Abstract
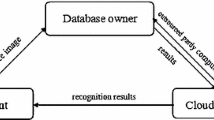
Recently, cloud storage and processing have been widely adopted. Mobile users in one family or one team may automatically backup their photos to the same shared cloud storage space. The powerful face detector trained and provided by a 3rd party may be used to retrieve the photo collection which contains a specific group of persons from the cloud storage server. However, the privacy of the mobile users may be leaked to the cloud server providers. In the meanwhile, the copyright of the face detector should be protected. Thus, in this paper, we propose a protocol of privacy preserving face retrieval in the cloud for mobile users, which protects the user photos and the face detector simultaneously. The cloud server only provides the resources of storage and computing and cannot learn anything of the user photos and the face detector. We test our protocol inside several families and classes. The experimental results reveal that our protocol can successfully retrieve the proper photos from the cloud server and protect the user photos and the face detector.







Similar content being viewed by others
Notes
References
Avidan S, Butman M (2006) Blind vision. In: Computer vision-ECCV, 9th European conference on computer vision, Graz, Austria, 7–13 May 2006, Proceedings, Part III, pp 1–13
Bost R, Popa RA, Tu S, Goldwasser S (2015) Machine learning classification over encrypted data. In: 22nd annual network and distributed system security symposium, NDSS, San Diego, California, USA, 8–11 Feb 2014
Chu C, Jung J, Liu Z, Mahajan R (2014) Strack: secure tracking in community surveillance. In: Proceedings of the ACM international conference on multimedia, MM’14, Orlando, FL, USA, 3–7 Nov 2014, pp 837–840
Daemen J, Rijmen V (2002) The design of Rijndael: AES-the advanced encryption standard. Springer, Berlin
Fanti GC, Finiasz M, Ramchandran K (2013) One-way private media search on public databases: the role of signal processing. IEEE Signal Process Mag 30(2):53–61
Jin X, Chen Y, Ge S, Zhang K, Li X, Li Y, Liu Y, Guo K, Tian Y, Zhao G, Zhang X, Wang Z (2015) Applications and techniques in information security: 6th international conference, ATIS, Beijing, China, 4–6 Nov 2015, Proceedings, chap. color image encryption in CIE L*a*b* Space, pp 74–85. Springer, Berlin, Heidelberg
Jin X, Guo K, Song C, Li X, Zhao G, Luo J, Li Y, Chen Y, Liu Y, Wang H (2016a) Private video foreground extraction through chaotic mapping based encryption in the cloud. In: Multimedia modeling: 22nd international conference, MMM, Miami, FL, USA, 4–6 Jan 2016, Proceedings, Part I, pp 562–573
Jin X, Wu Y, Li X, Li Y, Zhao G, Guo K (2016b) Ppvibe: privacy preserving background extractor via secret sharing in multiple cloud servers. In: 8th international conference on wireless communications & signal processing, WCSP, Yangzhou, China, 13–15 Oct 2016, pp 1–5
Jin X, Yuan P, Li X, Song C, Ge S, Zhao G, Chen Y (2017a) Efficient privacy preserving Viola–Jones type object detection via random base image representation. In: Proceedings of IEEE international conference on multimedia and expo (ICME), Hong Kong, China, 10–14 July 2017
Jin X, Zhu S, Xiao C, Sun H, Li X, Zhao G, Ge S (2017b) 3D textured model encryption via 3D lu chaotic mapping. Sci China Inf Sci 60(12):122107:1-9
Lu H, Li Y, Mu S et al (2017a) Motor anomaly detection for unmanned aerial vehicles using reinforcement learning. IEEE Internet Things J 5(4):2315–2322
Lu H, Li B, Zhu J et al (2017b) Wound intensity correction and segmentation with convolutional neural networks. Concurr Comput Pract Exp 29(6):e3927
Lu H, Li Y, Chen M, Kim H, Serikawa S (2018a) Brain intelligence: go beyond artificial intelligence. Mob Netw Appl 23(2):368–375. https://doi.org/10.1007/s11036-017-0932-8
Lu H, Li Y, Uemura T et al (2018b) Low illumination underwater light field images reconstruction using deep convolutional neural networks. Future Gener Comput Syst
Osadchy M, Pinkas B, Jarrous A, Moskovich B (2010) Scifi-a system for secure face identification. In: 31st IEEE symposium on security and privacy, S&P, 16–19 May 2010. Berkeley/Oakland, California, USA, pp 239–254
Shashank J, Kowshik P, Srinathan K, Jawahar CV, (2008) Private content based image retrieval. In, (2008) IEEE computer society conference on computer vision and pattern recognition (CVPR),24–26 June 2008. Anchorage, Alaska, USA
Sohn H, Plataniotis KN, Ro YM (2010) Privacy-preserving watch list screening in video surveillance system. In: Advances in multimedia information processing-PCM, 11th Pacific rim conference on multimedia, Shanghai, China, 21–24 Sept 2010, Proceedings, Part I, pp 622–632
Upmanyu M, Namboodiri AM, Srinathan K, Jawahar CV (2009) Efficient privacy preserving video surveillance. In: IEEE 12th international conference on computer vision, ICCV, Kyoto, Japan, 27 Sept–4 Oct 2009, pp 1639–1646
Viola PA, Jones MJ (2001) Robust real-time face detection. In: IEEE 8th international conference on computer vision ICCV, Vancouver, British Columbia, Canada, 7–14 July 2001, p 747
Viola PA, Jones MJ (2004) Robust real-time face detection. Int J Comput Vis 57(2):137–154
Wong WK, Cheung DWl, Kao B, Mamoulis N (2009) Secure knn computation on encrypted databases. In: Proceedings of the 2009 ACM SIGMOD international conference on management of data, p 139152, ACM, New York, NY, USA
Wright J, Yang AY, Ganesh A, Sastry SS, Ma Y (2009) Robust face recognition via sparse representation. IEEE Trans Pattern Anal Mach Intell 31(2):210–227
Xiaobin Z, Jing L, Jinqiao W, Changsheng L, Hanqing L (2014) Sparse representation for robust abnormality detection in crowded scenes. Pattern Recognit 47(5):1791–1799
Zhu X, Jin X, Zhang X, Li C, He F, Wang L (2015) Context-aware local abnormality detection in crowded scene. Sci China Inf Sci 58(5):052110:111 (CCF-B)
Acknowledgements
This work is partially supported by the National Natural Science Foundation of China (Grant Nos. 61772047, 61772513), the Open Funds of CETC Big Data Research Institute Co.,Ltd., (Grant No. W-2018022), the Science and Technology Project of the State Archives Administrator (Grant No. 2015-B-10), and the Fundamental Research Funds for the Central Universities (Grant Nos. 328201803, 328201801).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
None of the authors declare that he/she has conflict of interest.
Human or animals rights
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Communicated by V. Loia.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Jin, X., Li, Y., Ge, S. et al. Secure face retrieval for group mobile users. Soft Comput 23, 12813–12820 (2019). https://doi.org/10.1007/s00500-019-03834-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-019-03834-6