Abstract
The famous Fiat-Shamir transformation turns any public-coin three-round interactive proof, i.e., any so-called \(\Sigma {\text {-protocol}}\), into a non-interactive proof in the random-oracle model. We study this transformation in the setting of a quantum adversary that in particular may query the random oracle in quantum superposition.
Our main result is a generic reduction that transforms any quantum dishonest prover attacking the Fiat-Shamir transformation in the quantum random-oracle model into a similarly successful quantum dishonest prover attacking the underlying \(\Sigma {\text {-protocol}}\) (in the standard model). Applied to the standard soundness and proof-of-knowledge definitions, our reduction implies that both these security properties, in both the computational and the statistical variant, are preserved under the Fiat-Shamir transformation even when allowing quantum attacks. Our result improves and completes the partial results that have been known so far, but it also proves wrong certain claims made in the literature.
In the context of post-quantum secure signature schemes, our results imply that for any \(\Sigma {\text {-protocol}}\) that is a proof-of-knowledge against quantum dishonest provers (and that satisfies some additional natural properties), the corresponding Fiat-Shamir signature scheme is secure in the quantum random-oracle model. For example, we can conclude that the non-optimized version of Fish, which is the bare Fiat-Shamir variant of the NIST candidate Picnic, is secure in the quantum random-oracle model.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
E.g., the underlying computational hardness assumption does not hold anymore in the context of a quantum adversary.
- 2.
In the (quantum) random-oracle model, statistical security considers a computationally unbounded attacker with a polynomially bounded number of oracle queries.
- 3.
The paper [LZ19] was put on eprint (ia.cr/2019/262) a few days after our eprint version (ia.cr/2019/190).
- 4.
Alternatively, we may understand \(|\phi _0\rangle \) as an auxiliary input given to \(\mathcal A\).
- 5.
If it is the final output that is measured then there is nothing left to reprogram.
- 6.
We consider \(|\mathcal{Y}|\) to be superpolynomial in the security parameter, so that \(\frac{1}{2(q+1)|\mathcal{Y}|}\) is negligible and can be neglected. In cases where \(|\mathcal{Y}|\) is polynomial, the presented bound is not optimal, but an improved bound can be derived with the same kind of techniques.
- 7.
Informally, these modifications mean that we let \(\mathcal A\) make one more query to get H(x) into register
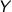 , and \(\tilde{G}_x^{H(x)}\) would then check that
, and \(\tilde{G}_x^{H(x)}\) would then check that 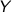 indeed contains H(x).
indeed contains H(x). - 8.
We recall that in case z is a quantum state, V is given by means of a measurement.
- 9.
In other words, \(\mathcal A\) is then non-uniform quantum polynomial-time with quantum advice.
- 10.
- 11.
See also Theorem 25 in [Unr17] for a different proof technique.
References
Alkim, E., et al.: Revisiting TESLA in the quantum random oracle model. In: Lange, T., Takagi, T. (eds.) PQCrypto 2017. LNCS, vol. 10346, pp. 143–162. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-59879-6_9
Abdalla, M., Fouque, P.-A., Lyubashevsky, V., Tibouchi, M.: Tightly-secure signatures from lossy identification schemes. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 572–590. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-29011-4_34
Ambainis, A., Rosmanis, A., Unruh, D.: Quantum attacks on classical proof systems: the hardness of quantum rewinding. In: 2014 IEEE 55th Annual Symposium on Foundations of Computer Science, pp. 474–483, October 2014
Boneh, D., Dagdelen, Ö., Fischlin, M., Lehmann, A., Schaffner, C., Zhandry, M.: Random oracles in a quantum world. In: Lee, D.H., Wang, X. (eds.) ASIACRYPT 2011. LNCS, vol. 7073, pp. 41–69. Springer, Heidelberg (2011). https://doi.org/10.1007/978-3-642-25385-0_3
Bos, J., et al.: CRYSTALS - Kyber: a CCA-secure module-lattice-based KEM. In: 2018 IEEE European Symposium on Security and Privacy (EuroS P), pp. 353–367, April 2018
Bellare, M., Goldreich, O.: On defining proofs of knowledge. In: Brickell, E.F. (ed.) CRYPTO 1992. LNCS, vol. 740, pp. 390–420. Springer, Heidelberg (1993). https://doi.org/10.1007/3-540-48071-4_28
Bellare, M., Rogaway, P.: Random oracles are practical: a paradigm for designing efficient protocols. In: Proceedings of the 1st ACM Conference on Computer and Communications Security, pp. 62–73. ACM (1993)
Chase, M., et al. Post-quantum zero-knowledge and signatures from symmetric-key primitives. In: Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, CCS 2017, pp. 1825–1842. ACM, New York (2017)
Canetti, R., Goldreich, O., Halevi, S.: The random oracle methodology, revisited. J. ACM 51(4), 557–594 (2004)
Damgard, I.: On sigma-protocols, Lecture Notes, Faculty of Science Aarhus University, Department of Computer Science (2010)
Dagdelen, Ö., Fischlin, M., Gagliardoni, T.: The Fiat–Shamir transformation in a quantum world. In: Sako, K., Sarkar, P. (eds.) ASIACRYPT 2013. LNCS, vol. 8270, pp. 62–81. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-42045-0_4
Eaton, E., Song, F.: Making existential-unforgeable signatures strongly unforgeable in the quantum random-oracle model. In: 10th Conference on the Theory of Quantum Computation, Communication and Cryptography, pp. 147 (2015)
Fehr, S.: Classical proofs for the quantum collapsing property of classical hash functions. In: Beimel, A., Dziembowski, S. (eds.) TCC 2018. LNCS, vol. 11240, pp. 315–338. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-03810-6_12
Faust, S., Kohlweiss, M., Marson, G.A., Venturi, D.: On the non-malleability of the Fiat-Shamir transform. In: Galbraith, S., Nandi, M. (eds.) INDOCRYPT 2012. LNCS, vol. 7668, pp. 60–79. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-34931-7_5
Fiat, A., Shamir, A.: How to prove yourself: practical solutions to identification and signature problems. In: Odlyzko, A.M. (ed.) CRYPTO 1986. LNCS, vol. 263, pp. 186–194. Springer, Heidelberg (1987). https://doi.org/10.1007/3-540-47721-7_12
Giacomelli, I., Madsen, J., Orlandi, C.: ZKBoo: faster zero-knowledge for Boolean circuits. In: 25th USENIX Security Symposium (USENIX Security 16), Austin, TX, pp. 1069–1083. USENIX Association (2016)
Ishai, Y., Kushilevitz, E., Ostrovsky, R., Sahai, A.: Zero-knowledge from secure multiparty computation. In: Proceedings of the Thirty-ninth Annual ACM Symposium on Theory of Computing - STOC 2007, p. 21 (2007)
Kiltz, E., Lyubashevsky, V., Schaffner, C.: A concrete treatment of Fiat-Shamir signatures in the quantum random-oracle model. In: Nielsen, J.B., Rijmen, V. (eds.) EUROCRYPT 2018. LNCS, vol. 10822, pp. 552–586. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-78372-7_18
Lyubashevsky, V.: Fiat-Shamir with aborts: applications to lattice and factoring-based signatures. In: Matsui, M. (ed.) ASIACRYPT 2009. LNCS, vol. 5912, pp. 598–616. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-10366-7_35
Lyubashevsky, V.: Lattice signatures without trapdoors. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 738–755. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-29011-4_43
Liu, Q., Zhandry, M.: Revisiting post-quantum Fiat-Shamir. Cryptology ePrint Archive, Report 2019/262 (2019). https://eprint.iacr.org/2019/262
Saito, T., Xagawa, K., Yamakawa, T.: Tightly-secure key-encapsulation mechanism in the quantum random oracle model. In: Nielsen, J.B., Rijmen, V. (eds.) EUROCRYPT 2018. LNCS, vol. 10822, pp. 520–551. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-78372-7_17
Unruh, D.: Quantum proofs of knowledge. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 135–152. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-29011-4_10
Unruh, D.: Quantum position verification in the random oracle model. In: Garay, J.A., Gennaro, R. (eds.) CRYPTO 2014. LNCS, vol. 8617, pp. 1–18. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-662-44381-1_1
Unruh, D.: Non-interactive zero-knowledge proofs in the quantum random oracle model. In: Oswald, E., Fischlin, M. (eds.) EUROCRYPT 2015. LNCS, vol. 9057, pp. 755–784. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-46803-6_25
Unruh, D.: Computationally binding quantum commitments. In: Fischlin, M., Coron, J.-S. (eds.) EUROCRYPT 2016. LNCS, vol. 9666, pp. 497–527. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-49896-5_18
Unruh, D.: Post-quantum security of Fiat-Shamir. In: Takagi, T., Peyrin, T. (eds.) ASIACRYPT 2017. LNCS, vol. 10624, pp. 65–95. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-70694-8_3
Zhandry, M.: How to construct quantum random functions. In: 2012 IEEE 53rd Annual Symposium on Foundations of Computer Science, pp. 679–687. IEEE, October 2012
Zhandry, M.: Secure identity-based encryption in the quantum random oracle model. Int. J. Quantum Inf. 13(04), 1550014 (2015)
Zhandry, M.: Quantum lightning never strikes the same state twice. http://arxiv.org/abs/1711.02276 (2017)
Zhandry, M.: How to record quantum queries, and applications to quantum indifferentiability. Cryptology ePrint Archive, Report 2018/276 (2018). https://eprint.iacr.org/2018/276
Acknowledgement
We thank Tommaso Gagliardoni and Dominique Unruh for comments on early basic ideas of our approach, and Andreas Hülsing, Eike Kiltz and Greg Zaverucha for helpful discussions. We thank Thomas Vidick for helpful remarks on an earlier version of this article.
JD and SF were partly supported by the EU Horizon 2020 Research and Innovation Program Grant 780701 (PROMETHEUS). JD, CM, and CS were supported by a NWO VIDI grant (Project No. 639.022.519).
Author information
Authors and Affiliations
Corresponding authors
Editor information
Editors and Affiliations
Appendices
A Proof of Lemmas 12 and 15
Proof
(of Lemma 12). Let \(\mathcal{A}\) be an adaptive \(\Sigma {\text {-protocol}}\) adversary, producing x and a in the first stage, and z in the second stage. We then consider the following algorithms. \(\mathcal{A}_{init}\) runs the first stage of \(\mathcal{A}\) (using the same initial state), outputting x and a. Let \(|\psi _{x,a}\rangle \) be the corresponding internal state at this point. Furthermore, for any possible x and a, \(\mathcal{A}_{x,a}\) is the following static \(\Sigma {\text {-protocol}}\) adversary. Its initial state is \(|\psi _{x,a}\rangle |a\rangle \) and in the first stage it simply outputs a, and in the second stage, after having received the verifier’s challenge, it runs the second stage of \(\mathcal{A}\). We then see that
Since \( \Pr \bigl [\langle \mathcal{A}_{x_\circ ,a} , \mathcal{V}(x_\circ ) \rangle = accept \bigr ]\) is bounded by a negligible function, given that \(\mathcal{A}_{x,a}\) is a (quantum polynomial-time/unbounded) static adversary, the claim follows. \(\square \)
Proof
(of Lemma 15). Let \(\mathcal{A}\) be an adaptive \(\Sigma {\text {-protocol}}\) adversary, producing x and a in the first stage, and z in the second stage. We construct a black-box knowledge extractor \(\mathcal{K}_{ad}\) that works for any such \(\mathcal{A}\). In a first step, \(\mathcal{K}_{ad}^\mathcal{A}\) runs the first stage of \(\mathcal{A}\) using the black-box access to \(\mathcal{A}\) (and having access to the initial state of \(\mathcal{A}\)). Below, we call this first stage of \(\mathcal{A}\) as \(\mathcal{A}_{init}\). This produces x and a, and we write \(|\psi _{x,a}\rangle \) for the corresponding internal state. Then, it runs \(\mathcal{K}_{na}^{\mathcal{A}^{x,a}}\), where \(\mathcal{K}_{na}\) is the knowledge extractor guaranteed to exist for static adversaries, and \(\mathcal{A}^{x,a}\) is the static adversary that works as follows. It’s initial state is \(|\psi _{x,a}\rangle |a\rangle \) and in the first stage it simply outputs a, and in the second stage it runs the second stage of \(\mathcal{A}\) on the state \(|\psi _{x,a}\rangle \). Note that having obtained x and a and the state \(|\psi _{x,a}\rangle \) as first step of \(\mathcal{K}_{ad}^\mathcal{A}\), \(\mathcal{K}_{na}^{\mathcal{A}^{x,a}}\) can then be executed with black box access to (the second stage of) \(\mathcal{A}\). For any subset \(X \subseteq \mathcal{X}\), we now see that
where the first inequality is because of the static proof-of-knowledge property, and the second is Jensen’s inequality, noting that we may assume without loss of generality that \(d \ge 1\). \(\square \)
B Generalization of Lemma 7 from [Unr12]
Lemma 29
Let \(P_1,\ldots ,P_n\) be projections and \(|\psi \rangle \) a state vector, and set
Then \(F \ge V^{2t-1}\).
The case \(t=2\) was proven in [Unr12, Lemma 7]. We show here how to extend the proof to \(t = 3\); the general case works along the same lines.
Proof
(of the case \(t = 3\)). For convenience, set \(A:= \frac{1}{n} \sum _i P_i\) and \(|\psi _{ijk}\rangle := P_k P_j P_i |\psi \rangle \). Then, using convexity of the function \(x \mapsto x^5\) to argue the first inequality, we get
where the last inequality is Claim 2 in the proof of Lemma 7 in [Unr12]. \(\square \)
Rights and permissions
Copyright information
© 2019 International Association for Cryptologic Research
About this paper
Cite this paper
Don, J., Fehr, S., Majenz, C., Schaffner, C. (2019). Security of the Fiat-Shamir Transformation in the Quantum Random-Oracle Model. In: Boldyreva, A., Micciancio, D. (eds) Advances in Cryptology – CRYPTO 2019. CRYPTO 2019. Lecture Notes in Computer Science(), vol 11693. Springer, Cham. https://doi.org/10.1007/978-3-030-26951-7_13
Download citation
DOI: https://doi.org/10.1007/978-3-030-26951-7_13
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-26950-0
Online ISBN: 978-3-030-26951-7
eBook Packages: Computer ScienceComputer Science (R0)


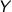 , and
, and 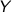 indeed contains H(x).
indeed contains H(x).