Abstract
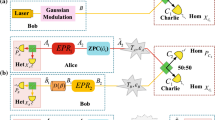
We propose a novel scheme for measurement-device-independent (MDI) continuous-variable quantum key distribution (CVQKD) by simultaneously conducting classical communication and QKD, which is called “simultaneous MDI-CVQKD” protocol. In such protocol, each sender (Alice, Bob) can superimpose random numbers for QKD on classical information by taking advantage of the same weak coherent pulse and an untrusted third party (Charlie) decodes it by using the same coherent detectors, which could be appealing in practice due to that multiple purposes can be realized by employing only single communication system. What is more, the proposed protocol is MDI, which is immune to all possible side-channel attacks on practical detectors. Security results illustrate that the simultaneous MDI-CVQKD protocol can secure against arbitrary collective attacks. In addition, we employ phase-sensitive optical amplifiers to compensate the imperfection existing in practical detectors. With this technology, even common practical detectors can be used for detection through choosing a suitable optical amplifier gain. Furthermore, we also take the finite-size effect into consideration and show that the whole raw keys can be taken advantage of to generate the final secret key instead of sacrificing part of them for parameter estimation. Therefore, an enhanced performance of the simultaneous MDI-CVQKD protocol can be obtained in finite-size regime.
Similar content being viewed by others
References
S. Pirandola, U. L. Andersen, L. Banchi, M. Berta, D. Bunandar, R. Colbeck, D. Englund, T. Gehring, C. Lupo, C. Ottaviani, J. Pereira, M. Razavi, J. S. Shaari, M. Tomamichel, V. C. Usenko, G. Vallone, P. Villoresi, and P. Wallden, Advances in quantum cryptography, arXiv: 1906.01645 (2019)
E. Diamanti, H.-K. Lo, B. Qi, and Z. Yuan, Practical challenges in quantum key distribution, npj Quantum Inf. 2, 16025 (2016)
H. K. Lo, M. Curty, and K. Tamaki, Secure quantum key distribution, Nat. Photonics 8(8), 595 (2014)
N. Gisin, G. Ribordy, W. Tittel, and H. Zbinden, Quantum cryptography, Rev. Mod. Phys. 74(1), 145 (2002)
V. Scarani, H. Bechmann-Pasquinucci, N. J. Cerf, M. Dušek, N. Lütkenhaus, and M. Peev, The security of practical quantum key distribution, Rev. Mod. Phys. 81(3), 1301 (2009)
C. Weedbrook, S. Pirandola, R. García-Patrón, N. J. Cerf, T. C. Ralph, J. H. Shapiro, and S. Lloyd, Gaussian quantum information, Rev. Mod. Phys. 84(2), 621 (2012)
L. M. Liang, S. H. Sun, M. S. Jiang, and C. Y. Li, Security analysis on some experimental quantum key distribution systems with imperfect optical and electrical devices, Front. Phys. 9(5), 613 (2014)
A. K. Ekert, Quantum cryptography based on Bell’s theorem, Phys. Rev. Lett. 67(6), 661 (1991)
H. K. Lo and H. F. Chau, Unconditional security of quantum key distribution over arbitrarily long distances, Science 283(5410), 2050 (1999)
J. Y. Wang, B. Yang, S. K. Liao, L. Zhang, Q. Shen, X. F. Hu, J. C. Wu, S. J. Yang, H. Jiang, Y. L. Tang, B. Zhong, H. Liang, W. Y. Liu, Y. H. Hu, Y. M. Huang, B. Qi, J. G. Ren, G. S. Pan, J. Yin, J. J. Jia, Y. A. Chen, K. Chen, C. Z. Peng, and J. W. Pan, Direct and full-scale experimental verifications towards ground–satellite quantum key distribution, Nat. Photonics 7(5), 387 (2013)
M. Lucamarini, Z. L. Yuan, J. F. Dynes, and A. J. Shields, Overcoming the rate-distance limit of quantum key distribution without quantum repeaters, Nature 557(7705), 400 (2018)
A. Farouk, J. Batle, M. Elhoseny, M. Naseri, M. Lone, A. Fedorov, M. Alkhambashi, S. H. Ahmed, and M. Abdel-Aty, Robust general N user authentication scheme in a centralized quantum communication network via generalized GHZ states, Front. Phys. 13(2), 130306 (2018)
F. Grosshans and P. Grangier, Continuous variable quantum cryptography using coherent states, Phys. Rev. Lett. 88(5), 057902 (2002)
F. Grosshans, G. Van Assche, J. Wenger, R. Brouri, N. J. Cerf, and P. Grangier, Quantum key distribution using gaussian-modulated coherent states, Nature 421(6920), 238 (2003)
T. C. Ralph, Continuous variable quantum cryptography, Phys. Rev. A 61(1), 010303 (1999)
F. Laudenbach, C. Pacher, C. H. F. Fung, A. Poppe, M. Peev, B. Schrenk, M. Hentschel, P. Walther, and H. Hübel, Continuous-variable quantum key distribution with Gaussian modulation–the theory of practical implementations, Adv. Quantum Technol. 1(1), 1800011 (2018)
B. Qi, L. L. Huang, L. Qian, and H. K. Lo, Experimental study on the Gaussian-modulated coherent-state quantum key distribution over standard telecommunication fibers, Phys. Rev. A 76(5), 052323 (2007)
X. D. Wu, Q. Liao, D. Huang, X. H. Wu, and Y. Guo, Balancing four-state continuous-variable quantum key distribution with linear optics cloning machine, Chin. Phys. B 26(11), 110304 (2017)
W. Liu, P. Huang, J. Peng, J. Fan, and G. Zeng, Integrating machine learning to achieve an automatic parameter prediction for practical continuous-variable quantum key distribution, Phys. Rev. A 97(2), 022316 (2018)
T. Wang, P. Huang, Y. Zhou, W. Liu, and G. Zeng, Practical performance of real-time shot-noise measurement in continuous-variable quantum key distribution, Quantum Inform. Process. 17(1), 11 (2018)
R. García-Patrón and N. J. Cerf, Unconditional optimality of gaussian attacks against continuous-variable quantum key distribution, Phys. Rev. Lett. 97, 190503 (2006)
P. Huang, J. Fang, and G. Zeng, State-discrimination attack on discretely modulated continuous-variable quantum key distribution, Phys. Rev. A 89(4), 042330 (2014)
X. D. Wu, Y. J. Wang, H. Zhong, Q. Liao, and Y. Guo, Plug-and-play dual-phase-modulated continuous-variable quantum key distribution with photon subtraction, Front. Phys. 14(4), 41501 (2019)
C. Xie, J. Zhang, Q. Pan, X. Jia, and K. Peng, Continuous variable quantum communication with bright entangled optical beams, Front. Phys. China 1(4), 383 (2006)
S. Pirandola, S. L. Braunstein, and S. Lloyd, Characterization of collective Gaussian attacks and security of coherent-state quantum cryptography, Phys. Rev. Lett. 101(20), 200504 (2008)
R. Renner and J. I. Cirac, de Finetti representation theorem for infinite-dimensional quantum systems and applications to quantum cryptography, Phys. Rev. Lett. 102(11), 110504 (2009)
A. Leverrier, F. Grosshans, and P. Grangier, Finite-size analysis of a continuous-variable quantum key distribution, Phys. Rev. A 81(6), 062343 (2010)
F. Furrer, T. Franz, M. Berta, A. Leverrier, V. B. Scholz, M. Tomamichel, and R. F. Werner, Continuous variable quantum key distribution: finite-key analysis of composable security against coherent attacks, Phys. Rev. Lett. 109(10), 100502 (2012)
A. Leverrier, R. García-Patrón, R. Renner, and N. J. Cerf, Security of continuous-variable quantum key distribution against general attacks, Phys. Rev. Lett. 110(3), 030502 (2013)
A. Leverrier, Composable security proof for continuous-variable quantum key distribution with coherent states, Phys. Rev. Lett. 114(7), 070501 (2015)
D. Huang, P. Huang, D. Lin, and G. Zeng, Long-distance continuous-variable quantum key distribution by controlling excess noise, Sci. Rep. 6(1), 19201 (2016)
D. Huang, P. Huang, H. Li, T. Wang, Y. Zhou, and G. Zeng, Field demonstration of a continuous-variable quantum key distribution network, Opt. Lett. 41(15), 3511 (2016)
P. Jouguet, S. Kunz-Jacques, A. Leverrier, P. Grangier, and E. Diamanti, Experimental demonstration of long-distance continuous-variable quantum key distribution, Nat. Photonics 7(5), 378 (2013)
C. Wang, D. Huang, P. Huang, D. Lin, J. Peng, and G. Zeng, 25 MHz clock continuous-variable quantum key distribution system over 50 km fiber channel, Sci. Rep. 5(1), 14607 (2015)
G. Brassard, N. Lütkenhaus, T. Mor, and B. C. Sanders, Limitations on practical quantum cryptography, Phys. Rev. Lett. 85(6), 1330 (2000)
Z. Yuan, J. Dynes, and A. Shields, Avoiding the blinding attack in QKD, Nat. Photonics 4(12), 800 (2010)
J. Z. Huang, S. Kunz-Jacques, P. Jouguet, C. Weedbrook, Z. Q. Yin, S. Wang, W. Chen, G. C. Guo, and Z. F. Han, Quantum hacking on quantum key distribution using homodyne detection, Phys. Rev. A 89(3), 032304 (2014)
P. Jouguet, S. Kunz-Jacques, and E. Diamanti, Preventing calibration attacks on the local oscillator in continuous-variable quantum key distribution, Phys. Rev. A 87(6), 062313 (2013)
X. C. Ma, S. H. Sun, M. S. Jiang, and L. M. Liang, Local oscillator fluctuation opens a loophole for Eve in practical continuous-variable quantum-key-distribution systems, Phys. Rev. A 88(2), 022339 (2013)
X. C. Ma, S. H. Sun, M. S. Jiang, and L. M. Liang, Wavelength attack on practical continuous-variable quantum-key-distribution system with a heterodyne protocol, Phys. Rev. A 87(5), 052309 (2013)
H. Qin, R. Kumar, V. Makarov, and R. Alléaume, Homodyne-detector-blinding attack in continuous-variable quantum key distribution, Phys. Rev. A 98(1), 012312 (2018)
H. Qin, R. Kumar, and R. Alléaume, Saturation attack on continuous-variable quantum key distribution system, Proc. SPIE 8899, 88990N (2013)
S. L. Braunstein and S. Pirandola, Side-channel-free quantum key distribution, Phys. Rev. Lett. 108(13), 130502 (2012)
H. K. Lo, M. Curty, and B. Qi, Measurement-device-independent quantum key distribution, Phys. Rev. Lett. 108(13), 130503 (2012)
F. Xu, M. Curty, B. Qi, and H. K. Lo, Practical aspects of measurement-device-independent quantum key distribution, New J. Phys. 15(11), 113007 (2013)
X. B. Wang, Three-intensity decoy-state method for device-independent quantum key distribution with basis-dependent errors, Phys. Rev. A 87(1), 012320 (2013)
M. Curty, F. Xu, W. Cui, C. C. W. Lim, K. Tamaki, and H. K. Lo, Finite-key analysis for measurement-device-independent quantum key distribution, Nat. Commun. 5(1), 3732 (2014)
C. Ottaviani, G. Spedalieri, S. L. Braunstein, and S. Pirandola, Continuous-variable quantum cryptography with an untrusted relay: Detailed security analysis of the symmetric configuration, Phys. Rev. A 91(2), 022320 (2015)
P. Papanastasiou, C. Ottaviani, and S. Pirandola, Finitesize analysis of measurement-device-independent quantum cryptography with continuous variables, Phys. Rev. A 96(4), 042332 (2017)
Y. Liu, T. Y. Chen, L. J. Wang, H. Liang, G. L. Shentu, J. Wang, K. Cui, H. L. Yin, N. L. Liu, L. Li, X. Ma, J. S. Pelc, M. M. Fejer, C. Z. Peng, Q. Zhang, and J. W. Pan, Experimental measurement-device-independent quantum key distribution, Phys. Rev. Lett. 111(13), 130502 (2013)
T. Ferreira da Silva, D. Vitoreti, G. B. Xavier, G. C. do Amaral, G. P. Temporão, and J. P. von der Weid, Proof-of-principle demonstration of measurement-device-independent quantum key distribution using polarization qubits, Phys. Rev. A 88(5), 052303 (2013)
Z. Tang, Z. Liao, F. Xu, B. Qi, L. Qian, and H. K. Lo, Experimental demonstration of polarization encoding measurement-device-independent quantum key distribution, Phys. Rev. Lett. 112(19), 190503 (2014)
H. W. Li, Z. Q. Yin, W. Chen, S. Wang, G. C. Guo, and Z. F. Han, Quantum key distribution based on quantum dimension and independent devices, Phys. Rev. A 89(3), 032302 (2014)
F. Xu, B. Qi, Z. Liao, and H. K. Lo, Long distance measurement-device-independent quantum key distribution with entangled photon sources, Appl. Phys. Lett. 103(6), 061101 (2013)
X. C. Ma, S. H. Sun, M. S. Jiang, M. Gui, and L. M. Liang, Gaussian-modulated coherent-state measurement-device-independent quantum key distribution, Phys. Rev. A 89(4), 042335 (2014)
S. Pirandola, C. Ottaviani, G. Spedalieri, C. Weedbrook, S. L. Braunstein, S. Lloyd, T. Gehring, C. S. Jacobsen, and U. L. Andersen, High-rate measurement-device-independent quantum cryptography, Nat. Photonics 9(6), 397 (2015)
Z. Li, Y. C. Zhang, F. Xu, X. Peng, and H. Guo, Continuous-variable measurement-device-independent quantum key distribution, Phys. Rev. A 89(5), 052301 (2014)
B. Qi, Simultaneous classical communication and quantum key distribution using continuous variables, Phys. Rev. A 94(4), 042340 (2016)
B. Qi and C. C. W. Lim, Noise analysis of simultaneous quantum key distribution and classical communication scheme using a true local oscillator, Phys. Rev. Appl. 9(5), 054008 (2018)
X. Wu, Y. Wang, Q. Liao, H. Zhong, and Y. Guo, Simultaneous classical communication and quantum key distribution based on plug-and-play configuration with an optical amplifier, Entropy 21(4), 333 (2019)
T. Wang, P. Huang, S. Wang, and G. Zeng, Carrierphase estimation for simultaneous quantum key distribution and classical communication using a real local oscillator, Phys. Rev. A 99(2), 022318 (2019)
W. A. Hofer, Solving the Einstein-Podolsky-Rosen puzzle: The origin of non-locality in Aspect-type experiments, Front. Phys. 7(5), 504 (2012)
M. Navascués and A. Acín, Security bounds for continuous variables quantum key distribution, Phys. Rev. Lett. 94(2), 020505 (2005)
S. Pirandola, R. Laurenza, C. Ottaviani, and L. Banchi, Fundamental limits of repeaterless quantum communications, Nat. Commun. 8(1), 15043 (2017)
S. Fossier, E. Diamanti, T. Debuisschert, R. Tualle-Brouri, and P. Grangier, Improvement of continuous-variable quantum key distribution systems by using optical preamplifiers, J. Phys. At. Mol. Opt. Phys. 42(11), 114014 (2009)
X. Zhang, Y. Zhang, Y. Zhao, X. Wang, S. Yu, and H. Guo, Finite-size analysis of continuous-variable measurement-device-independent quantum key distribution, Phys. Rev. A 96(4), 042334 (2017)
C. Lupo, C. Ottaviani, P. Papanastasiou, and S. Pirandola, Parameter estimation with almost no public communication for continuous-variable quantum key distribution, Phys. Rev. Lett. 120(22), 220505 (2018)
Q. Liao, Y. Wang, D. Huang, and Y. Guo, Dualphase-modulated plug-and-play measurement-device-independent continuous-variable quantum key distribution, Opt. Express 26(16), 19907 (2018)
X. Wu, Y. Wang, S. Li, W. Zhang, D. Huang, and Y. Guo, Security analysis of passive measurement-device-independent continuous-variable quantum key distribution with almost no public communication, Quantum Inform. Process. 18(12), 372 (2019)
C. Lupo, C. Ottaviani, P. Papanastasiou, and S. Pirandola, Continuous-variable measurement-device-independent quantum key distribution: Composable security against coherent attacks, Phys. Rev. A 97(5), 052327 (2018)
B. Qi, P. Lougovski, R. Pooser, W. Grice, and M. Bobrek, Generating the local oscillator “locally” in continuous-variable quantum key distribution based on coherent detection, Phys. Rev. X 5(4), 041009 (2015)
D. B. Soh, C. Brif, P. J. Coles, N. Lütkenhaus, R. M. Camacho, J. Urayama, and M. Sarovar, Self-referenced continuous-variable quantum key distribution protocol, Phys. Rev. X 5(4), 041010 (2015)
D. Huang, P. Huang, D. Lin, C. Wang, and G. Zeng, High-speed continuous-variable quantum key distribution without sending a local oscillator, Opt. Lett. 40(16), 3695 (2015)
X. Zhang, Y. Zhang, Z. Li, S. Yu, and H. Guo, IEEE Photonics J. 10, 1 (2018)
G.-P. Sanchez, Universite Libre de Bruxelles, 2007
Acknowledgements
This work was supported by the National Natural Science Foundation of China (Grant No. 61801522) and National Nature Science Foundation of Hunan Province, China (Grant No. 2019JJ40352).
Author information
Authors and Affiliations
Corresponding authors
Rights and permissions
About this article
Cite this article
Wu, XD., Wang, YJ., Huang, D. et al. Simultaneous measurement-device-independent continuous variable quantum key distribution with realistic detector compensation. Front. Phys. 15, 31601 (2020). https://doi.org/10.1007/s11467-020-0954-8
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11467-020-0954-8