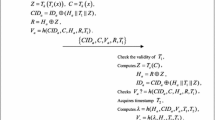
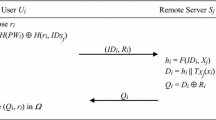
Abstract
When it comes to key agreement protocol, mutual authentication is regarded as a crucial security requirement. Yet, conventional authenticated key agreement using static ID cannot provide user anonymity if the communication content is compromised. A dynamic ID authentication scheme is a better alternative for maintaining user’s privacy. Based on the Chebyshev chaotic map, the author proposes a mobile dynamic ID authenticated key agreement scheme which allows mobile users to gain resources of remote servers. By optimizing the server computation, our scheme aims at increasing the concurrent process capacity of remote servers. We also demonstrate that the proposed scheme is secure against existential active attacks and outperforms related works.
Similar content being viewed by others
References
Awasthi, A. K. (2004). Comment on a dynamic ID-based remote user authentication scheme. Transaction on Cryptology, 1(2), 15–16.
Baptista, M. S. (1998). Cryptography with chaos. Physics Letters A, 240(1–2), 50–54.
Chen, C., He, D., Chan, S., Bu, J., Gao, Y., & Fan, R. (2011). Lightweight and provably secure user authentication with anonymity for the global mobility network. International Journal of Communication Systems, 24(3), 347–362.
Das, M. L., Saxana, A., & Gulati, V. P. (2004). A dynamic ID-based remote user authentication scheme. IEEE Transactions on Consumer Electronics, 50(2), 629–631.
Diffie, W., & Hellman, M. (1976). New directions in cryptography. IEEE Transactions on Information Theory, IT–22(6), 644–654.
Gong, P., Li, P., & Shi, W. B. (2012). A secure chaotic maps-based key agreement protocol without using smart cards. Nonlinear Dynamics, 70(4), 2401–2406.
He, D., Chen, Y., & Chen, J. H. (2012). Cryptanalysis and improvement of an extended chaotic maps-based key agreement protocol. Nonlinear Dynamics, 69(3), 1149–1157.
He, D., Chen, J., & Zhang, R. (2011). A more secure authentication scheme for telecare medicine information systems. Journal of Medical Systems, 36(3), 1989–1995.
Han, S. (2008). Security of a key agreement protocol based on chaotic maps. Chaos, Solitons & Fractals, 38(3), 764–768.
Hwang, M. S., & Li, L. H. (2000). A new remote user authentication scheme using smart cards. IEEE Transactions on Consumer Electron, 46(1), 28–30.
Juang, W. S., & Wu, J. L. (2009). Two efficient two-factor authenticated key exchange protocols in public wireless lans. Computers and Electrical Engineering, 1(35), 33–40.
Khan, M. K., Kim, S. K., & Alghathbar, K. (2011). Cryptanalysis and security enhancement of a more efficient and secure dynamic ID-based remote user authentication scheme. Computer Communications, 34(3), 305–309.
Kocarev, L. (2001). Chaos-based cryptography: a brief overview. IEEE Circuits and Systems Magazine, 1(3), 6–21.
Ku, W. C., & Chang, S. T. (2005). Impersonation attacks on a dynamic ID-based remote user authentication scheme using smart cards. IEICE Transactions on Communications, E88–B(5), 2165–2167.
Lamport, L. (1981). Password authentication with insecure communication. Communications of the ACM, 24(11), 770–772.
Lee, C. C., Chen, C. L., Wu, C. Y., & Huang, S. Y. (2012). An extended chaotic maps-based key agreement protocol with user anonymity. Nonlinear Dynamics, 69(1–2), 79–87.
Lee, C. C., & Hsu, C. W. (2012). A secure biometric-based remote user authentication with key agreement scheme using extended chaotic maps. Nonlinear Dynamics, 71(1–2), 201–211.
Lee, C. C., Li, C. T., & Hsu, C. W. (2013). “A three-party password-based authenticated key exchange protocol with user anonymity using extended chaotic maps”, Nonlinear Dynamics, in press, (doi:10.1007/s11071-013-0772-4).
Liao, I., Lee, C. C., & Hwang, M. S. (2005). “Security enhancement for a dynamic ID-based remote user authentication scheme, Proceedings of 2005 International Conference on Next Generation Web Services Practices, Seoul, Korea, pp. 437–440.
Lin, C. L., Sun, H. M., & Hwang, T. (2001). Attacks and solutions on strong-password authentication. IEICE Transactions on Communications, E84–B(9), 2622–2627.
Misbahuddin, M., & Bindu, C. S. (2008). Cryptanalysis of Liao-Lee-Hwang’s dynamic ID scheme. International Journal of Network Security, 2(6), 211–213.
Niu, Y., & Wang, X. (2011). An anonymous key agreement protocol based on chaotic maps. Communications in Nonlinear Science and Numerical Simulation, 16(4), 1986–1992.
Shimizu, A. (1991). A dynamic password authentication method by one way function. System and Computers in Japan, 22(7), 32–40.
Shimizu, A., Horioka, T., & Inagaki, H. (1998). A password authentication method for contents communication on the Internet. IEICE Transactions on Communications, E81–B(8), 1666–1673.
Su, R., & Cao, Z. F. (2010). An efficient anonymous authentication mechanism for delay tolerant networks. Computers and Electrical Engineering, 3(36), 435–441.
Tang, H. B., & Liu, X. S. (2012). Cryptanalysis of a dynamic ID-based remote user authentication with key agreement scheme. International Journal of Communication Systems, 25(12), 1639–1644.
Tsai, J. L., Wu, T. C., & Tsai, K. Y. (2010). New dynamic ID authentication scheme using smart cards. International Journal of Communication Systems, 23(12), 1449–1462.
Tseng, H., Jan, R., & Yang, W. (2009). “A chaotic maps-based key agreement protocol that preserves user anonymity”, Proceedings of IEEE international Conference on Communications (ICC09), pp. 1–6.
Tan, Z. (2013). A chaotic maps-based authenticated key agreement protocol with strong anonymity. Nonlinear Dynamics, 72(1–2), 311–320.
Wang, R. C., Juang, W. S., & Lei, C. L. (2011). Robust authentication and key agreement scheme preserving the privacy of secret key. Computer Communications, 34(3), 274–280.
Wang, Y. Y., Liu, J. Y., Xiao, F. X., & Dan, J. (2009). A more efficient and secure dynamic ID-based remote user authentication scheme. Computer Communications, 32(4), 583–585.
Wen, F., & Li, X. (2011). An improved dynamic ID-based remote user authentication with key agreement scheme. Computers and Electrical Engineering, 38(2), 381–387.
Wu, S., Zhu, T., & Pu, Q. (2011). Robust smart-cards-based user authentication scheme with user anonymity. Security and Communication Networks, 5(2), 236–248.
Xiao, D., Liao, X., & Deng, S. (2007). A novel key agreement protocol based on chaotic maps. Information Sciences, 177(4), 1136–1142.
Xue, K., & Hong, P. (2012). Security improvement on an anonymous key agreement protocol based on chaotic maps. Communications in Nonlinear Science and Numerical Simulation, 17(7), 2969–2977.
Yoon, E. J., Yoo, K. Y. (2006). “Improving the dynamic ID-based remote mutual authentication scheme”, Proceedings of 2006 OTM Workshops, Lecture Notes in Computer Science, Vol. 4277, Springer, Berlin, pp. 499–507.
Yoon, E. J., Yoo, K. Y., & Ha, K. S. (2011). A user friendly authentication scheme with anonymity for wireless communications. Computers and Electrical Engineering, 3(37), 356–364.
Acknowledgments
The author would like to thank anonymous referees for their valuable suggestions. This work was supported in part by the National Science Council of Republic of China under the contract number NSC 102-2221-E-019-041.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Lin, HY. Chaotic Map Based Mobile Dynamic ID Authenticated Key Agreement Scheme. Wireless Pers Commun 78, 1487–1494 (2014). https://doi.org/10.1007/s11277-014-1829-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-014-1829-5