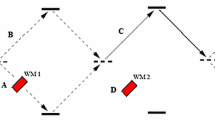
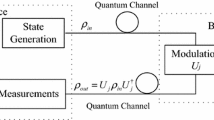
A simple fundamental modification of quantum key distribution protocols has been proposed: it is not required to protect the results of avalanche detectors from an eavesdropper, but all cryptographic properties of a protocol hold.

Similar content being viewed by others
Notes
To avoid misunderstanding, we note that the consideration below concerns the standard point–point configuration rather than twin-field quantum cryptography systems (see below).
The idea of interference of states from different sources in quantum key distribution was proposed as early as in 1997 in [5]; this system was called quantum key distribution based on a quantum computer.
REFERENCES
C. H. Bennett and G. Brassard, in Proceedings of the IEEE International Conference on Computers, Systems & Signal Processing, Bangalore, India, Dec. 9–12, 1984, p. 175.
S. N. Molotkov, Laser Phys. Lett. 16, 075203 (2019).
M. Lucamarini, L. M. Yuan, J. F. Dynes, and A. J. Shields, Nature (London, U.K.) 557, 400 (2018).
S. N. Molotkov and I. V. Sinilshchikov, Laser Phys. Lett. 16, 105205 (2019).
S. N. Molotkov, JETP Lett. 66, 773 (1997).
S. N. Molotkov, Laser Phys. Lett. 18, 045202 (2021).
S. N. Molotkov, J. Exp. Theor. Phys. 133, 272 (2021).
K. Kraus, States, Effects and Operations: Fundamental Notions of Quantum Theory (Springer, Berlin, 1983).
W. F. Stinespring, Proc. Am. Math. Soc. 6, 211 (1955).
R. Renner, PhD Thesis (ETH Zürich, Switzerland, 2005); arXiv: 0512258.
Funding
S.P. Kulik acknowledges the support of the Interdisciplinary Scientific Educational School “Photon and Quantum Technologies. Digital Medicine,” Moscow State University.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
The authors declare that they have no conflicts of interest.
Additional information
Translated by R. Tyapaev
Rights and permissions
About this article
Cite this article
Balygin, K.A., Kulik, S.P. & Molotkov, S.N. Quantum Key Distribution with Untrusted Detectors Accessible to an Eavesdropper. Jetp Lett. 116, 128–132 (2022). https://doi.org/10.1134/S0021364022601142
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1134/S0021364022601142