- 1Theseus Ltd., Chippenham, United Kingdom
- 2Fixated Threat Assessment Centre, London, United Kingdom
- 3Department of Security and Crime Science, University College London, London, United Kingdom
The adoption of the term grievance-fuelled violence reflects the fact that similarities exist between those committing violent acts in the context of grievance in different settings, so potentially allowing the application of insights gained in the study of one group to be applied to others. Given the low base rate of violence against public figures, studies in the field of violence against those in the public eye have tended to use, as a proxy for violence, attempts by the individuals concerned to achieve unwarranted and unwanted proximity to the subject of their attention, given that approach is a necessary prerequisite for most forms of attack. In such studies, one factor that has frequently been considered is whether the making of threats is associated with a subsequent approach. The results have been varied, with no correlation found in some, a negative correlation in others, and a positive correlation in at least one. Such studies have been retrospective, using case files prepared for other purposes, and samples of cases have been selected according to their victims’ sector of employment – for instance, politicians, celebrities, judiciary, and the corporate world. This study of a sample of 126 threat assessment cases, using a prospective methodology, looks at the associations between the making of threats and subsequent approach from a different angle – that of a standardised and validated classification of underlying motivation. It finds that particular types and forms of threat are significantly associated with subsequent approach in cases that are fuelled by grievance, but not in those with the motivation of seeking a relationship. Furthermore, when a sample with a mixture of motivational categories was examined in the manner of previous studies, such associations with threat were not apparent. These results refine the existing understanding of the significance of threats in public-facing cases. Future research projects in this area might usefully incorporate the consideration of underlying motivation, in particular grievance.
Introduction
The term grievance-fuelled violence has been used over the last decade to reflect the fact that similarities exist between those committing violent that acts in the context of grievance in settings previously studied separately, such as school shootings, workplace violence, random massacres, and lone-actor terrorism (e.g., Lankford, 2012; McCauley et al., 2013; Capellan, 2015; Clemmow et al., 2022). This is relevant because insights gained in the study of one group may prove to be applicable to others. Indeed, Clemmow et al. (2022) suggest that, rather than developing risk assessment tools for specific contexts of violence, “an overarching framework for guiding threat assessment of LAGFV [lone-actor grievance-fuelled violence] may be feasible”. In the field of violence against those in the public eye or in public-facing roles, studies have been similarly “siloed,” with the cases studied according to sector of employment – for instance, celebrities (Dietz and Martell, 1989; Dietz et al., 1991a; Meloy et al., 2008), politicians (Dietz and Martell, 1989; Dietz et al., 1991b,Scalora et al., 2002a,b), royal families (Fixated Research Group, 2006; James et al., 2010; van der Meer et al., 2012), judicial officials (Calhoun, 1998; Eke et al., 2014), and the corporate world (James et al., 2022). The relevance of the concept of grievance-fuelled violence in these areas of study has been described (Pathé et al., 2018; Wilson et al., 2018, 2021; Barry-Walsh et al., 2020, p. 482).
A focus within this literature has been the issue as to whether detectable warning behaviours precede incidents of violence (Meloy et al., 2012, 2021), and one question that has repeatedly arisen is whether the making of threats is associated with subsequent adverse consequences. Some studies have focussed on the cases of physical violence committed against those in the public eye and examined antecedent events for the presence of warning behaviours, including threats (e.g., Fein and Vossekuil, 1999; James et al., 2007, 2008; Hoffman et al., 2011). A general finding is that acts of violence against public figures often involve forms of previous warning behaviour, including the making of threats. This is important as it offers the possibility of preventive interventions. However, such studies offer no information as to the proportion of all communicated threats that are associated with subsequent violence. A problem with trying to examine the associations of threats prospectively is the very low base rate of violence. Given this, studies have tended to use, as a proxy for violence, attempts by concerning correspondents at subsequent approach, in other words attempts to achieve unwarranted and unwanted proximity to the subject of their attentions. Approach is considered a proxy for violence because it is a necessary prerequisite for almost all forms of attack.
The method adopted in such studies of threats to public figures is to examine a sample of the writers of inappropriate and concerning letters, comparing those who subsequently approached the public figure with those who did not. Results have generally shown that, although many individuals who approach have made threats, there is no significant association between making threats and approaching in some studies: In a few studies, a positive association was indeed identified; yet in others, there was a significant inverse correlation between the two. To an extent, the differences in results may be influenced by the sector of employment of the public figures forming the basis of each study, but even then, the results from research efforts are inconsistent.
Three areas of employment have been subjected to particular study. Dietz et al. (1991a) made an exhaustive study of cases of threatening and otherwise inappropriate letters to Hollywood celebrities, using stratified samples of 107 individuals who pursued encounters with the celebrities and 107 who did not. Of the 214 cases, 49 (23%) made threats of some sort. The definition of threats was broad and not restricted simply to the threats of violence. There were no significant associations, positive or negative, between making threats and subsequent approach. This applied regardless of the type of threat, the consequence threatened, or the number of threats made. By contrast Meloy et al. (2008, 2011) examined an archival, convenience sample of stalkers and harassers, taken from the case files of police, prosecutorial agencies, and the security department of an entertainment corporation, as well as their own personal case archives. They identified 271 cases of “celebrity stalkers,” of whom 18% (48 cases) made threats of physical violence. Threats of physical violence were found to be significantly associated with approach.
A second group of studies concerned politicians. Dietz and Martell looked at threatening and otherwise inappropriate letters to members of Congress (1989; Dietz et al., 1991b), comparing 43 subjects who pursued encounters with the members of Congress with 43 who did not. Threats in some form were made in 50 cases (58%). Threats were significantly associated with the absence of subsequent approach. This applied to direct threats, indirect threats, and veiled threats, and also to any form of threat, as well as threats of violence. In addition, the mean number of threats was significantly greater in those who did not subsequently approach. Subsequently, Scalora and colleagues looked for the associations between threats and approach to the members of congress as a part of three broader studies. The first study examined 4,387 electronic case files from the archives of the Threat Assessment Section of the U.S. Capital Police, which concerned threatening or otherwise problematic contacts with members or staff (Scalora et al., 2002a). These cases were then divided into those that approached and those that did not. In all, 986 cases (22.5%) approached. The sample included cases where approach had not been preceded by communication. Subjects “were considered to have utilised threatening language if they described a desire to physically harm or have physical harm occur to the target in either a direct or veiled fashion.” Using this definition, 31.7% of cases involved a direct or veiled threat towards members of the “congressional community.” Approachers were significantly less likely to have made a direct or veiled threat prior to the problematic contact. However, it was noted that 21.5% of approachers had threatened, as had 42% of “violent approaches” (those involving “threat or use of a weapon, attempted, or actual assault”). A second study from the same group (Scalora et al., 2002b) randomly selected 316 of the more recent files from the same source, with a particular focus on pre-approach behaviour. Cases involving threatening language were “over-sampled” in this design to ensure that an adequate proportion of such cases was included. The definition of threatening language was expanded to include, not only threats of physical harm, but also “vague unspecified harm (e.g., potentially to physical, reputational or political well-being).” In total, 104 cases (32.9% of the total sample) approached, and 205 (64.9%) threatened. The making of threats was significantly associated with not making an approach. A third study (Schoeneman et al., 2011) tightened the methodology somewhat in terms of rationale and hypotheses, the emphasis of the study being on thematic content and language characteristics. The authors examined a sample of 326 written contact cases, 49 of whom had engaged in approach behaviour and 277 had not. No significant difference was found between approachers and non-approachers in the use of “threatening language,” for which the operational definition in the coding manual was not included in the published paper.
In a third group of studies, the Fixated Research Group (FRG)1 conducted extensive investigations into those who engaged in threatening or otherwise inappropriate communications towards the members of the British royal family, or made attempts, successful or otherwise, to approach them (Fixated Research Group, 2006). The definition of threats used was that of Scalora et al. (2002b): in other words, it was broad in scope and not restricted to threats of physical violence. The various studies by the FRG which resulted concerned a structured, random sample of 365 cases taken from 5,685 case files held by the Metropolitan Police Force’s Royalty Protection division. The sampling method ensured roughly equal representation for the different categories of behaviour adopted, these being: pre-approach (i.e., communications); pre-approach and approach; approachers; failed breachers of security cordons; and successful breachers. In comparing those who communicated with those who both communicated and approached, the making of threats was significantly associated with the absence of approach. However, this did not hold for those who made successful or unsuccessful attempts to breach security perimeters for the purpose of achieving proximity. A similar exercise was subsequently undertaken with 107 cases who sent disturbing communications and/or made problematic approaches to members of the Dutch royal family (van der Meer et al., 2012). Here, threats were defined as communications threatening serious physical or sexual assault, kidnapping, or arson. Those who made threatening communications were significantly less likely to approach.
There has been a range of other studies concerning threats to public figures, which have produced valuable findings, but did not directly consider the relationship between threats and approach. For instance, Calhoun (1998) examined more than 3,000 threatening contacts and assaults against federal judicial officials and examined which forms of threat were more likely to be associated with violence. However, concerning communications which did not threaten were not examined. Eke et al. (2014) examined reoffending rates at 2 years in those who had threatened or harassed judicial officials in Ontario. Threateners were significantly more likely to engage in violent reoffending, but the study did not produce results that could be compared with the findings detailed above. Such studies are not considered further here.
The initial reaction to the studies concerning threats and approach that were published in the 1990s was somewhat simplistic, at least amongst non-clinicians, with some authors erroneously concluding that threats were either irrelevant or somehow a protective factor against violence in public figure cases. This sentiment was captured by Meloy (2000, p. 161): “Threats are not that big a deal. That’s right, you read it correctly.” Meloy later set out the nature and history of this widespread misapprehension (Meloy, 2014, pp.244-5) and described the current consensus that threats need to be taken seriously in risk assessment. This has been put clearly by Mullen and colleagues who state the practical position in terms of threats in stalking and harassment: “Threats should be regarded as promises. Like many promises, not all are fulfilled, but nevertheless they should be accepted as a commitment to future action until proved otherwise” (Mullen et al., 2000, p. 218).
Problems of interpretation are not aided by inconsistencies in the results from different studies, which serve to indicate that some parameters may be missing in the consideration of the problem. Dietz and Martell (1989, p. 14: 17), in their major report to the National Institute of Justice, drew up risk-factor scales for approach in celebrity cases. Yet, when they tried to apply these to cases involving the members of Congress, the scales failed to distinguish approach-positive cases from approach-negative. The authors note (Dietz et al., 1991b) that the focus and concerns of those contacting/approaching celebrities differed from those concerned with members of Congress. In the celebrity cases, 56% “idolised or worshipped” the celebrity to whom they wrote, whereas only 2% were preoccupied with “injustice to self.” In the congressional cases, 38% were preoccupied with “justice to self” and only 4% were preoccupied with “love, marriage, romance.” In other words, the pattern of motivations differed between the two samples. The papers discussed above have generally examined motivation in terms of such factors as thematic content, adopted roles, preoccupations, and concerns, using ad hoc lists of constructs and categories. Only the royal family studies constructed a standardised typology of motivation and applied it to individual cases. All the studies illustrate a wide range of different pre-occupations and concerns within each sample, though these are not directly comparable between all the studies, tend to be overlapping rather than mutually exclusive, and some of the lists are long. They are not necessarily comprehensive, and it is inevitable that retrospective file trawls produce a proportion of cases with insufficient information to divine motivation. The relevant classifications are set out in Table 1. They key point here is that all the studies involved a rag-bag of motivations, mixed in a way that had no meaning per se and was unlikely to be directly reproducible.
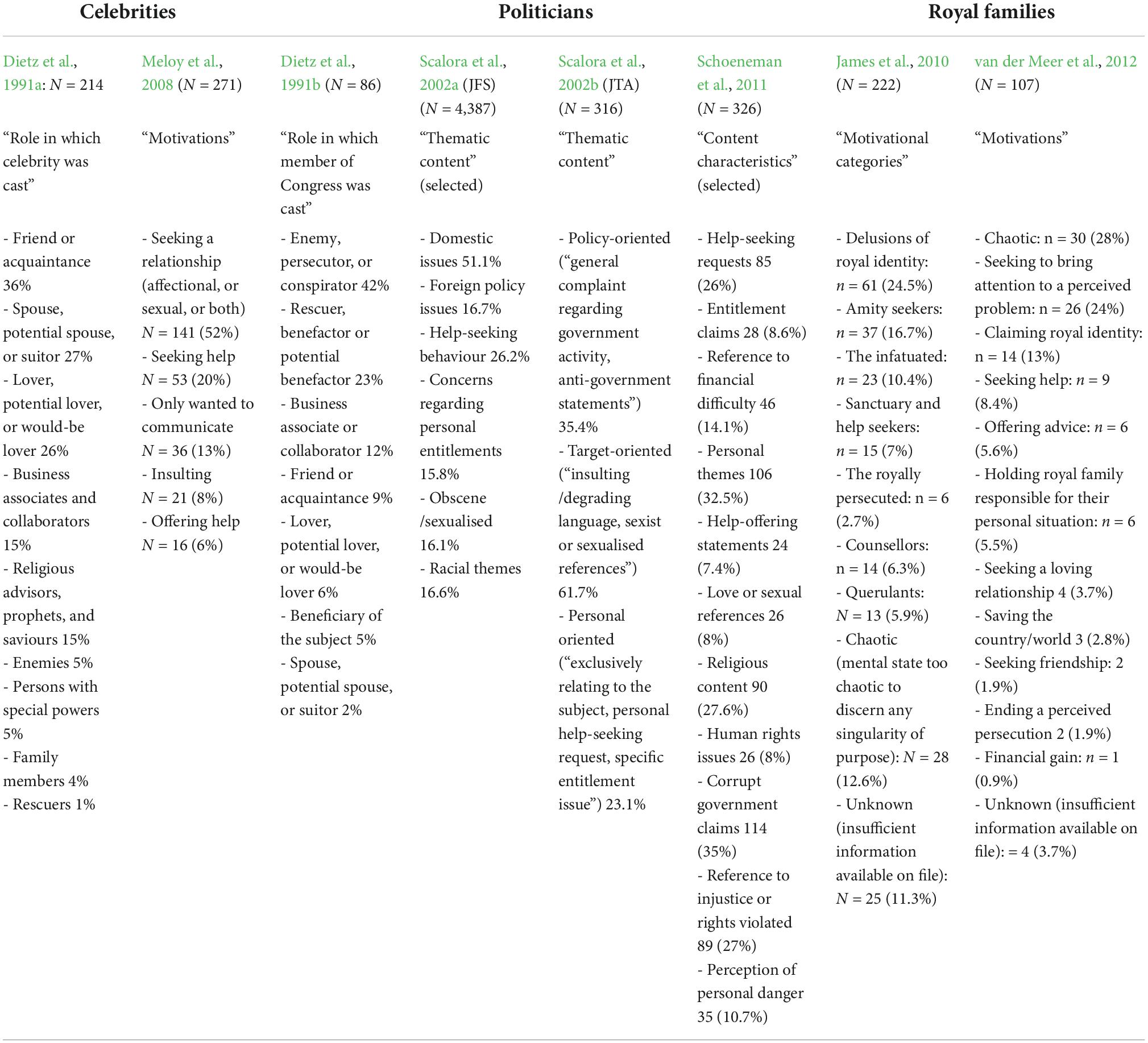
Table 1. Motivational categories adopted in eight studies which examined associations between threats and approach.
In effect, the study of groups selected by the recipients’ sector of employment determines that each sample is a hodge-podge of motivations, even if particular ones predominate in a given sector. This might be of no importance in the study of threat and approach if motivation had no effect on the relationship between the two. Yet, if motivation is important, then to study mixed samples risks defeating the purpose: and there are in fact some clear indications that motivation is a determining factor. Whilst the field may not have been originally conceived of as such, threatening and otherwise inappropriate communications to public figures constitute forms of stalking and harassment: and it is clear from the general stalking literature that motivation is central to the assessment of risk in stalking. The most widely accepted motivational classification, that of Mullen et al. (1999), defines five categories of stalkers, including categories concerning grievance and relationship-seeking. Subsequent studies using this classification have shown that associations of risk in stalking vary between the categories, with significant differences in rates of violence, persistence, and recurrence, and in the prevalence of psychosis and attachment problems (MacKenzie et al., 2008; McEwan et al., 2009a,b, 2017, 2018; James et al., 2010a). In terms of threat, differences have been demonstrated, in that explicit threats were significantly associated with violence in approachers in the rejected category (McEwan et al., 2009b). In addition, it has been illustrated that different forms of risk (e.g., persistence, violence, and escalation) carry different associations in terms of risk factors, and that these vary in turn with motivational group (Mullen et al., 2009b: pp. 226-250). This forms the basis of the Stalking Risk Profile (MacKenzie et al., 2009), a leading structured professional judgement tool for the assessment of risk in stalking, the validity of which has been demonstrated (McEwan et al., 2018). It would seem logical that the association between threats and approach should be investigated in terms of the motivation of the problematic individual, rather than the profession of the victim. As Meloy et al. wrote in 2010: “…The issue for future research should no longer be whether threats are important, but which threats and threateners are associated (or not associated) with which form of adverse event, behaviour or motivational type.” Yet, direct analysis of the association between threats and approach (as a proxy for violence) has yet to be undertaken by motivational type.
Other than the underlying motivation, a further factor which has not been subjected to systematic study concerns the immediate purpose of a threat. In other words, with the underlying motivation as background, what is the immediate purpose of the threat to the threatener? For instance, a threat might be a way of simply venting anger or be intended to cause psychological pain to the recipient. Or it might be a paranoid defensive stance, or a straightforward statement of intent. A simple, standardised classification of immediate purpose has been developed (Warren et al., 2014), but this has not up to now been used in the study of threats in concerning communications to public figures and those in the public eye.
This study was conceived with the specific purpose of examining the relationship between threats and approach in a manner based on motivation, rather than the victim’s source of employment. A particular focus was upon the motive of grievance. In addition, it was intended to avoid some of the methodological problems that are evident in other studies. First, some studies have included cases where there has been approach without previous communication: this confuses the issue. Second, all the principal studies outlined above have problems with sequencing: in other words, they are unable to differentiate (and therefore may have included) cases of communicated threat which were made after approach or were delivered at first approach. This introduces impurity into the samples, such that it cannot safely be concluded whether or not threats are a risk factor, because it is unclear whether any relationship is predictive. There are also divergences in terms of the definition as to what constitutes a threat. The most comprehensive definition has been that of Dietz et al. (1991a,b), who defined a threat as “any offer to do harm, however implausible.” This is broad enough to include, not only threats of physical violence, but also threats of suicide, property damage, financial consequences, reputational damage, and persistence. A similar definition was adopted by Scalora et al. in the second of their studies (Scalora et al., 2002b) and in the British royal family studies (Fixated Research Group, 2006; James et al., 2010). However, the other studies outlined above limited themselves to the consideration of threats of physical violence and excluded other threatened consequences (Scalora et al., 2002a; Meloy et al., 2008; van der Meer et al., 2012), whereas Schoeneman et al. (2011) considered only the rather vague category of “threatening language.” This concentration upon the risk of violence is understandable in terms of the fear of homicide, particularly in jurisdictions where members of the public are able to gain access to firearms. However, other types of threatened action are also serious, such as the causing of reputational or financial damage. Nor is there any reason to suppose that those threatening something other than violence are immune from subsequently engaging in acts of violence. These are arguments for studying threats in the round. Finally, it appears that all studies, apart from an examination of threats in corporate cases (James et al., 2022), have been archival in nature, based upon police or security files prepared for purposes other than research. Given that the cases were historical, the researchers had little opportunity to add information from further sources, other than criminal records or police data and, in the case of Dietz and colleagues’ investigation into celebrity cases (1991a), from details reported in the press.
Aims
The study aimed to examine the links between threats and approach as a proxy for violence, using a clearly defined sample and adopting standardised categorisations of underlying motivation and of the immediate purpose of threats, which have an established basis in the specialist literature.
In doing so, the aim was to examine four principal hypotheses, derived from an examination of the literature described above:
1) The associations between making threats and approach will differ when the underlying motivation is one of grievance, compared with cases where the motivation is the seeking of a relationship.
2) Associations identified between threats and approach in individual motivational groups will no longer be evident, if all the different motivational groups are considered together as one single group.
3) Between motivational groups, different associations with approach will be found according to the immediate purpose of making threats.
4) The form of harm threatened will be linked with the likelihood of subsequent approach.
To explore hypotheses (1) and (2), particular factors were chosen to examine for positive or negative associations with approach. These were drawn from factors considered in previous studies. Specifically, they comprised:
• Making of threats per se.
• Making of different types of threats (i.e., direct, indirect, veiled, and conditional)
• Numbers of threats made, both overall and of each individual threat type.
• Substance of the threats (i.e., the consequences threatened)
• Characteristics of language used.
• Immediacy, escalation, persistence, and plausibility.
• Presence of serious mental disorder.
Overall, the study embraced three broader purposes: to expand understanding of the role of grievance in public figure threats, to help make sense of some of the reasons for conflicting results in previous studies of threats to public figures, and to suggest improvements in methodology for future studies.
Method
The study used a prospective design, in that data items were gathered on open cases as they progressed, rather than from closed files prepared for other purposes.
Study sample
The original sample comprised 140 consecutive cases referred to a risk assessment company based on the Fixated Threat Assessment Model (Wilson et al., 2021), in which security/police staff work alongside psychiatric personnel. Each case included in the study involved a full risk assessment and investigation, as opposed to the more numerous referrals in which the company was asked only for an outline opinion or initial handling advice. A purpose-designed dataset was completed as each case progressed and entered into a computerised database in an anonymised form. This included copies of all relevant communications and background information, from which names had been redacted to meet data storage requirements.
The 140 cases had either written concerning communications or made concerning approaches, or both. Cases in which concerning communications had been made subsequent to, or at the time of, first inappropriate approach were then excluded, as were cases which involved approach, but no communication. The cases were then divided according to motivation.
Definitions
Threats
A threat was defined as a statement or indication by someone that they will do something unpleasant or harmful to another or cause something unpleasant to happen to the recipient of the threat or someone close to them. The definition included, but was not restricted to physical violence (i.e., infliction of physical injury), and it encompassed other possible forms of harm:
• Threat of a psychological consequence, such as fear, distress, emotional pain, or misery.
• Threat of sexual violence (i.e., unwanted sexual activity imposed by physical force).
• Threat to persist, that a person’s unwanted attentions will not go away.
• Threat to escalate unwanted behaviours, for instance by moving from writing to turning up in person.
• Threat of a legal consequence, such as prosecution.
• Threat of a reputational consequence, such as adverse publicity or exposure, whether through informing named individuals, employers, news media, or similar.
• Threat of a financial consequence, such as losses or ruin.
This definition was presumed to be very similar in scope to that of Dietz and Martell (1989).
Types of threat
Threats were classified into the following categories:
• A direct threat: a straightforward statement of intent. For instance, “I am going to take you to court”; “I am going to get you sent to gaol”; “I am going to kick the living day-lights out of you”; “I am going to kill you.”
• An indirect threat tends to be vague, hinted at, and somewhat unclear. The precise negative consequence and the general plan are unspecified. For instance: “You are going to get what you deserve”; “You are going to be sorry.”
• A veiled threat is a coded statement in which no explicit intentions are articulated, but rather are implied. The statement clearly hints at a possible negative consequence, but leaves it to the potential victim to interpret the message and give a definite meaning to the threat. For instance, “You wouldn’t like to see me when I’m angry,” or “It would be a shame if anything happened to you.”
• A conditional threat is one that threatens a negative consequence unless the recipient does what the threatener wants, e.g., “Unless you do what I ask, I will ruin you”; “If you don’t settle this matter, your family will suffer.”
The different types of threat used and their number were recorded for each case through studying the totality of communications. Classification was undertaken jointly by four of the authors, together reviewing each case and threat.
Approach
An approach was defined as any uninvited attempt, successful or otherwise, to achieve physical propinquity to the person concerned. In total, eight different behaviours, which are not mutually exclusive, were recorded separately and then summated into one variable: turning up at offices/places of work; concerning behaviour at offices/places of work; appearing at home address; attempt at personal approach; physically accosting; following; attack or attempted attack; waiting/loitering for. These behaviours are not considered individually below.
Plausibility
Whether a threat was empty or realistic was considered in terms of four different criteria:
• Plausible. The threat is one that would be practicably possible to carry out, e.g., “I will write to your employer.” “I will tell your wife that you are having an affair.”
• Fairly implausible. The threat would be possible, but very difficult to carry out. For instance, “I will shoot you,” in a country with no access to guns. Or “My lawyers will be filing criminal and civil actions,” in someone with a case that no competent lawyer would take on, or where the complainant had no means to pay a lawyer.
• Completely implausible: “I will drop a nuclear bomb on you.”
• Practicable, but toothless: “I will write to the Prime Minister and the newspapers.” Or “I will report you to the police.”
Categorisations
Motivational typology
The motivational typology of harassing and stalking behaviour used in this study is that of Mullen et al. (1999), which is generally accepted as the standard (Pinals, 2007). It defines five categories of stalkers: the Rejected, Intimacy Seekers, the Incompetent Suitor, the Resentful, and the Predatory. The motivational classification is incorporated into the structure of the Stalking Risk Profile (SRP: MacKenzie et al., 2009; McEwan et al., 2018), a widely used structured professional judgement tool for the assessment and management of risk in harassment and stalking. The version of the classification used here is the adaptation for public figure cases set out in the SRP (pp. 69-71). The definitions of each category are set out in Table 2. This includes an additional three categories (Help Seekers, Attention Seekers and the Chaotic, adapted from Mullen et al., 2009a,b). It excludes the “Predatory” category of the typology by Mullen et al., examples of which are very rare in public figure samples and of which there were none in the current dataset. Whereas the public figure typology excludes the “Rejected” category, it was retained here. The “Resentful” group is to all intents and purposes synonymous with the “aggrieved,” and the latter term will be used from this point on. Cases were allocated to SRP motivational group by joint discussion between three authors, including a co-author of the SRP. In three cases where difficulty was experienced in group allocation, the opinion of the lead author of the SRP was sought.
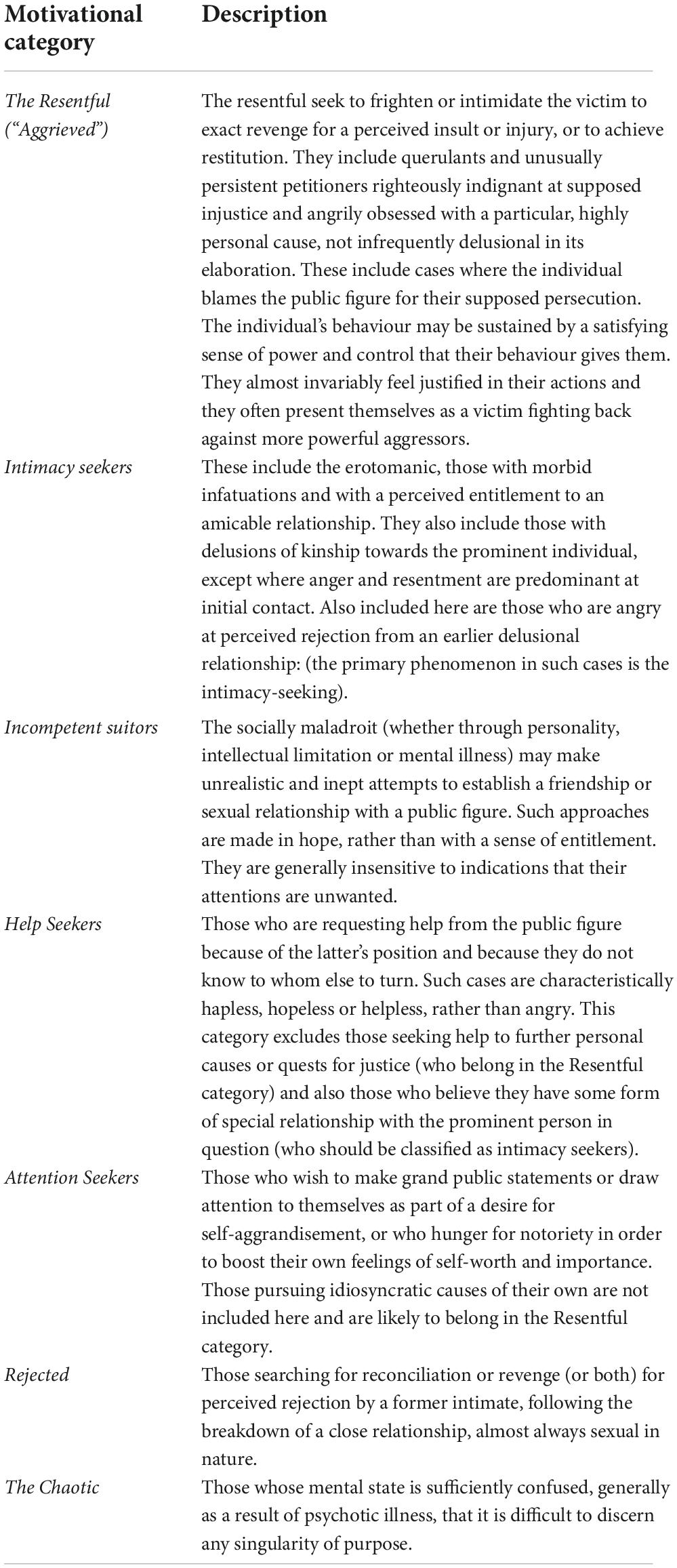
Table 2. Definitions of motivational categories extracted from Mullen et al. (1999) and MacKenzie et al. (2009).
Immediate motives for making threats
The sibilant categorisation of Mullen and colleagues (Warren et al., 2014) was adopted. This divides motives into five separate and mutually exclusive categories:
• Screaming: To achieve emotional release, the threat is made to release emotional pain. The act of sending the threat in itself brings relief to the threatener.
• Shocking: To cause emotional pain, the threatener rejoices in the idea of the emotional pain that the threats will inflict upon the recipient.
• Shielding: To get their defence in first, for instance, paranoid people who believe they are about to be attacked in some manner may threaten as a form of self-defence.
• Scheming: To make someone do something, conditional threats to make the recipient behave in a certain way.
• Signalling: Declarations of intent, a simple statement of what the person is going to do.
Allocation to categories was undertaken through joint discussion between four authors.
Statistical analyses
Data on the cases in question were entered into a database and analysed using SPSS-26 (IBM Corp., 2019). The chi-square test was used to examine the associations between categorical variables. Where any minimum cell counts were less than 5, Fisher’s exact test was reported. Odds ratios with 95% confidence intervals are also given for each significant association. For the ease of understanding, odds ratios and 95% confidence intervals of less than 1 are reported as reciprocals. To examine the differences between two samples when the dependent variable was either ordinal or continuous, the Mann–Whitney U test for medians was used. An advantage of the Mann–Whitney U test is that it can be used for relatively small sample sizes.
Effect sizes
The effect size was calculated for each measure of association. Whereas null hypothesis significance testing indicates how likely it is that a result is due to chance, effect size indicates the magnitude (and therefore importance) of the relationship (Nakagawa and Cuthill, 2007). In contrast to p-values, the effect size is independent of sample size, which makes it a useful and separate source of information when sample sizes are small or uneven and Type II errors more likely (Siegel and Castellan, 1988). φ was used as the measure of effect size with chi-square testing, and r with Mann–Whitney U (Rosenthal, 1991). In general, when the interpretation of effect sizes cannot be contextualised, it is suggested that a value that reaches 0.1 may be considered a small effect, one that reaches 0.3 a medium effect, and 0.5 a large effect (Cohen, 1988).
Odds ratios
Odds ratios are used as a further way of describing effect size in associations when the outcome is binary. They represent the probability that an event will occur divided by the probability that it will not occur. Confidence intervals can be provided for odds ratios and ORs are easier to compare than measures such as φ. Other studies in this area have presented odds ratios, and the facility for comparison between studies is desirable. Odds ratios are suitable for retrospective cohort studies (McKenzie and Thomas, 2020), and their inclusion here takes account of it being “best to examine study results presented in several ways to better understand the true meaning of study findings” (Norton et al., 2018, p. 85).
Considerations of sample size
A priori sample size calculations are conspicuous by their absence in the studies of threats and approach, including the present study. This reflects the exploratory and preliminary nature of research exercises in this area, one in which sample size calculations “may be of little value in early exploratory studies where scarce data are available on which to base the calculations” (Jones, Carley & Harrison, p. 455).
Multiple testing
As the purpose of the study was to explore possible associations, multiple testing was used. In the interests of minimising Type II errors, no corrections to significance values were incorporated to compensate for multiple testing. In consequence, conclusions drawn below from p-values larger than 0.01 should be treated with caution, in terms of the possibility of Type I errors (those where an association is erroneously found to be significant).
Results
Sample selection
Of the 140 cases in the original sample, fourteen were excluded because approach occurred without prior communication, the communication was handed over at the time of approach, or the communication came after the approach. This gave a sample of 126 cases.
The 126 cases were broken down according to motivational group. In total, 51 cases fell into the resentful/aggrieved category. There were 42 cases which fell into either the intimacy-seeking or incompetent suitor groups. The latter two have important differences, in that the intimacy seekers are more likely to suffer from psychotic illness. However, the shared motivation is the pursuit of an intimate relationship. For this reason, the two were taken together for the purposes of the study and are referred to as “relationship-seeking.”
Preliminary analyses were undertaken to determine whether intimacy seekers and incompetent suitors showed any differences in key areas which might make combining them into one relationship-seeking group inadvisable. Examining the proportions who made threats and the proportions making different categories of threats (direct, indirect, veiled, and conditional), there were no significant differences using the chi-square test, and effect sizes were small, ranging from −0.014 to −0.149. Nor were there any significant differences, employing the Mann–Whitney U test, in overall numbers of threats made or numbers of categories of threats used.
The aggrieved and relationship seekers together accounted for 73.8% of the cases in the sample. The remaining 26.2% (33 cases) were distributed amongst four further motivational groups: attention/publicity seeking 5 (4%); help-seeking 13 (10.3%); chaotic 7 (5.6%); and rejected 5 (4.0%). In total, three cases (2.4%) were difficult to classify. (Two were aggressive Twitter campaigns without any obvious motivation, and one involved an inept attempt at fraud and blackmail). The number in each of these groups was too small to warrant separate study. Accordingly, the study focussed on threatening behaviour in the aggrieved and relationship seekers, the association between threats and approach in these two groups, and for the sake of comparison, some analysis of these factors in the study sample of 126 cases, the sample being undifferentiated in terms of motivation.
Of the resentful cases, 13.7% originated from the talent sector, this denoting a group of actors, authors, television presenters, and other performers. A further 17% were private individuals, essentially those of high net worth or well known because of previous careers in politics. In total, 72.5% were in public-facing roles because of their positions in large banking institutions, well-known companies, or non-governmental organisations (“corporate” cases). The equivalent percentages for the relationship-seeking were as follows: talent sector 78.0%; private individuals 12.2%; and corporate cases 9.8%.
Comparing basic characteristics of the aggrieved with those of relationship seekers
Sex
The sex profiles of the two groups were very similar: Resentful men 40 (80%), relationship-seeking men 33 (78.6%): χ2 = 0.028, p = 0.866, φ = 0.018.
Age
The age of the cases was available in 70% of cases (65). The age profiles of the two groups were similar: Resentful: mean = 43.21, SD = 13.05; Relationship-seeking: mean = 39.35, SD = 10.51. Mann–Whitney U = 443.50, Standardised test statistic (z) = –1.072, p = 0.284, r = 0.133.
Associations between threats and approach
A series of analyses was conducted to examine the associations between the making of threats and approach in the aggrieved, in relationship seekers and in the study sample as a whole, undifferentiated by motivation (“all-motivations” group).
Proportions of cases that approached
Of the all-motivations group of 126 cases, 40 (31.7%) approached. Of the 51 aggrieved cases, 14 approached (27.5%). Of the 42 relationship-seeking cases, 20 (47.6%) approached. Aggrieved cases were significantly less likely to approach than relationship-seeking cases (χ2 = 4.039, p = 0.044; φ = –0.208; OR [95%CI] 2.404 [1.013–5.682].
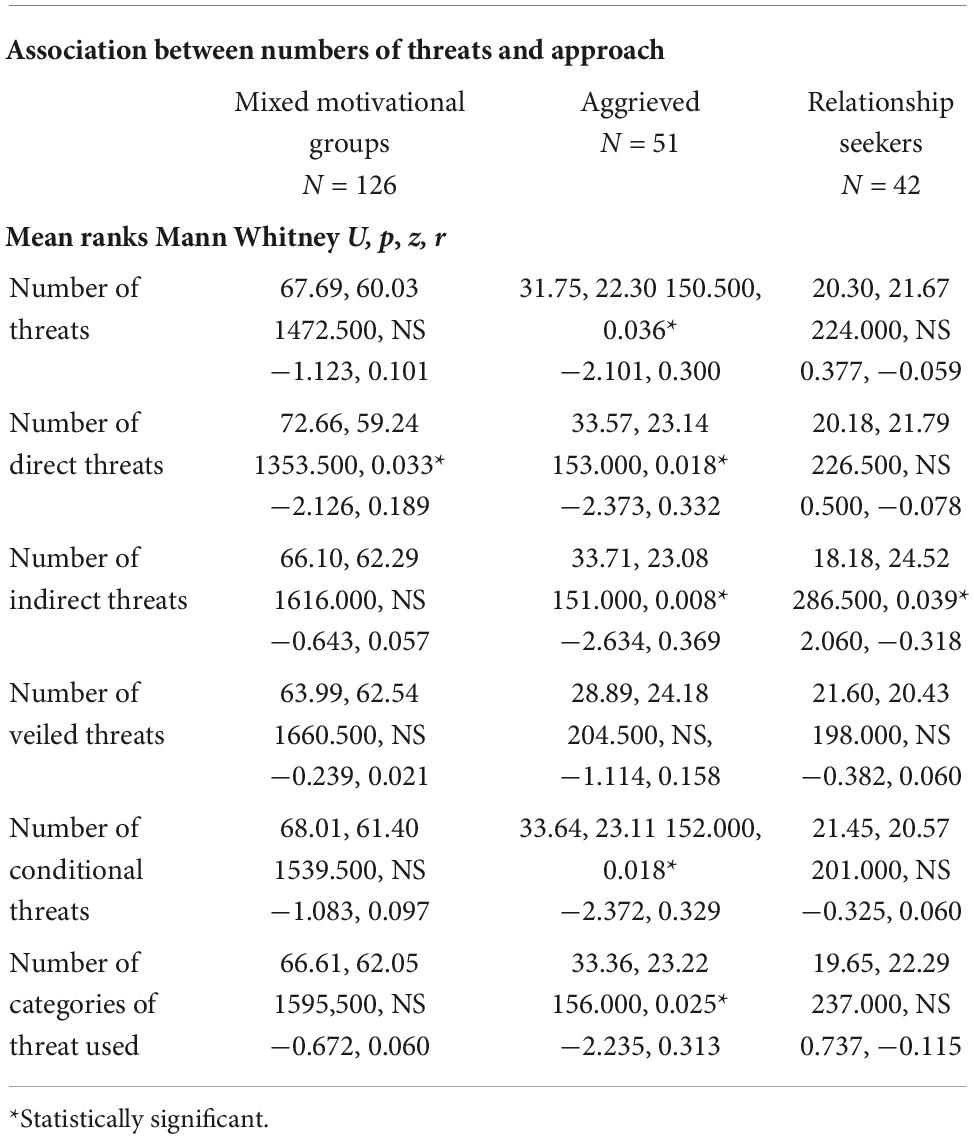
Associations between type of threat and approach in the mixed motivations sample, and in aggrieved and relationship-seeking groups
In the mixed motivations sample, there were no significant associations between the making of any threats and approach (refer to Table 3, which considers the mixed motivations group, the aggrieved and the relationship seekers separately and sequentially). Nor were there any significant associations between approach and the making of specific types of threat. Indeed, the proportions of cases making different types of threats who subsequently approached are similar to the proportions who did not. In the aggrieved cases, the proportion of threateners who approached is larger for each type of threat than the proportions of threateners who did not approach. The reverse is true for all types of threatening in relationship-seeking cases, in that the proportions of approachers who threatened were smaller than the proportions of threateners who did not approach.
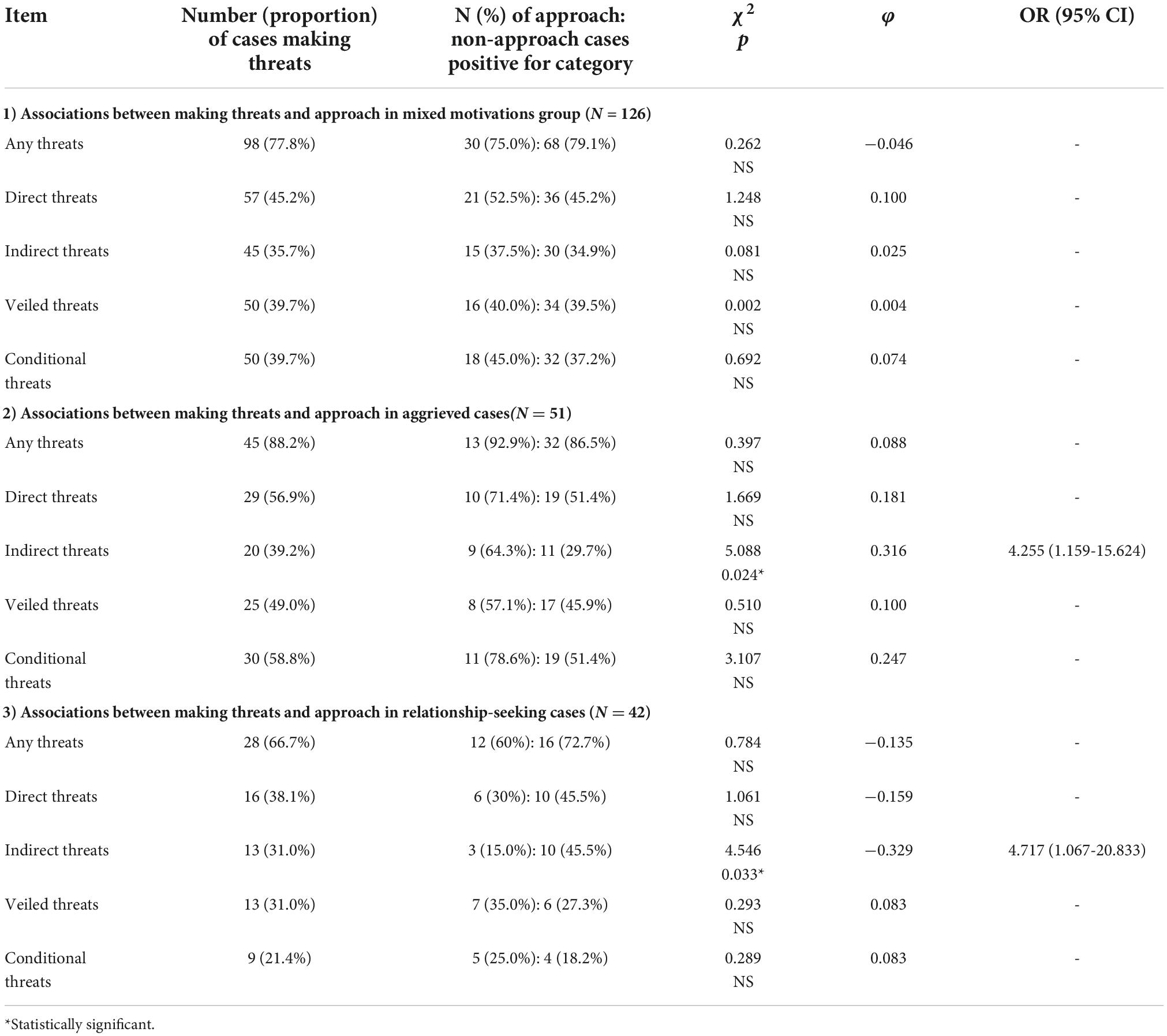
Table 3. Associations between threats and threat types and approach in the mixed motivations group, the aggrieved and relationship seekers.
In aggrieved cases, the making of indirect threats was significantly associated with approach. In relationship-seeking cases, the position is reversed, in that the making of indirect threats is significantly associated with the absence of approach. In the aggrieved cases, the association between conditional threats and approach fell short of significance in the current sample (p = 0.078), whilst there was an effect size of 0.247.
Association between numbers of threats made and approach
In the aggrieved cases, there was a statistical association between numbers of threats and approach in all categories examined, apart from veiled threats; that is for total threats, direct threats, indirect threats, conditional threats, and number of threat categories used (refer to Table 4). In the relationship seekers, the only significant association was a negative one between approach and numbers of indirect threats made. In the mixed motivations sample, the only statistically significant association between numbers of threats and approach was for direct threats.
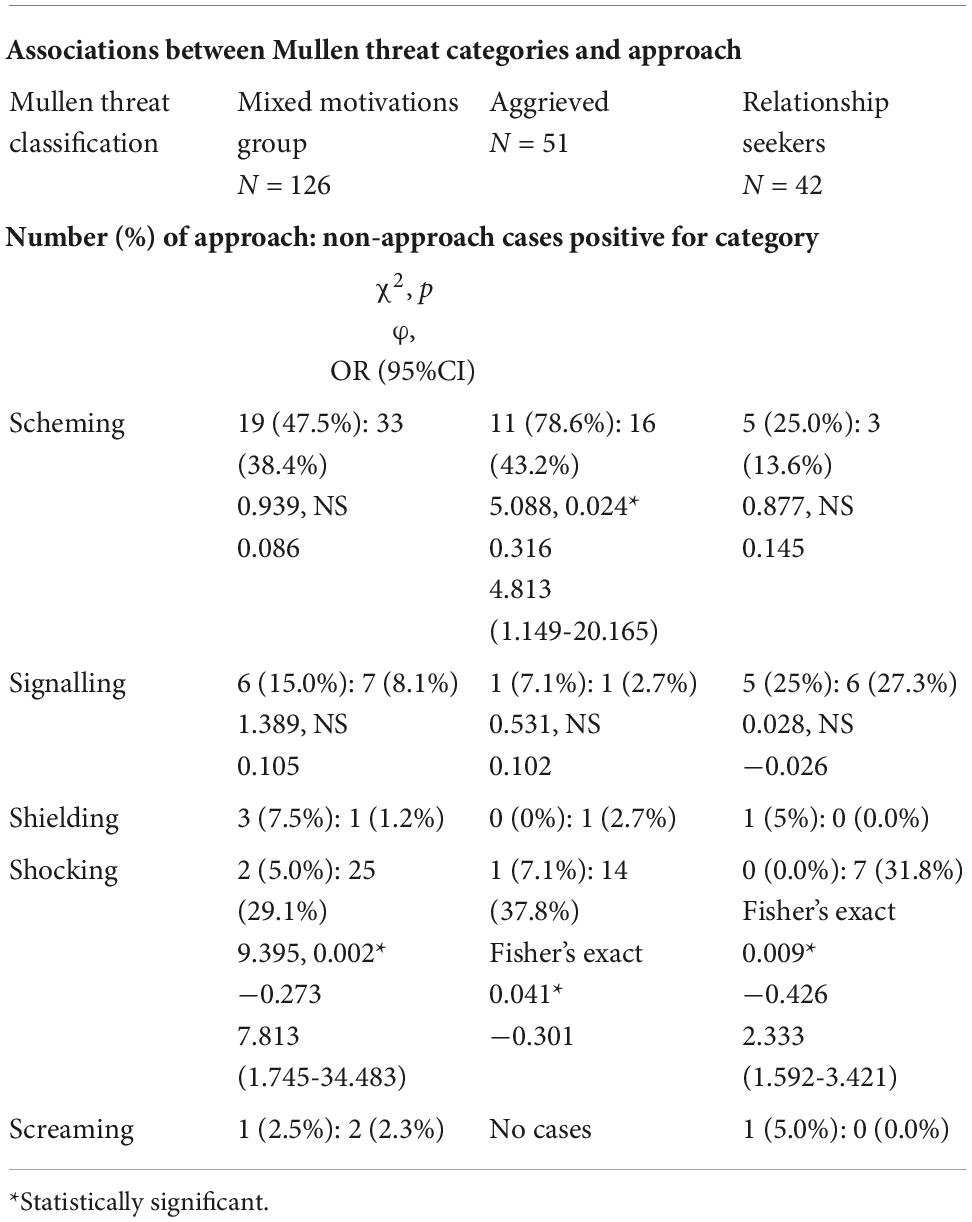
Associations between Mullen threat categories and approach
A consistent finding with the mixed motivations sample, the aggrieved and the relationship-seeking, was that “shocking” was negatively associated with approach (refer to Table 5). In the aggrieved cases, “scheming” was significantly associated with approach, but no such relationship was found in the mixed motivations sample, nor in the relationship seekers. There were too few cases in the shielding and screaming categories for meaningful analysis.
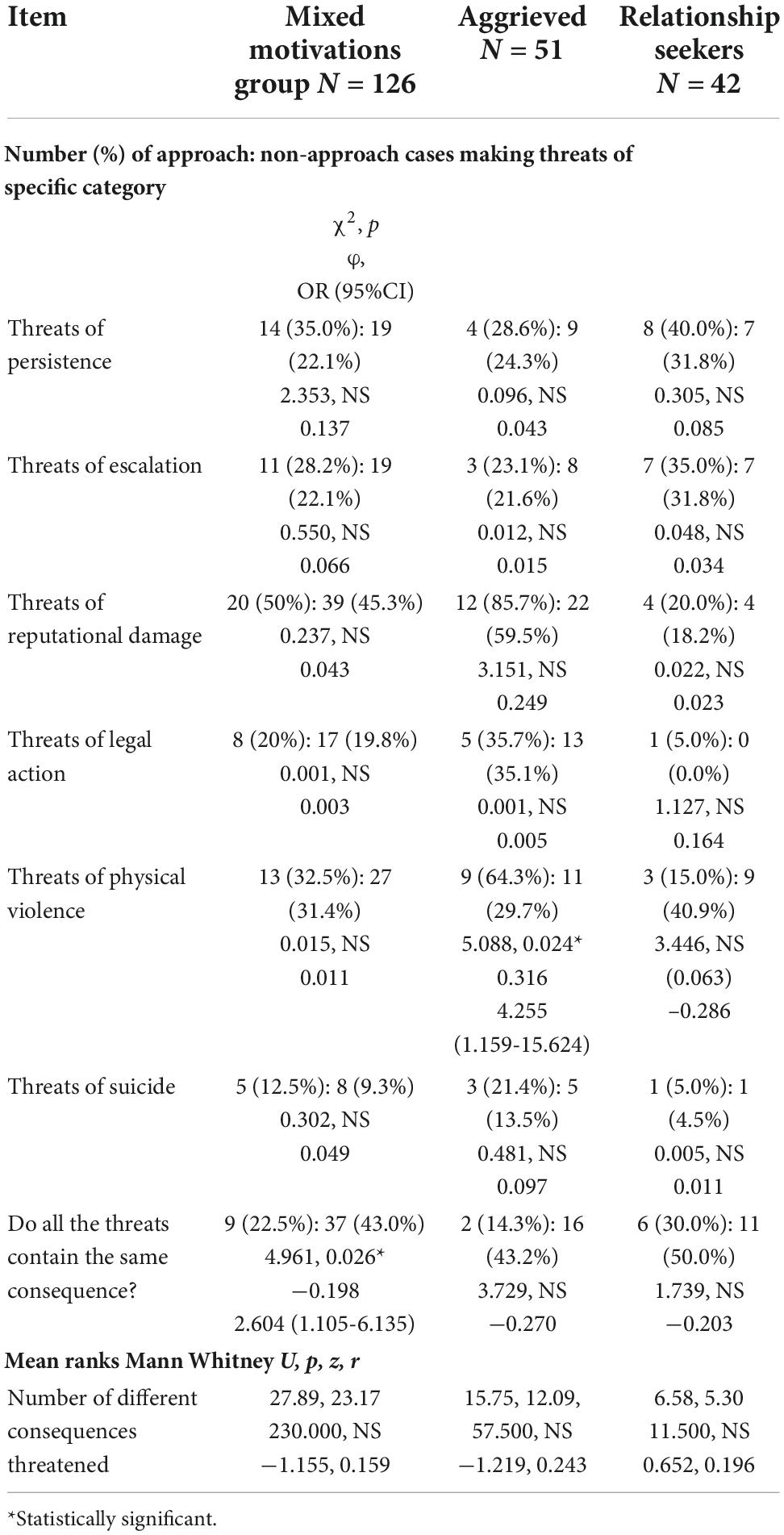
Associations between consequences threatened and approach
Whereas in the mixed motivations sample, there was no association between approach and threats of physical violence, a different picture emerged when looking at the aggrieved and the relationship seekers (refer to Table 6). In the aggrieved, there was a significant association between threats of physical violence and approach. In the relationship-seeking, there was an inverse relation between threats of physical violence and approach, which did not reach significance in this relatively small sample, although the effect size was –0.286. There were insufficient case numbers for meaningful analysis of disruption, financial damage, or sexual violence.
Plausibility
There were no significant associations between approach and any of the threat plausibility criteria – neither in the mixed motivations group, the aggrieved, nor the relationship seekers. All effect sizes were below 0.1.
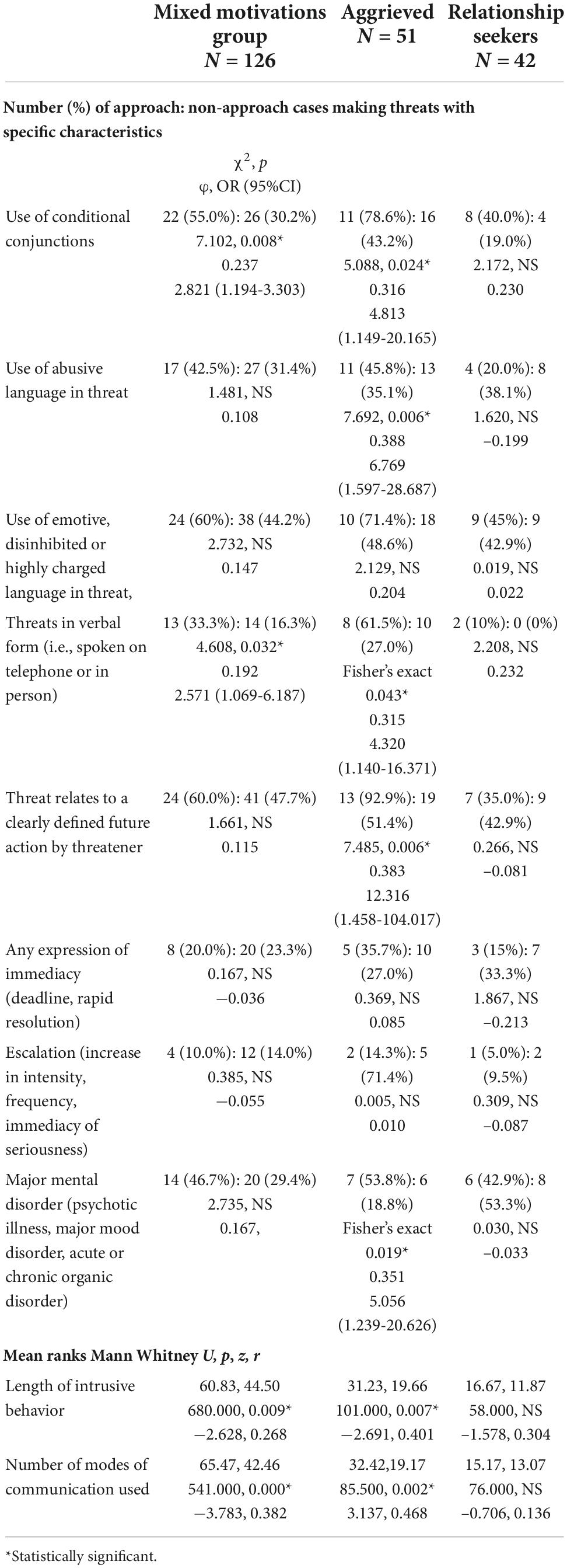
Associations between threat characteristics and approach
In total, three of the items examined concerned use of language (refer to Table 7). The use of conditional conjunctions (e.g., if, as long as, provided that, on condition that) was significantly associated with approach in the mixed motivations sample and the aggrieved. In the relationship seekers, there was no significant association in the small sub-sample, but the effect size was 0.230. The use of abusive language was significantly associated with approach in the aggrieved, but not in relationship seekers or the mixed motivations group. The use of emotive language produced no significant associations with approach, although the effect size in the aggrieved was 0.204.
Threats in verbal form were significantly associated with approach in the mixed motivations sample and the aggrieved, and there was an effect size of 0.232 in the relationship seekers. Threats relating to a clearly defined future action by the threatener were highly significantly associated with the approach in the aggrieved, but not in relationship seekers or the mixed motivations group. In the aggrieved, approach was further associated with the number of different modes of communication used (letters, e-mails, telephone, sms, etc.).
The study also looked at immediacy of the threat (e.g., containing deadlines or other expressions of imminence). It found no significant associations with approach, although the relationship seekers showed a negative effect size of −0.213. No associations were found between an escalation in threatening behaviour (i.e., threats becoming more frequent, intense, or serious in the consequences threatened) and approach in any group. However, persistence in terms of length of intrusive behaviour was significantly associated with approach in the all-motivations group and in the aggrieved, with an effect size of 0.304 found in the relationship seekers.
The question was examined as to whether the use of emotive language might depend upon intent category. Given the strong association between the “shocker” category of immediate intent and absence of approach, the item concerning emotive language was recalculated with all shocker cases excluded. The link between approach and the use of emotive language in the threats was highly significant in the mixed motivations sample: 23 (60.5%): 20 (32.8%), χ2 = 7.333, p = 0.007, φ = 0.272, OR 3.143 (1.354–7.295), and in the aggrieved sample 10 (76.9%): 6 (26.1%), χ2 = 8.693, p = 0.003, φ = 0.491, OR 9.444 (1.924–12.645), but not in the relationship-seeking sample: 9 (45%): 4 (28.6%), χ2 = 0.941, NS, 0.166.
Mental disorder
In aggrieved cases where threats had been made, approach was significantly associated with the presence of major mental disorder (refer to Table 7). No such association was found in the relationship seekers.
Discussion
This is the first study designed to examine the associations of threats with approach to public figures from the perspective of motivation, approach being selected as a convenient proxy for violence. It concentrated upon the aggrieved, comparing them with relationship seekers, setting them in the context of a study sample which involved a mixed group of motivations. Despite a modest sample size, the study was able to demonstrate that there are particular factors associated with approach in the aggrieved who threaten, and that the significance of these is largely lost, if study samples are analysed without taking account of underlying motivation. Similarly, there are particular factors that apply to relationship seekers, but not the aggrieved, although these are fewer in number.
Before considering how the results relate to the extant literature and discussing their implications for threat assessment, the results will be examined in terms of the four hypotheses around which the study was structured.
(1). The associations between making threats and approach will differ when the underlying motivation is one of grievance, compared with cases where the motivation is the seeking of a relationship.
In the aggrieved, those making indirect threats were significantly more likely to approach, whereas the reverse was the case in the relationship seekers (refer to Table 3). A similar differentiation was found in terms of the association between number of indirect threats and approach (Table 4). The aggrieved showed significant associations with approach in overall number of threats, number of direct threats, number of conditional threats, and number of categories of threat used. There were no such associations in the relationship seekers. The “scheming” threat category was significantly associated with approach in the aggrieved, but not in the relationship seekers (refer to Table 5). Threats of physical violence were associated with approach in the aggrieved. There was a trend for the reverse in the relationship seekers and, although this difference did not reach statistical significance in this sample, the effect size was −0.286 (refer to Table 6). The use of abusive language in the threats was associated with approach in the aggrieved: in the relationship seekers, the converse did not reach statistical significance, and the effect size was –0.232. Approach in the aggrieved was associated with the clarity of threatened consequence, but this did not apply in the relationship seekers (refer to Table 7). In addition, in cases where threats had been made, approach in the aggrieved was associated with the length of intrusive behaviour, the number of modes of communication used, and with the presence of major mental disorder. These associations were absent in relationship seekers (refer to Table 7). In summary, important differences were found between the aggrieved and relationship seekers in terms of associations between threats and approach.
(2). Associations identified between threats and approach in individual motivational groups will no longer be evident, if all the different motivational groups are considered together as one single group.
The results provided evidence that consideration of the general sample without accounting for motivation is likely to disguise significant differences which exist – in other words, that the study of sets of cases based on a sector of employment, such as politicians or celebrities, which combine groups with different threat profiles, flatten out the results and disguise real differences. The number of indirect threats made was significantly associated with approach in the aggrieved, but with non-approach in the relationship seekers: yet, no such differences appear in the whole mixed motivations sample (Table 4). Schemers are significantly more likely to approach in the aggrieved, but not in the relationship seekers, yet, no difference is found in the mixed motivation sample (Table 5). Threats of physical violence are significantly associated with approach in the aggrieved and there is a trend to non-approach in the relationship seekers: yet, no such significant differences are found when all motivations are taken together (Table 6). The use of abusive language is significantly associated with approach in the aggrieved, but not in relationship seekers: no association is present in the mixed motivation group. The same applies to the threats being clearly defined (Table 7). The length of intrusive behaviour is strongly associated with approach in the aggrieved group, and in the mixed motivation sample, but not in the relationship seekers. The same pattern applies to the number of modes of communication. In those that made threats, approach is significantly associated with the presence of major mental disorder, but not in relationship seekers or the mixed motivations sample.
(3). Between motivational groups, different associations with approach will be found according to the immediate purpose of making threats.
Sufficient numbers for analysis were present for two of the Mullen threat classification categories (Table 5). A significant difference was found, in that scheming was significantly associated with approach in the aggrieved, but not in the relationship seekers. In both the aggrieved and the relationship seekers, shocking was associated with non-approach. This will be discussed further later.
(4). The form of harm threatened may be linked with the likelihood of subsequent approach.
It is notable that threats of physical violence were significantly associated with approach in the aggrieved, with a trend towards non-approach in the relationship seekers (refer to Table 6). However, there was little indication of any differences with threats of persistence, escalation, legal action, or suicide. No significant differences were found for three further items, threats of reputational damage, cases where the threats all containing the same consequences, or the number of different consequences threatened. However, the effect sizes in these items indicate that the relationships are worthy of further exploration in larger samples.
In summary, the results offered considerable support to the hypotheses under consideration. Our contention would be that consideration of the risk of adverse outcomes in those who make threatening or otherwise concerning intrusions into the lives of those in the public eye would benefit from incorporating the principals elucidated for the evaluation of risk in stalking, harassment, and threats in other populations (Mullen et al., 1999; MacKenzie et al., 2009). In other words, the top level in the hierarchy of examination should be the consideration of underlying motivation, rather than the nature of the victims’ employment. Furthermore, assessment should recognise that risk factors will differ according to the particular form of potential adverse outcome concerned. These principals apply equally well to the study of the making of threats as they do to other forms of harassing communication and physical intrusion. With threats, there is a third major element to consider and that is the question as to the immediate purpose of the threat to the threatener. Issues of mode and form of threat require consideration, but are generally subsidiary to the above.
The issue concerning motivation, to put it at its most banal, is that those motivated by love are unlikely to behave in the same way as those motivated by hate. In this study, it has been shown that risk factors associated with moving from threat to approach differ in important ways between those motivated by seeking a relationship and those fuelled by grievance. Lumping all motivations into one, as in other studies described above, blurs differences, as might be expected by the proverbial mixing of apples and oranges. A few characteristics are held in common, but many are not. The difference in conclusions between previous studies of celebrities and those of politicians can be explained by the predominance of a different motivation – relationship-seeking with celebrity cases and grievance with politicians. Differences in findings between studies within one sector (such as in threats and approach in celebrity cases between Dietz et al., 1991a and Meloy et al., 2008) are likely to be accounted for by variations in the motivational mix of the samples, different definitions of risk, and the difficulties of the retrospective study of case files assembled for other purposes.
The study is unusual, in that it used a classification for the immediate purpose of the threats made. Of particular interest, here is the finding that the Mullen classificational group, “shockers,” is firmly associated with non-approach in both the motivational groups studied: indeed, in this comparatively small sample, only 5% of “shockers” of any motivation went on to approach. “Shockers” are the cases where the threats were made to inflict emotional pain. This would appear to be an end in itself, which is not associated with a need for further action. This finding is linked to the differentiation made by Calhoun (1998) between “hunters” and “howlers,” in other words, those who “shout” and those who go on to act, which is also reflective of the differentiation between making and posing a threat. The finding about “shockers” may also be key to understanding some of the differences between the findings of this motivational study and those of samples of politicians, where the making of threats was negatively associated with the approach (Dietz et al., 1991b; Scalora et al., 2002a,b). In those studies, the most frequent motivation would appear to be that of grievance, although the samples are a mix of motivations. Our suggestion is that the cases included sufficient a proportion of “shockers” as to determine a significant association between threats and non-approach. Some evidence for this can be found in the details of the studies. For instance, in the study of members of congress by Dietz et al. (1991b), in which threats were significantly associated with non-approach, there were significant negative associations between approach and “attempts to instil fear in the politician,” “attempts to frighten the politician,” “attempts to instil worry in the politician,” and “attempts to provoke upset in the politician.” These items would appear to be encompassed by the Mullen “shocker” category. In the studies by Dietz et al. of inappropriate communications to celebrities, these data points do not appear. Yet, it is notable that only 5% of respondents cast themselves in the role of “enemies,” compared with 40% in the study of members of congress. No relation between threat and approach was found in this study. It may be that the relative absence of “shockers” in this sample determined the difference in this respect between the politicians and celebrities. It is also possible that the inclusion of ‘shockers’ in samples may have affected the findings in terms of a lack of association between direct threats and approach: for, direct threats are likely to be over-represented amongst ‘shockers’, given that indirect or veiled threats have less in the way of shock quality.
Other general observations from the study are that threats are very common in the study sample, being present in 77.8% of cases – and significantly more common in the aggrieved than the relationship seekers. In the aggrieved, but not in the relationship-seeking, length of intrusive behaviour and number of modes of communication were significantly associated with approach, as was mental disorder. The first two of these might be taken as an indication of persistence, rather than intensity, as it is of note that expressions of immediacy (e.g., deadlines) and indications of recent escalation were not associated with approach in those who made threats. Nor did the indicators of plausibility or implausibility show any significant effects. It might be theorised that issues of commitment, immediacy, and practicality are subsumed to some degrees within the question as to the immediate purpose of a threat: or that plausibility is of less import to an individual who is mentally ill. Finally, a significant association between mental disorder and approach in those that threatened was found in the aggrieved, but not in the relationship seekers, although the proportion of cases with mental disorder was greater in the latter. A possible explanation is that the nature of the mental illness may differ between the two motivational groups, with a greater proportion of delusional disorders in the aggrieved, and of schizophrenia in the relationship seekers. The findings of the study in terms of threats and the associations of approach are summarised in Table 8 for the ease of comparison of the “profiles” of the aggrieved and relationship seekers.
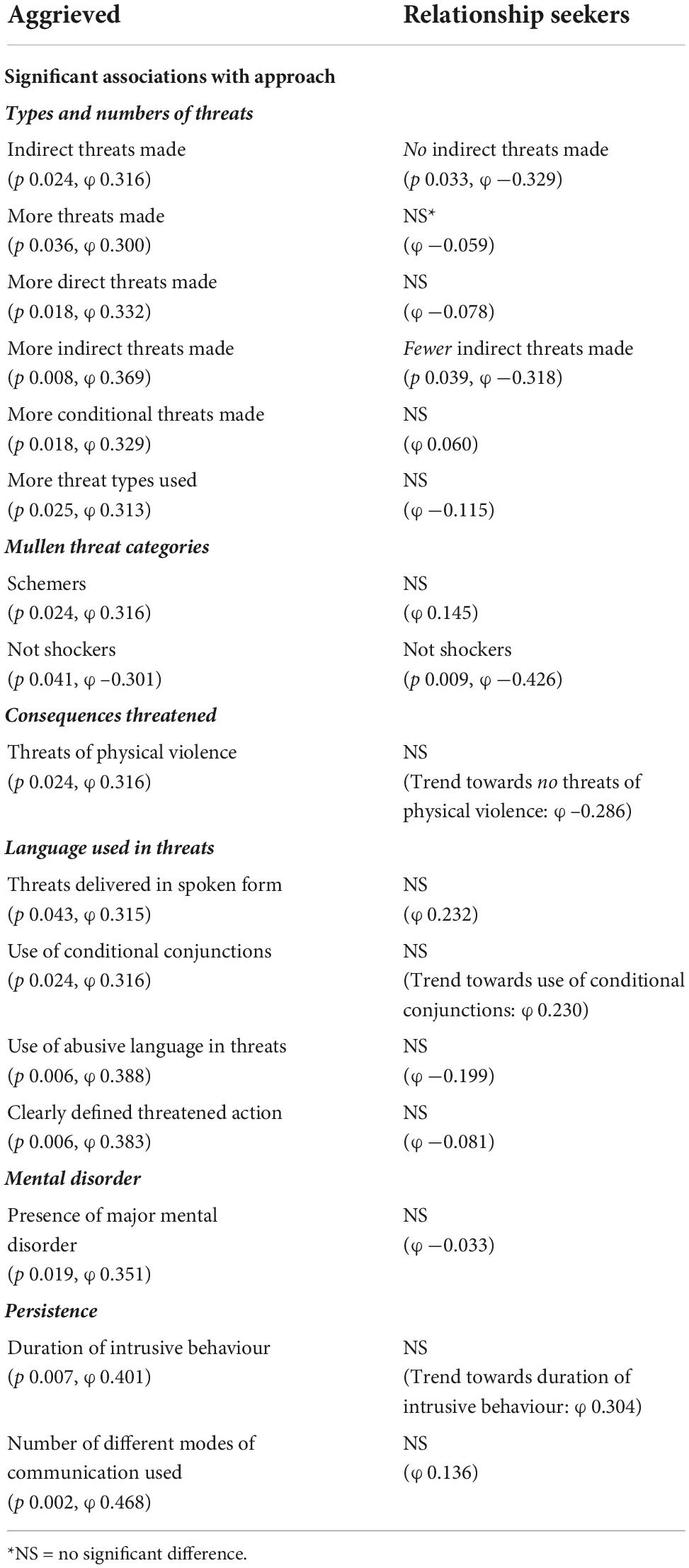
Table 8. Summary of differences in significant associations with approach between aggrieved and relationship-seekers threateners.
Limitations
The limitations to this study are self-evident. The sample size, at 126 cases, was relatively small, particularly in the sub-groups, and significant associations are likely to have been missed which would have become apparent, had a larger sample been used. In addition, there were insufficient numbers to examine all the categories in the motivational typology, or all those in the typology of intent. Some of these limitations may have been offset to a degree by the use of effect sizes as additional indices, and by the improved methodological purity and exactitude when compared with previous studies. It would evidently be desirable to repeat the exercise with larger numbers and in samples of different origin, despite the complexities and time that would be involved. Sampling procedures in future studies could usefully be designed in method to ensure roughly equal numbers of threateners and non-threateners. Second, this study did not examine violence directly, but rather approach as a proxy for violence. The use of a proxy was unavoidable given the low base rate of violence, and the choice of approach as a proxy at least enabled comparison with previous studies.
Conclusion
As to what this study can contribute to the consideration of grievance-fuelled violence, (the expanding literature on which this is not the place to summarise), it provides a few small pieces to a very much larger jigsaw. It is through the availability of such comparative material, from different fields, that improvement may be made in the identification of risk factors to incorporate into population-based preventative approaches. The latter remain relatively primitive in that they aim to apply a rather coarse filter to an understanding of motives and interactions which are affected and modified by highly individual factors and events in a person’s life which cannot readily be captured through forms of screening: and the low base rate of violence makes the proportion of false positives high in any such screening process. Nevertheless, screening based on risk factors remains the principal tool available, and further consideration of individual and dynamic risk factors that cannot be incorporated into the design of such screens can later be applied to cases “screened-in” and to the design of interventions at an individual level.
The study dealt with the specific issues of the making of threats and their relevance to risk of approach, as a proxy for violence. Perhaps, its main contribution is methodological. Our principal conclusion would be that differences in motivation and in immediate purpose of threats should both be incorporated into future studies in the area of threats to people in the public eye, and other groups besides. We have suggested ways in which this could be done.
Data availability statement
The datasets presented in this article are available to suitably qualified academic researchers upon request to the lead author.
Author contributions
DJ designed the project, co-ordinated the analyses, and was principal writer. FF, PA, AM, CS, and AW contributed equally to the various stages of the project. All authors contributed to the article and approved the submitted version.
Conflict of interest
No direct financial benefits accrued to the authors from the conducting of this research. PA and AW are directors of Theseus Ltd., in which they have a financial interest. DJ is a non-salaried advisor to Theseus Ltd. DJ is a co-author of the Stalking Risk Profile, from which he receives no financial benefit.
The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
Footnotes
References
Barry-Walsh, J., James, D. V., and Mullen, P. E. (2020). Fixated threat assessment centers: Preventing harm and facilitating care in public figure threat cases and those thought to be at risk of lone-actor grievance-fuelled violence. CNS Spectr. 25, 630–637. doi: 10.1017/S1092852920000152
Calhoun, F. S. (1998). Hunters and howlers: Threats and violence against federal judicial officials in the United States, 1789-1993. Arlington, VA: Department of Justice, U.S. Marshals Service.
Capellan, J. A. (2015). Lone-wolf terrorist or deranged shooter? A study of ideological active shooter events in the United States, 1970-2014. Stud. Confl. Terror. 38, 395–413. doi: 10.1080/1057610X.2015.1008341
Clemmow, C., Gill, P., Bouhana, N., Silver, J., and JHorgan, J. (2022). Disaggregating lone-actor grievance-fuelled violence: Comparing lone-actor terrorists and mass murderers. Terror. Polit. Violence 34, 558–584. doi: 10.1080/09546553.2020.1718661
Cohen, J. (1988). Statistical power analysis for the behavioral sciences, 2nd Edn. Hillsdale, NJ: Lawrence Erlbaum.
Dietz, P. E., and Martell, D. A. (1989). Mentally disordered offenders in pursuit of celebrities and politicians. Washington, DC: National Institute of Justice.
Dietz, P. E., Matthews, D. B., Martell, D. A., Stewart, T. M., Hrouda, D. R., and Warren, J. (1991b). Threatening and otherwise inappropriate letters to members of the United States congress. J. Forensic Sci. 36, 1445–1468. doi: 10.1520/JFS13165J
Dietz, P., Matthews, D., Van Duyne, C., Martell, D., Parry, C., Stewart, T., et al. (1991a). Threatening and otherwise inappropriate letters to hollywood celebrities. J. Forensic Sci. 36, 185–209. doi: 10.1520/JFS13019J
Eke, A. W., Meloy, J. R., Brooks, K., Jean, L., and Hilton, N. Z. (2014). Threats, approach behaviour, and violent recidivism among offenders who harass Canadian justice officials. J. Threat Assess. Manage. 1, 188–202. doi: 10.1037/tam0000016
Fein, R. A., and Vossekuil, B. (1999). Assassination in the United States: An operational study of recent assassins, attackers, and near-lethal approachers. J. Forensic Sci. 44, 321–333. doi: 10.1520/JFS14457J
Hoffman, J., Meloy, J. R., Guldiman, A., and Ermer, A. (2011). Attacks on German public figures, 1968-2004. Warning behaviours, potentially lethal and non-lethal acts, psychiatric status, and motivations. Behav. Sci. Law 29, 155–179. doi: 10.1002/bsl.979
James, D. V., MacKenzie, R. D., Allen, P., Wolfe Murray, A., De Silva, A., Yang, J., et al. (2022). Factors associated with approach and persistence in corporate threat assessment cases: The validity of the CTAP. J. Threat Assess. Manage. Advance online publication. doi: 10.1037/tam0000180 [Epub ahead of print].
James, D. V., McEwan, T. E., MacKenzie, R. D., Meloy, J., Mullen, P. E., Pathé, M. T., et al. (2010). Persistence in stalking: A comparison of associations in general forensic and public figure samples. J. Forensic Psychiatry Psychol. 21, 283–305. doi: 10.1080/14789940903388994
James, D. V., Mullen, P. E., Meloy, J. R., Pathé, M. T., Farnham, F. R., Preston, L., et al. (2007). The role of mental disorder in attacks on european politicians 1990-2004. Acta Psychiatr. Scand. 116, 334–344. doi: 10.1111/j.1600-0447.2007.01077.x
James, D. V., Mullen, P. E., Pathé, M. T., Meloy, J. R., Farnham, F. R., Preston, L., et al. (2008). Attacks on the british royal family: The role of psychotic illness. J. Am. Acad. Psychiatry Law 36, 59–67.
James, D. V., Mullen, P. E., Pathé, M. T., Meloy, J. R., Farnham, F. R., Preston, L., et al. (2010a). Stalkers and harassers of royalty: An exploration of proxy behaviours for violence. Behav. Sci. Law 29, 64–80. doi: 10.1002/bsl.922
Lankford. (2012). A comparative analysis of suicide terrorists and rampage, workplace, and school shooters in the United States from 1990 to 2010. Homicide Stud. 17, 255–274. doi: 10.1177/1088767912462033
MacKenzie, R. D., McEwan, T. E., Patheì, M. T., James, D. V., Ogloff, J. R. P., and Mullen, P. E. (2009). The stalking risk profile: Guidelines for the assessment and management of stalkers. Melbourne, VA: StalkInc.
MacKenzie, R. D., Mullen, P. E., Ogloff, J. R. P., McEwan, T. E., and James, D. V. (2008). Parental bonding and adult attachment styles in different types of stalker. J. Forensic Sci. 53, 1443–1449. doi: 10.1111/j.1556-4029.2008.00869.x
McCauley, C., Moskalenko, S., and van Sohn, B. (2013). Characteristics of lone-wolf violent offenders: A comparison of assassins & school attackers. Perspect. Terror. 7, 4–24.
McEwan, T. E., Daffern, M., MacKenzie, R. D., and Ogloff, J. R. P. (2017). Risk factors for stalking violence, persistence and recurrence. J. Forensic Psychiatry Psychol. 28, 38–56. doi: 10.1080/14789949.2016.1247188
McEwan, T. E., Mullen, P. E., and MacKenzie, R. (2009a). A study of the predictors of persistence in stalking situations. Law Hum. Behav. 33, 149–158. doi: 10.1007/s10979-008-9141-0
McEwan, T. E., Mullen, P. E., MacKenzie, R. D., and Ogloff, J. R. P. (2009b). Violence in stalking situations. Psychol. Med. 39, 1469–1478.
McEwan, T. E., Shea, D. E., Daffern, M., MacKenzie, R. D., Ogloff, J., and Mullen, P. E. (2018). The reliability and predictive validity of the stalking risk profile. Assessment 25, 259–276. doi: 10.1177/1073191116653470
McKenzie, D. P., and Thomas, C. (2020). Relative risks and odds ratios: Simple rules on when and how to use them. Eur. J. Clin. Invest. 50:e13249. doi: 10.1111/eci.13249
Meloy, J. R. (2000). Violence risk and threat assessment. San Diego, CA: Specialized Training Services.
Meloy, J. R. (2014). Approaching and attacking public figures: A contemporary analysis of communications and behavior. J. Threat Assess. Manage. 1, 243–261. doi: 10.1037/tam0000024
Meloy, J. R., Hoffman, J., Bibeau, L., and Guldimann, A. (2021). “Warning behaviours,” in International handbook of threat assessment, 2nd Edn, eds J. R. Meloy and J. Hoffmann (New York, NY: Oxford University Press), 45–67. doi: 10.1093/med-psych/9780190940164.003.0003
Meloy, J. R., Hoffmann, J., Guldimann, A., and James, D. V. (2012). The role of warning behaviors in threat assessment: An exploration and suggested typology. Behav. Sci. Law 30, 256–279. doi: 10.1002/bsl.999
Meloy, J. R., James, D. V., Mullen, P. E., Pathé, M. T., Farnham, F. R., Preston, L. F., et al. (2011). Factors associated with escalation and problematic approaches toward public figures. J. Forensic Sci. 56(Suppl. 1), S128–S135. doi: 10.1111/j.1556-4029.2010.01574.x
Meloy, J. R., Mohandie, K., and Green, M. (2008). “A forensic investigation of those who stalk celebrities,” in Stalking, threatening and attacking public figures, eds J. R. Meloy, L. Sheridan, and J. Hoffman (New York, NY: Oxford University Press), 37–54. doi: 10.1002/bsl.2252
Mullen, P. E., James, D. V., Meloy, J. R., Pathé, M. T., Farnham, F. R., Preston, L., et al. (2009b). The fixated and the pursuit of public figures. J. Forensic Psychiatry Psychol. 20, 33–47. doi: 10.1080/14789940802197074
Mullen, P. E., Pathé, M., and Purcell, R. (2009a). Stalkers and their victims. Cambridge: Cambridge University Press.
Mullen, P. E., Pathé, M., and Purcell, R. (2009b). Stalkers and their victims, 2nd Edn. Cambridge: Cambridge University Press.
Mullen, P. E., Pathé, M., Purcell, R., and Stuart, G. W. (1999). Study of stalkers. Am. J. Psychiatry 156, 1244–1249. doi: 10.1176/ajp.156.8.1244
Nakagawa, S., and Cuthill, I. C. (2007). Effect size, confidence interval and statistical significance: A practical guide for biologists. Biol. Rev. Camb. Philos. Soc. 82, 591–605. doi: 10.1111/j.1469-185X.2007.00027.x
Norton, E. C., Dowd, B. E., and Maciejewski, M. L. (2018). Odds ratios-current best practice and use. J. Am. Med. Assoc. 320, 84–85. doi: 10.1001/jama.2018.6971
Pathé, M. T., Haworth, D. J., Goodwin, T., Holman, A. G., Amos, S. J., Winterbourne, P., et al. (2018). Establishing a joint agency response to the threat of lone-actor grievance-fuelled violence. J. Forensic Psychiatry Psychol. 29, 37–52. doi: 10.1080/14789949.2017.1335762
Pinals, D.A. (ed.) (2007). Stalking: Psychiatric perspectives and practical approaches. Group for the advancement of psychiatry. New York, NY: Oxford University Press.
Rosenthal, R. (1991). Meta-analytic procedures for social research, 2nd Edn. Newbury Park, CA: Sage.
Scalora, M. J., Baumgartner, J. V., Callaway, D., Zimmerman, W., Hatch-Maillette, M. A., Covell, C. N., et al. (2002a). An epidemiological assessment of problematic contacts to members of congress. J. Forensic Sci. 47, 1360–1364. doi: 10.1520/JFS15575J
Scalora, M. J., Baumgartner, J. V., Zimmerman, W., Callaway, D., Hatch-Maillette, M. A., Covell, C. N., et al. (2002b). Risk factors for approach behavior toward the U.S. congress. J. Threat Assess. 2, 35–55. doi: 10.1300/J177v02n02_03
Schoeneman, K. A., Scalora, M. J., Darrow, C. D., McLawsen, J. E., Chang, G. H., and Zimmerman, W. J. (2011). Written content indicators of problematic approach behavior toward political officials. Behav. Sci. Law 29, 284–301. doi: 10.1002/bsl.977
Siegel, S., and Castellan, N. J. (1988). Nonparametric Statistics for the Behavioral Sciences, 2nd Edn. New York, NY: McGraw-Hill.
van der Meer, B., Bootsma, L., and Meloy, J. R. (2012). Disturbing communications and problematic approaches to the dutch royal family. J. Forensic Psychiatry Psychol. 23, 571–589. doi: 10.1080/14789949.2012.727453
Warren, L., Mullen, P. E., and McEwan, T. (2014). “Explicit threats of violence,” in International handbook of threat assessment, eds J. R. Meloy and J. L. Hoffman (New York, NY: Oxford University Press), 18–38.
Wilson, S. P., Patheì, M. T., Farnham, F. R., and James, D. V. (2021). “The fixated threat assessment centers,” in International handbook of threat assessment, 2nd Edn, eds J. R. Meloy and J. Hoffmann (New York, NY: Oxford University Press), 475–491. doi: 10.1093/med-psych/9780190940164.003.0027
Keywords: grievance, violence, fixation, mental health, security, lone-actor grievance-fuelled violence
Citation: James DV, Farnham FR, Allen P, Martinsone A, Sneader C and Wolfe Murray A (2022) Threats to public figures and association with approach, as a proxy for violence: The importance of grievance. Front. Psychol. 13:998155. doi: 10.3389/fpsyg.2022.998155
Received: 19 July 2022; Accepted: 20 September 2022;
Published: 26 October 2022.
Edited by:
Emily Corner, Australian National University, AustraliaReviewed by:
Nathan Brooks, New Zealand Police, New ZealandTroy McEwan, Swinburne University of Technology and Forensicare, Australia
Copyright © 2022 James, Farnham, Allen, Martinsone, Sneader and Wolfe Murray. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: David V. James, david.j@theseusrisk.com
 David V. James
David V. James Frank R. Farnham2,3
Frank R. Farnham2,3 Philip Allen
Philip Allen Ance Martinsone
Ance Martinsone Charlie Sneader
Charlie Sneader