)\), we use \(m_{i,j}\) to denote the message in the query input x if \((T_x,O_x)=(i,j)\). We define
to be the message set with \(q_i\) messages, where \(\mathcal {M}_i\) contains all messages in those tuples with \(T_x=i\). According to the setting of oracle response, for those hash queries belonging to Type i for all \(i\in [0,n]\), there have \(n+1\) message sets \(\mathcal {M}_0,~\mathcal {M}_1, ~\mathcal {M}_2\), \(~\cdots ,~\mathcal {M}_n\) at most to capture all messages in these queries.
Without knowing the signature \(\varSigma _m\) of m, the adversary must make hash queries H(m), \(H(m||\varSigma _m^1), H(m||\varSigma _m^2), \cdots , H(m||\varSigma _m^n)\) in sequence because \(\varSigma _m^i\) in the query \(m||\varSigma _m^i\) contains
For a message before its signature query, the adversary could not query all \(n+1\) hash queries for this message. Therefore, we have the following inequality and subset relationship hold.
All queried messages mentioned above can be described in Table 3. Suppose the adversary can finally forge a valid signature on a message \(m^*\). The adversary must at least make the hash query \(H(m^*||\varSigma _{m^*}^n)\) in order to compute \(H(m^*||\varSigma _{m^*}^n)^{\alpha }\), which guarantees \(q_n\ge 1\). Since the number of hash queries is of at most q, we have \(q_0< q\).
The queried messages in \(n+1\) message sets fulfill the message set description in Sect. 4. Since \(q_n\ge 1 \) and \(q_0< q\), we have the Range Lemma and the Probability Lemma can also be applied to the above message sets, even these message sets are adaptively generated by the adversary.
Signature-Query: For a signature query on the message m that is adaptively chosen by the adversary, the simulation is described as follows.
If m is never queried to the random oracle, the simulator works as follows from \(i=1\) to \(i=n+1\), where i is increased by one for each time.
-
Add a query on \(m||\varSigma _m^{i-1}\) to the list (We define \(m||\varSigma _m^0=m\)). According to the setting of the random oracle simulation, we have the corresponding tuple is
$$\begin{aligned} (m||\varSigma _m^{i-1}, ~\mathcal {B},~ \bot ,~ \bot , ~g^{z_m^{i-1}}, ~z_m^{i-1}). \end{aligned}$$ -
Compute the block signature \(\sigma _{i}\) as
$$\begin{aligned} \sigma _{i}=H(m||\varSigma _m^{i-1})^{\alpha } = (g^{a})^{z_m^{i-1}}. \end{aligned}$$
Notice that \(\sigma _{i}\) for all i are computable by the simulator and the signature of \(\varSigma _m\) is equal to \(\varSigma _m^{n+1}=(\sigma _0, \sigma _1, \cdots , \sigma _{n+1})\). Therefore, the signature of m is computable by the simulator.
Suppose the message m is ever queried to the random oracle by the adversary, where the following queries associated with the message m are made by the adversary
Here, the integer \(r_m\) is adaptively decided by the adversary. Let \((x, I_x, T_x, O_x, U_x, z_x)\) be the tuple for \(x=m||\varSigma _m^{r_m}\). That is, \(T_x=r_m\).
-
If \( (T_x, O_x)= (c^*, k^*)\), the simulator aborts because
$$\begin{aligned} H(m||\varSigma _m^{r_m})=g^{bz_x},~~\sigma _{r_m+1}=H(m||\varSigma _m^{r_m})^{\alpha }=U_x^{a}=(g^{bz_x})^a=(g^{ab})^{z_x}, \end{aligned}$$which cannot be computed by the simulator and hence the simulator fails in simulating the signature for the adversary, especially the block signature \(\sigma _{r_m+1}\).
-
Otherwise, \( (T_x, O_x)\ne (c^*, k^*)\). Then, \(\sigma _{r_m+1}\) is computable by the simulator because
$$\begin{aligned} H(m||\varSigma _m^{r_m})=g^{z_x},~~\sigma _{r_m+1}=H(m||\varSigma _m^{r_m})^{\alpha }=(g^a)^{z_x}. \end{aligned}$$Similarly to the case that m is never queried to the random oracle, the simulator can generate and make hash queries
$$\begin{aligned} H(m||\varSigma _m^{r_m+1}),~~H(m||\varSigma _m^{r_m+2}), \cdots , H(m||\varSigma _m^n) \end{aligned}$$to the random oracle. Finally, it computes the signature \(\varSigma _m\) for the adversary.
This completes the description of signature simulation. Once the simulator generates the signature of m, it forwards the signature to the adversary. It is easy to verify that the computed signature is a valid signature.
Forgery: The adversary outputs a valid signature \(\varSigma _{m^*}\) on a message \(m^*\) that is not asked for a signature. Since the adversary cannot make a signature query on \(m^*\), we have the following queries to the random oracle were made by the adversary
The solution to the hard problem does not have to be associated with the forged message \(m^*\). The simulator solves the hard problem as follows.
-
The simulator searches \(\mathcal {L}\) to find the first tuple \((x, I_x, T_x, O_x, U_x, z_x)\) satisfying
$$\begin{aligned} (T_x, O_x)=(c^*, k^*). \end{aligned}$$If this tuple does not exist, abort. Otherwise, let the message \(m_{c^*, k^*}\) in this tuple be denoted by \(\hat{m}\) for short. That is, \(m_{c^*, k^*}=\hat{m}\) and we have \(\hat{m}\in \mathcal {M}_{c^*}\). We note that \(\hat{m}\) could be different from \(m^*\). This tuple therefore is equivalent to
$$\begin{aligned} (x, I_x, T_x, O_x, U_x, z_x)=\Big (\hat{m}||\varSigma _{\hat{m}}^{c^*},~ \mathcal {A},~c^*,~k^*,~ g^{bz_{\hat{m}}^{c^*}},~z_{\hat{m}}^{c^*}\Big ). \end{aligned}$$That is \(H(\hat{m}||\varSigma _{\hat{m}}^{c^*})=g^{bz_{\hat{m}}^{c^*}}\) contains the instance \(g^b\).
-
The simulator searches \(\mathcal {L}\) to find the second tuple \((x', I_{x'}, T_{x'}, O_{x'}, U_{x'}, z_{x'})\), where \(x'\) is the query about the message \(\hat{m}\) and \(T_{x'}=c^*+1\). If this tuple does not exist, abort. Otherwise, we have \(\hat{m}\in \mathcal {M}_{c^*+1}\) and
$$\begin{aligned} x'=\hat{m}||\varSigma _{\hat{m}}^{c^*+1}, \end{aligned}$$where \(\varSigma _{\hat{m}}^{c^*+1}\) contains \(\sigma _{c^*+1}=H(m||\varSigma _{m}^{c^*})^{\alpha }\).
-
The simulator computes and outputs
$$\begin{aligned} \Big ( H(\hat{m}||\varSigma _{\hat{m}}^{c^*})^{\alpha }\Big )^{\frac{1}{z_{\hat{m}}^{c^*}}}=\Big ( g^{abz_{\hat{m}}^{c^*}}\Big )^{\frac{1}{z_{\hat{m}}^{c^*}}}=g^{ab} \end{aligned}$$as the solution to the CDH problem.
Analysis. This completes the description of simulation and solution. The scheme simulation is indistinguishable from the real scheme because the signing key \(\alpha \) is simulated using the random exponent a in the instance and there is no random number in the signature simulation. The random oracle response is correct because the response \(U_x\) to each query x is computed using a random integer \(z_x\), independent of other integers.
According to the assumption, the adversary will break the signature scheme with advantage \(\epsilon \). We have the adversary will make the hash query \(H(m^*||\varSigma _{m^*}^{n})\) with probability at least \(\epsilon \),Footnote 6 such that \(m^*\in \mathcal {M}_n\) and hence \(q_n\ge 1\). The number of hash query is q. Since \(q_0+q_1+q_2+\cdots +q_n=q\), we have \(q_0<q\). Therefore, the conditions of the Probability Lemma hold with success probability \(\epsilon \) in our reduction.
The reduction is successful when the simulator does not abort in the query phase and the forgery phase. According to the setting of the simulation, we found
-
The simulator aborts in the query phase when \(m_{c^*, k^*}\in \mathcal {M}_{c^*}\) but \(m_{c^*, k^*}\notin \mathcal {M}_{c^*+1}\), because the simulator cannot compute the queried signature on the message \(m_{c^*, k ^*}\).
-
The simulator aborts in the forgery phase when \(m_{c^*, k^*}\notin \mathcal {M}_{c^*}\) because the simulator cannot embed \(g^b\) in the response to the query \(m_{c^*, k^*}\) under Type \(c^*\), or when \(m_{c^*, k^*}\notin \mathcal {M}_{c^*+1}\) because the solution to the CDH problem does not exist in the hash list.
Therefore, we have the reduction is successful when \(m_{c^*, k^*}\in \mathcal {M}_{c^*}\) and \(m_{c^*, k^*}\in \mathcal {M}_{c^*+1}\). According to the Probability Lemma, if \(q_0<q\) and \(q_n\ge 1\), we have \(\hat{m}=m_{c^*,k^*} \in \mathcal {M}_{c^*}\cap \mathcal {M}_{c^*+1}\) holds with probability \(1/({nq^{\frac{1}{n}}})\). Therefore, the reduction is successful and the simulator can solve the hard problem with success probability at least \(\epsilon /({nq^{\frac{1}{n}}})\).
The simulation time is mainly dominated by the signature simulation, where all signature computations cost \(O(n\cdot q_s)\) point multiplications. Notice that the simulation time does not consider the time cost of oracle responses. This completes the proof. \(\Box \)
Very recently, the work of [13] showed how to find a correct solution to a computational hard problem from hash queries for encryption schemes under the indistinguishability model. The loss factor is also \(nq^{\frac{1}{n}}\) with a similar chain-like structure in hash queries. However, we stress that the approaches towards tight reductions are totally different.
Remark 3
In the above probability analysis, we use the condition that the adversary can forge a valid signature to guarantee \(q_n\ge 1\), which is a desired condition in the Probability Lemma. We note that this condition is sufficient but not necessary in our reduction as long as \(q_n\ge 1\) holds.
6 Conclusion
Optimal security reductions with impossibility results of tight reductions for unique signatures and efficiently re-randomizable signatures have been well studied in the literature (Coron, Eurocrypt 2002; Hofheinz et al. PKC 2012; Bader et al., Eurocrypt 2016). It has been proved and claimed that any security reduction for a unique signature scheme or an efficiently re-randomizable signature scheme must loose a factor of at least \(q_s\) for \(q_s\) number of signature queries under a non-interactive assumption in the EU-CMA security model. In this work, we pointed out that their optimal security reductions cannot cover all security reductions and proposed a counterexample with a tight reduction in the random oracle model. We can program the security reduction with a very small loss factor, e.g., 100, for \(2^{50}\) hash queries to random oracles under the CDH assumption in the EU-CMA security model. We stress that our counterexample just bypasses the given proofs of optimal security reduction, because the proofs via meta-reduction break down in our query-based reduction. The given counterexample implies a new way of constructing a signature scheme with a tight reduction in the random oracle model from a signature scheme with a loose reduction. This transformation is universal and also applicable for unique signatures. This transformation method is somewhat impractical because of inefficiency due to the growth of signature length by n times. Nevertheless, this is the first method for enabling a tight proof without the use of a random salt in the signature generation.
Notes
- 1.
Kakvi and Kiltz in [16] proposed a conceptual level FDH (Full Domain Hash) unique signature scheme with a tight reduction. The proposed RSA-FDH scheme is a unique signature, while the reduction uses a fake but indistinguishable public key in the simulation such that the simulated RSA-FDH signatures are no longer unique. We note that both real signature scheme and simulated signature scheme in our counterexample are unique signatures.
- 2.
For easy understanding, we assume \(q^{\frac{1}{2}}\) and \(q^{\frac{1}{n}}\) are both integers for the query number q and the given number n in discussions.
- 3.
We emphasize that the corresponding security reduction is different when the adopted block signature is changed. In particular, how to simulate a block signature and how to solve a hard problem are dependent on the block signature. However, the reduction method with a tight reduction is the same.
- 4.
This can be done via encoding to make sure m does not contain the concatenation notation. For example, each bit \(X\in \{0,1\}\) of message and block signatures will be encoded into “0X” and the concatenation notation is represented using “11” such that the whole bit string as input to the hash function looks like ‘\(0X_10X_20X_3110X_40X_5\)”, where \(X_1X_2X_3\) is the message and \(X_4X_5\) is the block signature. We can force the scheme to use this encoding before hashing and signature generation. In the security proof, if a query made by the adversary does not use this encoding, this query is a query with an invalid structure and the simulator will randomly respond to the hash query because it will not be used in signature query or signature forgery.
- 5.
The word “contain” here means that a group element can be extracted from another group element. For example, \(H(x)=(g^b)^z\) where \(z\in \mathbb {Z}^*_p\) is a random number chosen by the simulator. Then, we have \(g^{ab}\) can be extracted from \(H(x)^{\alpha }\) by computing \((H(x)^{\alpha })^{\frac{1}{z}}\).
- 6.
The adversary can forge a valid signature via randomly choosing group elements as the forged signature without making the corresponding hash queries. However, the success probability is less than 1 / p. The actual probability of making such a hash query is \(\epsilon -1/{p}\). Since 1 / p is negligible compared to \(\epsilon \), we simplify the probability \(\epsilon -1/{p}\) into \(\epsilon \).
References
Abdalla, M., Bellare, M., Rogaway, P.: The oracle diffie-hellman assumptions and an analysis of DHIES. In: Naccache, D. (ed.) CT-RSA 2001. LNCS, vol. 2020, pp. 143–158. Springer, Heidelberg (2001). doi:10.1007/3-540-45353-9_12
Abdalla, M., Fouque, P.-A., Lyubashevsky, V., Tibouchi, M.: Tightly-secure signatures from lossy identification schemes. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 572–590. Springer, Heidelberg (2012). doi:10.1007/978-3-642-29011-4_34
Bader, C., Jager, T., Li, Y., Schäge, S.: On the impossibility of tight cryptographic reductions. In: Fischlin, M., Coron, J.-S. (eds.) EUROCRYPT 2016. LNCS, vol. 9666, pp. 273–304. Springer, Heidelberg (2016). doi:10.1007/978-3-662-49896-5_10
Bellare, M., Rogaway, P.: The exact security of digital signatures-how to sign with RSA and rabin. In: Maurer, U. (ed.) EUROCRYPT 1996. LNCS, vol. 1070, pp. 399–416. Springer, Heidelberg (1996). doi:10.1007/3-540-68339-9_34
Bernstein, D.J.: Proving tight security for rabin-williams signatures. In: Smart, N. (ed.) EUROCRYPT 2008. LNCS, vol. 4965, pp. 70–87. Springer, Heidelberg (2008). doi:10.1007/978-3-540-78967-3_5
Blazy, O., Kakvi, S.A., Kiltz, E., Pan, J.: Tightly-secure signatures from chameleon hash functions. In: Katz, J. (ed.) PKC 2015. LNCS, vol. 9020, pp. 256–279. Springer, Heidelberg (2015). doi:10.1007/978-3-662-46447-2_12
Boneh, D., Lynn, B., Shacham, H.: Short signatures from the weil pairing. In: Boyd, C. (ed.) ASIACRYPT 2001. LNCS, vol. 2248, pp. 514–532. Springer, Heidelberg (2001). doi:10.1007/3-540-45682-1_30
Boyd, C., Carr, C.: Fair client puzzles from the bitcoin blockchain. In: Liu, J.K.K., Steinfeld, R. (eds.) ACISP 2016. LNCS, vol. 9722, pp. 161–177. Springer, Cham (2016). doi:10.1007/978-3-319-40253-6_10
Chevallier-Mames, B., Joye, M.: A practical and tightly secure signature scheme without hash function. In: Abe, M. (ed.) CT-RSA 2007. LNCS, vol. 4377, pp. 339–356. Springer, Heidelberg (2006). doi:10.1007/11967668_22
Coron, J.-S.: Optimal security proofs for PSS and other signature schemes. In: Knudsen, L.R. (ed.) EUROCRYPT 2002. LNCS, vol. 2332, pp. 272–287. Springer, Heidelberg (2002). doi:10.1007/3-540-46035-7_18
Goh, E., Jarecki, S., Katz, J., Wang, N.: Efficient signature schemes with tight reductions to the diffie-hellman problems. J. Cryptol. 20(4), 493–514 (2007)
Goldwasser, S., Micali, S., Rivest, R.L.: A digital signature scheme secure against adaptive chosen-message attacks. SIAM J. Comput. 17(2), 281–308 (1988)
Guo, F., Susilo, W., Mu, Y., Chen, R., Lai, J., Yang, G.: Iterated random oracle: a universal approach for finding loss in security reduction. In: Cheon, J.H., Takagi, T. (eds.) ASIACRYPT 2016. LNCS, vol. 10032, pp. 745–776. Springer, Heidelberg (2016). doi:10.1007/978-3-662-53890-6_25
Hofheinz, D., Jager, T.: Tightly secure signatures and public-key encryption. In: Safavi-Naini, R., Canetti, R. (eds.) CRYPTO 2012. LNCS, vol. 7417, pp. 590–607. Springer, Heidelberg (2012). doi:10.1007/978-3-642-32009-5_35
Hofheinz, D., Jager, T., Knapp, E.: Waters signatures with optimal security reduction. In: Fischlin, M., Buchmann, J., Manulis, M. (eds.) PKC 2012. LNCS, vol. 7293, pp. 66–83. Springer, Heidelberg (2012). doi:10.1007/978-3-642-30057-8_5
Kakvi, S.A., Kiltz, E.: Optimal security proofs for full domain hash, revisited. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 537–553. Springer, Heidelberg (2012). doi:10.1007/978-3-642-29011-4_32
Katz, J., Wang, N.: Efficiency improvements for signature schemes with tight security reductions. In: Jajodia, S., Atluri, V., Jaeger, T. (eds.) CCS 2003, pp. 155–164. ACM (2003)
Luu, L., Narayanan, V., Zheng, C., Baweja, K., Gilbert, S., Saxena, P.: A secure sharding protocol for open blockchains. In: Weippl, E.R., Katzenbeisser, S., Kruegel, C., Myers, A.C., Halevi, S. (eds.) ACM Conference on Computer and Communications Security 2016, pp. 17–30. ACM (2016)
Schäge, S.: Tight proofs for signature schemes without random oracles. In: Paterson, K.G. (ed.) EUROCRYPT 2011. LNCS, vol. 6632, pp. 189–206. Springer, Heidelberg (2011). doi:10.1007/978-3-642-20465-4_12
Zhang, F., Safavi-Naini, R., Susilo, W.: An efficient signature scheme from bilinear pairings and its applications. In: Bao, F., Deng, R., Zhou, J. (eds.) PKC 2004. LNCS, vol. 2947, pp. 277–290. Springer, Heidelberg (2004). doi:10.1007/978-3-540-24632-9_20
Acknowledgment
We would like to thank Yannick Seurin for his helpful comments to improve the clarity of this paper. We would also like to thank Tibor Jager for his insightful comments especially for helping identify the gap between the proofs of impossibilities and our example. Finally, we would like to thank anonymous reviewers of CRYPTO 2017 for their insightful comments which help us improve the quality of this work. This work was partially supported by ARC Discovery Early Career Researcher Award (DECRA) DE170100641.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 International Association for Cryptologic Research
About this paper
Cite this paper
Guo, F., Chen, R., Susilo, W., Lai, J., Yang, G., Mu, Y. (2017). Optimal Security Reductions for Unique Signatures: Bypassing Impossibilities with a Counterexample. In: Katz, J., Shacham, H. (eds) Advances in Cryptology – CRYPTO 2017. CRYPTO 2017. Lecture Notes in Computer Science(), vol 10402. Springer, Cham. https://doi.org/10.1007/978-3-319-63715-0_18
Download citation
DOI: https://doi.org/10.1007/978-3-319-63715-0_18
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-63714-3
Online ISBN: 978-3-319-63715-0
eBook Packages: Computer ScienceComputer Science (R0)



