Abstract
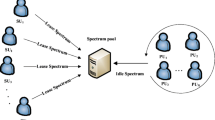
In order to realize efficient data transmission for multiple bounded rationality users sharing multiple channels in radio network, a dynamic spectrum access mechanism based on graphical evolutionary game is proposed to describe user’s dynamic process for distributing transmission rate. The mechanism can reflect the real game relationship among users, thus simplifying the complexity of the game. Meanwhile, a dynamic spectrum access algorithm with smaller complexity and corresponding dynamic equation are designed for the mechanism, converging to Nash equilibrium with faster speed and obtaining higher system throughput. At Nash equilibrium, the reward of individual user is identical on each channel. Theory analyzes and proves that the dynamic equation is globally asymptotically stable, which illustrates that when user deviates because of bounded rationality, it is still able to converge again with faster speed and guarantee better performance with less deviation, and user’s deviation only affects its neighboring users, not spreading to the whole network. Simulation comparison verifies the superiority above.














Similar content being viewed by others
References
Feng, D. Q., Jiang, C. Z., Lim, G., Leonard, J., Cimini, J., Feng, G., et al. (2013). A survey of energy-efficient wireless communications. Communications Surveys & Tutorials, IEEE, 15(1), 167–178.
Han, Z., Niyato, D., Saad, W., Basar, T., & Hjorungnes, A. (2012). Game theory in wireless and communication networks: Theory, models, and applications (pp. 55–251). Cambridge, MA: Cambridge University Press.
Yang, L., Kim, H., Zhang, J. S., Chiang, M., & Tan, C. W. (2013). Pricing-based decentralized spectrum access control in cognitive radio networks. IEEE/ACM Transactions on Networking (TON), 21(2), 522–535.
Wu, G. G., Ren, P. Y., & Du, Q. H. (2012). Dynamic spectrum auction with time optimization in cognitive radio networks. In IEEE vehicular technology conference (VTC Fall) (pp. 1–5).
Li, D. P., Xu, Y. Y., Wang, X. B., & Guizani, M. (2011). Coalitional game theoretic approach for secondary spectrum access in cooperative cognitive radio networks. IEEE Transactions on Wireless Communications, 10(3), 844–856.
Wang, B. B., Wu, Y., Ji, Z., Liu, K. J. R., & Clancy, T. C. (2008). Game theoretical mechanism design methods. Signal Processing Magazine, IEEE, 25(6), 74–84.
Xu, Y. H., Wang, J. L., Wu, Q. H., Anpalagan, A., & Yao, Y. D. (2012). Opportunistic spectrum access in cognitive radio networks: Global optimization using local interaction games. IEEE Journal of Selected Topics in Signal Processing, 6(2), 180–194.
Weibull, J. W. (1997). Evolutionary game theory. Cambridge, MA: MIT Press.
Sandholm, W. H. (2012). Evolutionary game theory. Computational Complexity: Theory, Techniques, And Applications, 1000–1029.
Tomassini, M. (2013). Introduction to evolutionary game theory. In Proceeding of the fifteenth annual conference companion on genetic and evolutionary computation conference companion (pp. 765–778). ACM.
Jiang, C. X., Chen, Yan., Gao, Yang., & Liu, K. J. R. (2013). Joint spectrum sensing and access evolutionary game in cognitive radio networks. IEEE Transactions on Wireless Communications, 12(5), 1–14.
Zhao, S. S., Zhu, Q., & Zhu, H. B. (2012). Evolutionary game theoretical approach to dynamic spectrum sharing. Journal of Computational Information Systems, 8(10), 4225–4232.
Xu, Y. H., Wu, Q. H., Wang, J. L., Shen, L., & Anpalagan, A. (2013). Opportunistic spectrum access using partially overlapping channels: Graphical game and uncoupled learning. IEEE Transactions on Communications, 61(9), 1–13.
Li, H. S., & Han, Z. (2010). Competitive spectrum access in cognitive radio networks: Graphical game and learning. In Wireless communications and networking conference (WCNC) (pp. 1–6). IEEE.
Xu, Y. H., Wu, Q. H., Wang, J. L., & Yao, Y. D. (2012). Social welfare maximization for SRSNs using bio-inspired community cooperation mechanism. Chinese Science Bulletin, 57, 125–131.
Shenker, S. (1995). Fundamental design issues for the future Internet. IEEE Journal of Selected Areas in Communications, 13, 1176–1188.
Sandholm, W. H. (2001). Potential games with continuous player sets. Journal of Economic Theory, 97(1), 81–108.
Neto, J. X. C., Oliveira, P. R., Soares, P. A., Jr, & Soubeyran, A. (2013). Learning how to play Nash, potential games and alternating minimization method for structured nonconvex problems on Riemannian manifolds. Journal of Convex Analysis, 20, 395–438.
Narendra, K. S., & Annaswamy, A. M. (2012). Stable adaptive systems. New York: Courier Dover Publications.
Barth, D., Bournez, O., Boussaton, O., & Cohen, J. (2009). A dynamic approach for load balancing. In Proceedings of the fourth international ICST conference on performance evaluation methodologies and tools. ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering) (p. 60).
Guess, T., Varanasi, M. K., & Member, S. (2003). A comparison of bandwidth-efficient multiple access to other signal designs for correlated waveform multiple-access communications. IEEE Transactions on Information Theory, 49(6), 1558–1564.
Acknowledgments
This work is supported by Foundation Items: The National Natural Science Foundation of China (61102062, 61301122). The Key Project of Chinese Ministry of Education (212145). The Research Project of Chongqing Education Commission (KJ120530, KJ1400405), NSF of Chongqing (cstc2014jcyjA40052), NSF of CQUPT (A2013-30), and the Doctor Science Research Starting Foundation of CQUPT (A2013-23).
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1
1.1 Proof of Theorem 1
Proof
We divide the set of channels M into the following three complete and mutually exclusive subsets according to the size of any two reward existing only three kinds of logical relationship, that is less than, equal to, greater than:
For a channel \( j \in M_{1} , \) the reward of user i on this channel is less than that on other channel, i.e. \( r_{i,j} \left( {x\left( n \right)} \right) < r_{i,k} \left( {x\left( n \right)} \right), \) so user does not continually transmit data on channel j with probability \( p_{j} = 0 \) and transmits on other channel having higher reward with probability \( p_{k} , \) which is given in formula (6):
Thus, the dynamic behavior of users selecting channels is given as:
For a channel \( j \in M_{2} , \) we have \( r_{i,j} \left( {x\left( n \right)} \right) = r_{i,k} \left( {x\left( n \right)} \right) \) and \( p_{j} = 0. \)
Thus \( \Delta x_{i,j} (n) = 0 \) and satisfies formula (7).
For a channel \( j \in M_{3} , \) we have \( r_{i,j} \left( {x\left( n \right)} \right) > r_{i,k} \left( {x\left( n \right)} \right). \) Thus user i continually transmits data on this channel. Since \( p_{j} > 0, \) there will be some other users from the channel \( l \in M_{1} \) to transmit on this channel. Let \( \Theta \) be the fraction of rate ratio of users carrying out the movement from the channel \( l \in M_{1} . \) We have
Since \( r_{i,k} \left( {x\left( n \right)} \right) = r_{i,l} \left( {x\left( n \right)} \right) \) and \( \sum\nolimits_{{l \in M_{2} }} {\left( {r_{i,k} \left( {x\left( n \right)} \right) - r_{i,l} \left( {x\left( n \right)} \right)} \right) = 0} \) for \( l \in M_{2} . \)
We obtain
Then, the increased fraction of rate ratio on channel \( j \in M_{3} \) thus is
which completes the proof. ■
Appendix 2
2.1 Proof of Theorem 2
Proof
We construct a potential function:
where \( B_{i} = \sum\nolimits_{{j \in {\mathcal{M}}}} {r_{i,j} \left( {x_{i,j} \text{,}x_{{J_{ - i} ,j}} } \right)} \) is denoted in formula (4).
Now suppose that arbitrary user i makes a unilateral deviation from \( x_{i,j} \) to \( \tilde{x}_{i,j} , \) the change in its total reward function is represented by:
where \( \tilde{x}_{h,j} \) is rate distribution ratio of its community users after user i unilaterally changes strategy.
The change in the potential function caused by this unilateral change is given by:
where \( \mathcal{N}\backslash J_{i} \) stands for that set \( J_{i} \) is excluded from set \( \mathcal{N}. \)
In graphical game, as the action of user \( i \) only affects the reward of its neighboring users, then the following equation holds:
We conclude from (16), the game is a potential game.
This completes the proof. ■
Appendix 3
3.1 Proof of Theorem 3
Proof
According to [19], we prove the globally asymptotic stability by using the following Lyapunov Function \( V\left( {x\left( n \right)} \right) = L^{ * } - L\left( {x\left( n \right)} \right), \) where \( L\left( {x\left( n \right)} \right) = \sum\nolimits_{j = 1}^{M} {\int_{ - \infty }^{{x_{j} \left( n \right)}} {r_{i,j} } } \left( y \right)dy, \) since \( L^{ * } \) is the unique global maximum of \( L\left( {x\left( n \right)} \right) \) achieved at \( x\left( n \right) = x^{ * } , \) we thus have \( \forall x\left( n \right) \ne x^{ * } ,\,V\left( {x\left( n \right)} \right) > 0,\,V\left( {x^{ * } } \right) = 0. \)
Then differentiating \( V\left( {x\left( n \right)} \right) \) with respective to n, we have
Thus, we obtain \( \forall x\left( n \right) \ne x^{ * } ,\,\tilde{V}\left( {x\left( n \right)} \right) < 0,\,\tilde{V}\left( {x^{ * } } \right) = 0, \) which completes the proof. ■
Rights and permissions
About this article
Cite this article
Li, FW., Yuan, YH., Zhu, J. et al. Dynamic Spectrum Access Mechanism Based on Graphical Evolutionary Game in Radio Network. Wireless Pers Commun 85, 2191–2210 (2015). https://doi.org/10.1007/s11277-015-2899-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2899-8