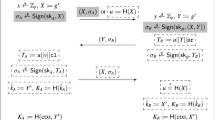
Abstract
The classical RSA is vulnerable to low private exponent attacks (LPEA) and has homomorphism. KMOV based on elliptic curve E n (a,b) over ℤ n can resist LPEA but still has homomorphism. QV over E n (a,b) not only can resist LPEA but also has no homomorphism. However, QV over E n (a,b) requires the existence of points whose order is M n = lcm{♯E p (a,b), ♯E q (a,b)}. This requirement is impractical for all general elliptic curves. Besides, the computation over En(a,b) is quite complicated. In this paper, we further study conic curve C n (a,b) over ℤ n and its corresponding properties, and advance several key theorems and corollaries for designing digital signature schemes, and point out that C n (a,b) always has some points whose order is M n = lcm{♯E p (a,b), ♯E q (a,b)}. Thereby we present an improved QV signature over C n (a,b), which inherits the property of non-homomorphism and can resist the Wiener attack. Furthermore, under the same security requirements, the improved QV scheme is easier than that over E n (a,b), with respect plaintext embedding, inverse elements computation, points computation and points’ order calculation. Especially, it is applicable to general conic curves, which is of great significance to the application of QV schemes.
Similar content being viewed by others
References
Koyama K, Maurer U, Okamoto T, et al. New public-key schemes based on elliptic curves over the ring ℤn. In: Feigenbaum J, ed. Advances in Cryptology-CRYPTO’91, Lect Notes in Comput Sci. Santa Barbara: Springer-Verlag, 1992, 576:252–266
Qu M H, Vanstone S. On ID-based cryptosystems over ℤn. In: International Symposium on Number Theory of 2000. Chengdu, 2000. 13–26
Zhu W Y, Sun Q. The elliptic curves over ℤn and digital signature scheme (in Chinese). J Elect Inf Tech, 2003, 25: 40–47
Zhu W Y, Sun Q. The elliptic curve over ℤn and key exchange protocal (in Chinese). Acta Eletr Sin, 2005, 33(1): 83–87
Cao Z F. A public key cryptosystem based on a conic over finite fields \( \mathbb{F}_p \) (in Chinese). In:In: Advances in Cryptology Chinacypt’98. Beijing: Publishing House of Electronics Industry, 1998. 45–49
Cao Z F. Conic analog of RSA cryptosystem and some improved RSA cryptosystem (in Chinese). J Nat Sci Heilongjiang Univ, 1999, 4: 15–18
Sun Q, Zhu W Y, Wang B. The conic curves over ℤn and public key cryptosystem protocol (in Chinese). J Sichuan Univ (Nat Sci Ed), 2005, 42(3): 471–478
Wang B, Zhu W Y, Sun Q. Public key cryptosystem based on the conic curves over ℤn (in Chinese). J Sichuan Univ (Engin Sci Ed), 2005, 37(5): 112–117
Sun Q, Zhang Q F, Peng G H. An algorithm to compute the multiples of an element in a group and its application to public key cryptosystems (in Chinese). In: Advances in Cryptology Chinacypt’2002. Beijing: Publishing House of Electronics Industry 2002. 117–124
Hastad J. On using RSA with low exponent in a public key network. In: Williams H C, ed. Advances in Cryptology-CRYPTO 85. Lec Notes in Comput Sci. Santa Barbara: Springer-Verlag, 1986, 218: 403–408
Wiener M J. Cryptanalysis of short RSA secret exponents. IEEE Trans Inf Theory, 1990, 36(3): 553–558
Boneh D. Twenty years of attacks on RSA cryptosystem. Notices of the AMS, 1999, 46(2): 203–213
Sun Q, Pend G H, Zhu W Y. RSA-type cryptosystem based on conic curves over ℤn and resistance to short private exponent attacks (in Chinese). In: Advances in Cryptology Chinacypt’2006. Beijing: Publishing House of Science and Technology of China, 2006
Zhu W Y, Sun Q. Basis of computer cryptography application (in Chinese). Beijing: Publishing House of Science and Technology of China, 2007. 111–130
Author information
Authors and Affiliations
Corresponding author
Additional information
Supported by the National Natural Science Foundation of China (Grant No. 10128103)
Rights and permissions
About this article
Cite this article
Wang, B., Fang, Y., Lin, H. et al. The improved QV signature scheme based on conic curves over ℤ n . Sci. China Ser. F-Inf. Sci. 52, 602–608 (2009). https://doi.org/10.1007/s11432-009-0083-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11432-009-0083-z