Abstract
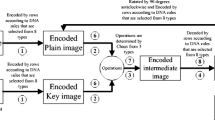
This paper proposes a novel image encryption algorithm based on chaos and DNA planes operations by utilizing one time pad. The plain image is firstly shuffled by means of “interweaving of ranks”. Next, we divided the permutated image into four sub-images with same size, and encode one of them by DNA rules. Decompose encoded image into four “DNA planes”, which means that every single pixel can compose four DNA units, for all pixels, four planes can be obtained. After that, shuffle each DNA plane respectively, decode these DNA planes and combine them back to a single quarter image. Finally, diffuse other three parts using resultant image from last step. Diffusion operations are achieved by exclusive or operation. Then, the four sub-images are combined into one image, which is the cipher image. In combination with the SHA3–512 hash, it is used to resist the basic requirements of the typical attack of the algorithm, and establishes the relationship between the initial value of the chaotic system and the plaintext image. Experimental results and numerical analysis show that the proposed algorithm can resist typical attacks, such as chosen-plaintext attack, et al., and has better character of security. The proposed algorithm can be used in image encryption.







Similar content being viewed by others
References
Al-Sharif S, Iqbal F, Baker T, et al. White-hat hacking framework for promoting security awareness. 2016 8th IFIP International Conference on New Technologies, Mobility and Security (NTMS) IEEE, 2016: 1–6
Asim M, Yautsiukhin A, Brucker AD et al (2018) Security policy monitoring of BPMN-based service compositions. Journal of Software: Evolution and Process 30(9):e1944
Assad SE, Farajallah M (2016) A new chaos-based image encryption system. Signal Process Image Commun 41:144–157
Bakhshandeh A, Eslami Z (2013) An authenticated image encryption scheme based on chaotic maps and memory cellular automata. Optics & Lasers in Engineering 51(6):665–673
Cao X, Du L, Wei X et al (2016) High capacity reversible data hiding in encrypted images by patch-level sparse representation. IEEE transactions on cybernetics 46(5):1132–1143
Chai X, Chen Y, Broyde L (2017) A novel chaos-based image encryption algorithm using DNA sequence operations. Optics & Lasers in Engineering 88:197–213
Enayatifar R, Abdullah AH, Isnin IF (2014) Chaos-based image encryption using a hybrid genetic algorithm and a DNA sequence. Optics & Lasers in Engineering 56(5):83–93
Faragallah OS (2015) Efficient confusion–diffusion chaotic image cryptosystem using enhanced standard map. Signal Image & Video Processing 9(8):1–10
George RT, Gopakumar K (2015) Spatiotemporal chaos in globally coupled NCA map lattices using 3-D Arnold cat map for digital image encryption. First international conference on computational systems and communications. IEEE, pp 203–208
Ghafir I, Saleem J, Hammoudeh M et al (2018) Security threats to critical infrastructure: the human factor. J Supercomput 74:4986–5002
Hua Z, Zhou Y (2017) Design of image cipher using block-based scrambling and image filtering. Inf Sci 396:97–113
Huang X, Ye G (2014) An image encryption algorithm based on hyper-chaos and DNA sequence. Multimedia Tools & Applications 72(1):57–70
Hussain I, Gondal MA (2014) An extended image encryption using chaotic coupled map and S-box transformation. Nonlinear Dynamics 76(2):1355–1363
Hussain AJ, Marcinonyte DM, Iqbal FI (2018) Et. al. smart home systems security. 2018 IEEE 20th international conference on high performance computing and communications; IEEE 16th international conference on Smart City; IEEE 4th international conference on data science and systems (HPCC/SmartCity/DSS). IEEE:1422–1428
Jain A, Rajpal N (2016) A robust image encryption algorithm resistant to attacks using DNA and chaotic logistic maps. Multimedia Tools & Applications 75(10):5455–5472
Kadir A, Hamdulla A, Guo WQ (2014) Color image encryption using skew tent map and hyper chaotic system of 6th-order CNN. Optik-International Journal for Light and Electron Optics 125(5):1671–1675
Karam Y, Baker T, Taleb-Bendiab A (2012) Security support for intention driven elastic cloud computing. In: Sixth UKSim/AMSS European symposium on computer modeling and simulation. IEEE, 2012, pp 67–73
Kumar M, Iqbal A, Kumar P (2016) A new RGB image encryption algorithm based on DNA encoding and elliptic curve Diffie-Hellman cryptography. Signal Process 125(C):187–202
Li C, Lin D, Lü J (2017) Cryptanalyzing an image-scrambling encryption algorithm of pixel bits. IEEE Multimedia 24(3):64–71
Liu W, Sun K, Zhu C (2016) A fast image encryption algorithm based on chaotic map. Optics & Lasers in Engineering 84:26–36
Mao Q, Chang CC, Wu HL (2013) An image encryption scheme based on concatenated torus automorphisms. KSII Transactions on Internet & Information Systems 7(6):1492–1511
Norouzi B, Seyedzadeh SM, Mirzakuchaki S et al (2014) A novel image encryption based on hash function with only two-round diffusion process. Multimedia Systems 20(1):45–64
Qin C, Zhou Q, Cao F et al (2018) Flexible lossy compression for selective encrypted image with image inpainting. IEEE Transactions on Circuits and Systems for Video Technology. https://doi.org/10.1109/TCSVT.2018.2878026
Seyedzadeh SM, Norouzi B, Mosavi MR et al (2015) A novel color image encryption algorithm based on spatial permutation and quantum chaotic map. Nonlinear Dynamics 81(1–2):511–529
Sivakumar T, Venkatesan R (2015) A novel image encryption using calligraphy based scan method and random number. KSII Transactions on Internet & Information Systems 9(6):2317–2337
Wang Q, Yu S, Li C et al (2015) Theoretical design and FPGA-based implementation of higher-dimensional digital chaotic systems. IEEE Transactions on Circuits & Systems I Regular Papers 63(3):401–412
Wang X, Liu C, Zhang H (2016) An effective and fast image encryption algorithm based on Chaos and interweaving of ranks. Nonlinear Dynamics 84(3):1595–1607
Wang XY, Zhang HL, Bao XM (2016) Color image encryption scheme using CML and DNA sequence operations. BioSystems 144:18–26
Wu Y, Zhang X, Peng C (2013) The capture and reduction Technology of Image Data based on HTTP protocol. Journal of Emerging Trends in Computing and Information Sciences 4(9):670–674
Xie EY, Li C, Yu S et al (2016) On the cryptanalysis of Fridrich's chaotic image encryption scheme. Signal Process 132:150–154
Zhang Y, Tang Y (2018) A plaintext-related image encryption algorithm based on chaos. Multimed Tools Appl 77(6):6647–6669
Zhang L, Zhu Z, Yang B et al (2015) Medical image encryption and compression scheme using compressive sensing and pixel swapping based permutation approach. Math Probl Eng 2015:1–9
Zhang X, Zhang H, Xu C (2016) Reverse iterative image encryption scheme using 8-layer cellular automata. KSII Transactions on Internet & Information Systems 10(7):3397–3413
Zhang X, Wang CQ, Zheng ZM (2017) An efficient chaotic image encryption algorithm based on self-adaptive model and feedback mechanism. KSII Transactions on Internet & Information Systems 11(3):1785–1801
Acknowledgements
This research is supported by the National Natural Science Foundation of China (Nos: 61672124, 61370145 and 61173183), the Password Theory Project of the 13th Five-Year Plan National Cryptography Development Fund (No: MMJJ20170203).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wang, X., Wang, Y., Zhu, X. et al. Image encryption scheme based on Chaos and DNA plane operations. Multimed Tools Appl 78, 26111–26128 (2019). https://doi.org/10.1007/s11042-019-07794-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-07794-9