Abstract
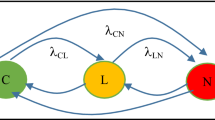
This paper presents the quantitative network survivability analysis for a power-aware mobile ad hoc network (MANET) based on Markov regenerative processes (MRGPs). The MRGP is one of the widest classes of stochastic point process which are mathematically tractable. In the past literature, the model for a power-aware MANET was described by a continuous-time Markov chain (CTMC). However, in the sense of representation ability, CTMC modeling is not sufficient to analyze the relationship between battery state and node behavior in the power-aware MANET. In particular, such problem seriously arises when we treat the transient behavior of the power-aware MANET. In the paper, we revisit a power-aware MANET model by using MRGP, and present both stationary and transient analyses for the MRGP-based model.














Similar content being viewed by others
Explore related subjects
Discover the latest articles and news from researchers in related subjects, suggested using machine learning.References
Aad, I., Hubaux, J. P., & Knightly, E. W. (2004). Denial of service resilience in ad hoc networks. In Proceedings of the 10th annual international conference on mobile computing and networking (pp. 202–215). ACM.
Asmussen, S., Nerman, O., & Olsson, M. (1996). Fitting phase-type distributions via the EM algorithm. Scandinavian Journal of Statistics, 23(4), 419–441.
Baum, L. E., Petrie, T., Soules, G., & Weiss, N. (1970). A maximization technique occurring in the statistical analysis of probabilistic function of Markov chains. Annals of Mathematical Statistics, 41(1), 164–171.
Bettstetter, C. (2002). On the minimum node degree and connectivity of a wireless multihop network. In Proceedings of ACM international symposium on mobile ad hoc networking and computing (MobiHoc-2002) (pp. 80–91). ACM.
Bettstetter, C., Klinglmayr, J., & Lettner, S. (2010). On the degree distribution of k-connected random networks. In Proceedings of IEEE conference on communications (ICC-2010) (pp. 1–6). IEEE CSP.
Bobbio, A., & Cumani, A. (1992). ML estimation of the parameters of a PH distribution in triangular canonical form. In G. Balbo & G. Serazzi (Eds.), Computer performance evaluation (pp. 33–46). Elsevier Science Publishers.
Bolch, G., Greiner, S., de Meer, H., & Trivedi, K. S. (2006). Queueing networks and Markov chains: Modeling and performance evaluation with computer science applications (2nd ed.). New York: Wiley.
Chen, D., Garg, S., & Trivedi, K. S. (2002). Network survivability performance evaluation: A quantitative approach with applications in wireless ad-hoc networks. In Proceedings of ACM international conference on modeling analysis and simulation of wireless and mobile systems (MSWiM-2002) (pp. 61–68). ACM.
Choi, H., Kulkarni, V. G., & Trivedi, K. S. (1994). Markov regenerative stochastic Petri nets. Performance Evaluation, 20, 337–357.
Çinlar, E. (1969). Markov renewal theory. Advances in Applied Probability, 1, 123–187.
Cloth, L., Haverkort, B. R., & Jongerden, M.R. (2007). Computing battery lifetime distributions. In Proceedings of the 37th annual IEEE/IFIP international conference on dependable systems and networks (pp. 780–789). IEEE CS Press.
Cumani, A. (1982). On the canonical representation of homogeneous Markov processes modelling failure-time distributions. Microelectronics Reliability, 22, 583–602.
Dahl, G. (1993). The design of survivable directed networks. Telecommunication Systems, 2, 349–377.
Deng, L., & Mark, J. (1993). Parameter estimation for Markov modulated Poisson processes via the EM algorithm with time discretization. Telecommunication Systems, 1, 321–338.
Ellison, R., Fisher, D., Linger, R., Lipson, H., Longstaff, T., & Mead, N. (1997). Survival network systems: An emerging discipline. Tech. Rep. CMU/SEI-97-TR-013, SEI/CMU.
Fricks, R., Telek, M., Puliafito, A., & Trivedi, K. S. (1998). Markov renewal theory applied to performability evaluation. In K. Bagchi & G. Zobrist (Eds.), State-of-the art in performance modeling and simulation. Modeling and simulation of advanced computer systems: Applications and systems (pp. 193–236). Newark, NJ: Gordon and Breach Publishers.
Gupta, V., Krishnamurthy, S., & Faloutsos, M. (2002). Denial of service attacks at the MAC layer in wireless ad hoc networks. In Proceedings of IEEE conference on military communications (pp. 1118–1123). IEEE CSP.
Knight, J. C., & Sullivan, K. J. (2000). On the definition of survivability. Tech. Rep. CS-TR-33-00, Dept. of Computer Science, University of Virginia.
Okamura, H., Dohi, T., & Trivedi, K. S. (2011). A refined EM algorithm for PH distributions. Performance Evaluation, 68(10), 938–954.
Okamura, H., Kishikawa, H., Dohi, T. (2013). Application of deterministic annealing EM algorithm to MAP/PH parameter estimation. Telecommunication Systems, 54(1), 79–90.
Reibman, A., & Trivedi, K. S. (1989). Transient analysis of cumulative measures of Markov model behavior. Stochastic Models, 5(4), 683–710.
Reibman, A. L., & Trivedi, K. S. (1988). Numerical transient analysis of Markov models. Computers Operations Research, 15, 19–36.
Rosenberg, E. (2002). Capacity requirements for node and arc survivable networks. Telecommunication Systems, 20(1,2), 107–131.
Soni, S., & Prikul, H. (2002). Design of survivable networks with connectivity requirements. Telecommunication Systems, 20, 133–149.
Takahasi, H., & Mori, M. (1974). Double exponential formulas for numerical integration. Publ. RIMS, Kyoto Univ. (Vol. 9, pp. 721–741).
Telek, M., Bobbio, A., Jereb, L., Puliafito, A., & Trivedi, K. S. (1995). Steady state analysis of Markov regenerative SPN with age memory policy. In Quantitative evaluation of computing and communication systems (LNCS 977) (pp. 165–179). Springer.
Telek, M., & Horváth, A. (2001). Transient analysis of age-MRSPNs by the method of supplementary variables. Performance Evaluation, 45, 205–221.
Thümmler, A., Buchholz, P., & Telek, M. (2006). A novel approach for phase-type fitting with the EM algorithm. IEEE Transactions on Dependable and Secure Computing, 3(3), 245–258.
Xing, F., & Wang, W. (2006). Modeling and analysis of connectivity in mobile ad hoc networks with misbehaving nodes. In Proceedings of IEEE conference on communications (ICC-2006) (pp. 1879–1884). IEEE CSP.
Xing, F., & Wang, W. (2010). On the survivability of wireless ad hoc networks with node misbehaviors and failures. IEEE Transactions on Dependable and Secure Computing, 7(3), 284–299.
Yi, Z., & Dohi, T. (2011). Quantitative comparison of survivability models for wireless ad hoc networks. In Proceedings of 2nd international conference on networking and computing (ICNC-2011) (pp. 284–287). IEEE CSP.
Yi, Z., & Dohi, T. (2012). Survivability analysis for a wireless ad hoc network based on semi-Markov model. IEICE Transactions on Information & Systems, E95-D(12), 2844–2851.
Yi, Z., Dohi, T., & Okamura, H. (2012). Survivability modeling and analysis for a power-aware wireless ad hoc network. In Proceedings of 4th international workshop on reliable networks design and modeling (RNDM 2012). IEEE CSP.
Yoshihara, T., Kasahara, S., & Takahashi, Y. (2001). Practical time-scale fitting of self-similar traffic with Markov modulated Poisson process. Telecommunication Systems, 17(1–2), 185–211.
Acknowledgments
This research was partially supported by the Ministry of Education, Science, Sports and Culture, Grant-in-Aid for Scientific Research (C), Grant No. 21510167 (2009–2011).
Author information
Authors and Affiliations
Corresponding author
Appendices
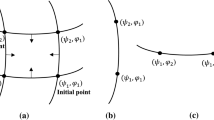
A Uniformization
The uniformization approach is effective to compute the matrix exponential in the Markov analysis [21, 22]. Let \(\gamma _{F,L}(v)\) and \(\gamma _{L,F}(v)\) be the p.m.f.’s of mixed Poisson distribution with mixture probabilities \(F_{F,L}(t)\) and \(F_{L,F}(t)\), respectively:
where \(q_F\) and \(q_L\) are maximum values of absolute diagonal elements of \(\varvec{Q}_F\) and \(\varvec{Q}_L\). Using the p.m.f.’s, the matrix exponential form can be rewritten by
The infinite sums may be truncated by left truncation point \(L\) and right truncation point \(R\) such that
where \(\epsilon \) is a tolerance error.
B Computation of Weights
This paper utilizes the method to generate the weighted samples based on the double exponential (DE) formula [25]. This approach provides more accurate approximation to many types of integral functions, compared to trapezoidal rule, Simpson’s rule, etc. The DE formula changes the original integration to an infinite integration of the function which decays according to double exponential function. Here we use the following function
By substituting the above function to \(\int _0^\infty f(t) \log g(t)dt\), the integration is transformed to
where \(\phi '(x)\) is the first derivative of \(\phi (x)\). Applying the trapezoidal rule to the above integration, we have
where \(h\) is a step size and \(K^+ (= -K^-)\) is a upper (lower) limit of discretization points. In fact, the accuracy of integration can be controlled by the parameters \(h\) and \(K^+\). That is, given \(h\) and \(K^+\), we generate the weighted samples \((t_1, w_1), \ldots , (t_K, w_K)\) as follows
where \(K = K^+ - K^- + 1\).
Rights and permissions
About this article
Cite this article
Okamura, H., Yi, Z. & Dohi, T. Network survivability modeling and analysis for power-aware MANETs by Markov regenerative processes. Telecommun Syst 60, 471–484 (2015). https://doi.org/10.1007/s11235-015-9989-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-015-9989-5