Abstract
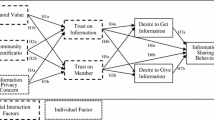
Although social networking services (SNS) are among the most important means of sharing and communication in today’s virtual world, little work has been done to explain the personal information-sharing behavior of SNS users in detail. This study tries to investigate the dimensions of personal information-sharing behavior of SNS users and to find important factors affecting their sharing behavior. In terms of the width and depth of sharing personal information, we distinguish two important dimensions of personal information-sharing behavior—i.e., sharing regularity and sharing density. As a width dimension of sharing behavior, sharing regularity refers to the frequency of sharing personal information with other SNS users, and as a depth dimension of sharing behavior, sharing density deals with the degree of personal information sharing with others. Using a theoretical lens from the Theory of Reasoned Action (TRA), we propose a research model of the two dimensions of personal information-sharing behavior, which also includes attitude toward sharing, social trust, and trust in a social networking service. The study finds that social trust and trust in the SNS have a significant effect on SNS users’ attitude toward sharing, which in turn strongly influences the two dimensions of personal information-sharing behavior. The implications of the study for research and practice will be discussed with future directions.



Similar content being viewed by others
References
Abdul-Rahman A, Hailes S (2000) Supporting trust in virtual communities. In: Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, 2000, vol 1, p 9. IEEE
Ardichvili A, Page V, Wentling T (2003) Motivation and barriers to participation in virtual knowledge-sharing communities of practice. J Knowl Manag 7(1):64–77
Barnes SB (2006) A privacy paradox: social networking in the United States. First Monday 11(9):11–15
Basso A, Goldberg D, Greenspan S, Weimer D (2001) First Impressions: Emotional and Cognitive Factors Underlying Judgments of Trust E-commerce. Paper Presented at the Proceedings of the 3rd ACM Conference on Electronic Commerce, Tampa, Florida, USA
Bentler PM, Speckart G (1979) Models of attitude-behavior relations. Psychol Rev 86(5):452–464
Berners-Lee T, Hall W, Hendler JA, O’Hara K, Shadbolt N, Weitzner DJ (2006) A framework for web science. Found Trends Web Sci 1(1):1–130
Bock G-W, Zmud R, Kim Y-G, Lee J-N (2005) Behavioral intention formation in knowledge sharing: examining the roles of extrinsic motivators, social-psychological forces, and organizational climate. MIS Q 29(1):87–111
Bollen KA (1989) Structural Equations with Latent Variables. Wiley, New York
Boyd DM, Ellison NB (2007) Social network sites: definition, history, and scholarship. J Comput Mediat Commun 13(1):210–230
Boyd J (2003) The rhetorical construction of trust online. Commun Theory 13(4):392–410
Brown J, Broderick AJ, Lee N (2007) Word of mouth communication within online communities: conceptualizing the online social network. J Interact Mark 21(3):2–20
Byrne BM (2001) Structural Equation Modeling with AMOS: Basic Concepts, Applications, and Programming. Lawrence Erlbaum Associates, Publishers, Mahwah
Canzaroli A, Tan Y, Thoen W (1999) The social and institutional context of trust in e-commerce. In: Proceedings of Autonomous Agents, 1999 Workshop on Deception, Fraud and Trust in Agent Societies, pp 65–66
Castelfranchi C, Pedone R (1999) A review on Trust in Information Technology. National Research Council-Institute of Psychology, Rome
Chai S, Kim M (2011) A socio-technical approach to knowledge contribution behavior: an empirical investigation of social networking sites users. Int J Inf Manag 32(2):118–126
Chang YP, Zhu DH (2011) Understanding social networking sites adoption in China: a comparison of pre-adoption and post-adoption. Comput Hum Behav 27(5):1840–1848
Cheung CMK, Chiu P-Y, Lee MKO (2011) Online social networks: why do students use FaceBook? Comput Hum Behav 27(4):1337–1343
Chin WW (1995) Partial least squares is to LISREL as principal components analysis is to common factor analysis. Technol Stud 2(2):315–319
Chin WW (1998) Commentary: issues and opinion on structural equation modeling. MIS Q 22(1):vii–xvi
Chin WW (1998b) The partial least squares approach for structural equation modeling. In: Marcoulides GA (ed) Modern Methods for Business Research. Lawrence Erlbaum Associates, Mahwah, pp 295–336
Chow WS, Chan LS (2008) Social network, social trust and shared goals in organizational knowledge sharing. Inf Manag 45(7):458–465
Coleman J (1990) Systems of Trust and Their Dynamic Properties. Foundations of Social Theory. JS Coleman. Harvard University Press, Cambridge
Coppola NW, Hiltz SR, Rotter NG (2004) Building trust in virtual teams. IEEE Trans Prof Commun 47(2):95–104
Corbitt BJ, Thanasankit T, Yi H (2003) Trust and e-commerce: a study of consumer perceptions. Electron Commer Res Appl 2(3):203–215
Cropanzano R, Mitchell MS (2005) Social exchange theory: an interdisciplinary review. J Manag 31(6):874–900
Dasgupta P (2000) Trust as a commodity. In: Trust: making and breaking cooperative relations, vol 4. University of Oxford, Department of Sociology, pp 49–72
Delhey J, Newton K (2005) Predicting cross-national levels of social trust: global pattern or nordic exceptionalism? Eur Sociol Rev 21(4):311–327
DiMicco J, Millen DR, Geyer W, Dugan C, Brownholtz B, Muller M (2008) Motivations for social networking at work. Paper presented at the Proceedings of the 2008 ACM Conference on Computer Supported Cooperative Work, San Diego, CA, USA
Dirks KT, Ferrin DL (2001) The role of trust in organizational settings. Organ Sci 12(4):450–467
Doney PM, Cannon JP (1997) An examination of the nature of trust in buyer–seller relationships. J Mark 61(2):35–51
Dwyer C, Hiltz S, Passerini K (2007) Trust and privacy concern within social networking sites: a comparison of Facebook and MySpace. In: AMCIS 2007 Proceedings, 339
Ebizmba.com (2012) Top 15 most popular social networking sites. http://www.ebizmba.com/articles/social-networking-websites. Accessed 27 Jan 2012
Ellison NB (2007) Social network sites: definition, history, and scholarship. J Comput Mediat Commun 13(1):210–230
Ellison NB, Steinfield C, Lampe C (2007) The benefits of Facebook “Friends:” social capital and college students’ use of online social network sites. J Comput Mediat Commun 12(4):1143–1168
Ferrin DL, Kim PH, Cooper CD, Dirks KT (2007) Silence speaks volumes: the effectiveness of reticence in comparison to apology and denial for responding to integrity-and competence-based trust violations. J Appl Psychol 92(4):893
Fishbein M (1979) A theory of reasoned action: some applications and implications. Neb Symp Motiv 27:65–116
Fishbein M, Ajzen I (1975) Belief, Attitude, Intention, and Behavior: An Introduction to Theory and Research. Addison-Wesley Pub. Co., Reading
Fogel J, Nehmad E (2009) Internet social network communities: risk taking, trust, and privacy concerns. Comput Hum Behav 25(1):153–160
Fornell C, Larcker DF (1981) Evaluating structural equation models with unobservable variables and measurement error. J Mark Res 18(1):39–50
Gambetta D (ed) (1988) Trust: making and breaking cooperative relations. England: Basil Blackwell, Oxford
Gefen D (2000) E-commerce: the role of familiarity and trust. Omega 28(6):725–737
Gefen D, Karahanna E, Straub DW (2003) Trust and TAM in online shopping: an integrated model. MIS Q 27(1):51–90
Gefen D, Straub D (2005) A practical guide to factorial validity using PLS-graph: tutorial and annotated example. Commun Assoc Inf Syst 16(1):91–109
Gefen D, Straub DW (2004) Consumer trust in B2C e-Commerce and the importance of social presence: experiments in e-Products and e-Services. Omega 32(6):407–424
Golbeck J, Hendler J (2006) Inferring binary trust relationships in web-based social networks. ACM Trans Internet Technol (TOIT) 6(4):497–529
Goodwin NR (1996) Economic Meanings of Trust and Responsibility. The University of Michigan Press, Ann Arbor
Gordon ME, Slade LA, Schmitt N (1986) The ‘science of the sophomore’ revisited: from conjecture to empiricism. Acad Manag Rev 11(1):191–207
Grace-Farfaglia P, Dekkers A, Sundararajan B, Peters L, Park S-H (2006) Multinational web uses and gratifications: measuring the social impact of online community participation across national boundaries. Electron Commer Res 6(1):75–101
Hanafizadeh P, Khedmatgozar HR (2012) The mediating role of the dimensions of the perceived risk in the effect of customers’ awareness on the adoption of Internet banking in Iran. Electron Commer Res 12(2):151–175
Hardin R (2004) Trust and Trustworthiness. Russell Sage Foundation Publications, Thousand Oaks
Harman HH (1967) Modern Factor Analysis. University of Chicago Press, Chicago
Harrison McKnight D, Choudhury V, Kacmar C (2002) The impact of initial consumer trust on intentions to transact with a web site: a trust building model. J Strateg Inf Syst 11(3–4):297–323
Hollis M (1998) Trust within reason. Cambridge University Press, Cambridge
Hosmer LT (1995) Trust: the connecting link between organizational theory and philosophical ethics. Acad Manag Rev 20(2):379–403
Hsieh J-K, Hsieh Y-C, Tang Y-C (2012) Exploring the disseminating behaviors of eWOM marketing: persuasion in online video. Electron Commer Res 12(2):201–224
Hulland J (1999) Use of partial least squares (PLS) in strategic management research: a review of four recent studies. Strateg Manag J 20(2):195–204
Jeffries FL, Reed R (2000) Trust and adaptation in relational contracting. Acad Manag Rev 25(4):873–882
Jones K (1996) Trust as an affective attitude. Ethics 107(1):4–25
Kim DJ (2008) Self-perception-based versus transference-based trust determinants in computer-mediated transactions: a cross-cultural comparison study. J Manag Inf Syst 24(4):13–45
Kim DJ, Ferrin DL, Rao HR (2008) A trust-based consumer decision-making model in electronic commerce: the role of trust, perceived risk, and their antecedents. Decis Support Syst 44(2):544–564
Kim DJ, Steinfield C, Lai Y-J (2008) Revisiting the role of web assurance seals in business-to-consumer electronic commerce. Decis Support Syst 44(4):1000–1015
Kui M, Yue W, Xu Z, Xiaochun X, Gengdu Z (2005) A trust management model for virtual communities. In: The Fifth International Conference on Computer and Information Technology, 2005. CIT. IEEE, pp 741–745
Lewis K, Kaufman J, Christakis N (2008) The taste for privacy: an analysis of college student privacy settings in an online social network. J Comput Mediat Commun 14(1):79–100
Li F, Pieńkowski D, Van Moorsel A, Smith C (2012) A holistic framework for trust in online transactions. Int J Manag Rev 14(1):85–103
Liang H, Saraf N, Hu Q, Xue Y (2007) Assimilation of enterprise systems: the effect of institutional pressures and the mediating role of top management. MIS Q 31(1):59–87
Liker JK, Sindi AA (1997) User acceptance of expert systems: a test of the theory of reasoned action. J Eng Technol Manag 14(2):147–173
Marsh S (1994) Trust in distributed artificial intelligence. In: Artificial social systems. Springer, Berlin, pp 94–112
Mayer RC, Davis JH, Schoorman FD (1995) An integrative model of organizational trust. Acad Manag Rev 20(3):709–734
McAllister DJ (1995) Affect-and cognition-based trust as foundations for interpersonal cooperation in organizations. Acad Manag J 38(1):24–59
McKnight DH, Chervany NL (2001) Conceptualizing trust: a typology and e-commerce customer relationships model. In: Proceedings of the 34th Annual Hawaii International Conference on System Sciences, 2001. IEEE, p 10
McKnight DH, Choudhury V, Kacmar C (2002) Developing and validating trust measures for e-commerce: an integrative typology. Inf Syst Res 13(3):334–359
Metzger MJ (2004) Privacy, trust, and disclosure: exploring barriers to electronic commerce. J Comput Mediat Commun 9(4)
Mykytyn PPJ, Harrison DA (1993) The application of the theory of reasoned action to senior management and strategic information systems. Inf Resour Manag J 6(2):12
Naughton J (2012) US elections 2012: is Facebook ‘the real presidential swing state’? http://www.theguardian.com/technology/2012/sep/02/impact-internet-us-presidential-elections. Accessed 10/07/2012
Nissenbaum H (1999) Can trust be secured online? A theoretical perspective. Etica Politica 1(2):1–15
Olson JS, Olson GM (2000) i2i trust in e-commerce. Commun ACM 43(12):41–44
Oxford English, D. privacy, adj.1, adv., and n. http://www.oxforddictionaries.com/us/definition/american_english/privacy. Accessed 22/06/2016
Panteli N, Sockalingam S (2005) Trust and conflict within virtual inter-organizational alliances: a framework for facilitating knowledge sharing. Decis Support Syst 39(4):599–617
Pavlou PA (2003) Consumer acceptance of electronic commerce: integrating trust and risk with the technology acceptance model. Int J Electron Commer 7(3):101–134
Pavlou PA, Liang H, Xue Y (2007) Understanding and mitigating uncertainty in online exchange relationships: a principal-agent perspective. MIS Q 31(1):105–136
Resnick P, Kuwabara K, Zeckhauser R, Friedman E (2000) Reputation systems. Commun ACM 43(12):45–48
Ridings CM, Gefen D (2004) Virtual community attraction: why people hang out online. J Comput Mediat Commun 10(1)
Ringle C, Wende S, Will A (2005) Smart PLS 2.0 M3. University of Hamburg, Hamburg
Rubin AD, Geer DE Jr (1998) A survey of Web security. Computer 31(9):34–41
Salehan M, Mousavizadeh Kashipaz SM, Xu C (2013) Information sharing on social networking websites: antecedents and consequences of trust. In: Americas Conference on Information Systems (AMCIS), Chicago, IL
Salehan M, Negahban A (2013) Social networking on smartphones: when mobile phones become addictive. Comput Hum Behav 29(6):2632–2639
Salisbury WD, Rodney AP, Allison WP, David WM (2001) Perceived security and World Wide Web purchase intention. Ind Manag Data Syst 101(4):165–177
Schoenbachler DD, Gordon GL (2002) Trust and customer willingness to provide information in database-driven relationship marketing. J Interact Mark 16(3):2–16
Schriesheim CA (1979) The similarity of individual directed and group directed leader behavior descriptions. Acad Manag J 22(2):345–355
Shin D-H (2010) The effects of trust, security and privacy in social networking: a security-based approach to understand the pattern of adoption. Interact Comput 22(5):428–438
Six F, Nooteboom B, Hoogendoorn A (2010) Actions that build interpersonal trust: a relational signalling perspective. Rev Soc Econ 68(3):285–315
Sledgianowski D, Kulviwat S (2009) Using social network sites: the effects of playfulness, critical mass and trust in a hedonic context. J Comput Inf Syst 49(4):10
Smith JB (1997) Selling alliances: issues and insights. Ind Mark Manag 26(2):149–161
Snijders C (1996) Trust and Commitments, vol 33. Purdue University Press, West Lafayette
Sotiriadis MD, van Zyl C (2013) Electronic word-of-mouth and online reviews in tourism services: the use of twitter by tourists. Electron Commer Res 13(1):1–22
Steinfield C, Ellison NB, Lampe C (2008) Social capital, self-esteem, and use of online social network sites: a longitudinal analysis. J Appl Dev Psychol 29(6):434–445
Suh B, Han I (2003) The impact of customer trust and perception of security control on the acceptance of electronic commerce. Int J Electron Commer 7(3):135–161
Tufekci Z (2008) Can you see me now? Audience and disclosure regulation in online social network sites. Bull Sci Technol Soc 28(1):20–36
Urban GL, Sultan F, Qualls WJ (2000) Placing trust at the center of your internet strategy. Sloan Manag Rev 42(1):39–48
Valenzuela S, Park N, Kee KF (2009) Is There Social Capital in a Social Network Site?: Facebook use and college students’ life satisfaction, trust, and participation. J Comput Mediat Commun 14(4):875–901
Wixom BH, Watson HJ (2001) An empirical investigation of the factors affecting data warehousing success. MIS Q 25(1):17–32
Wu I-L (2003) Understanding senior management behavior in promoting the strategic role of IT in process reengineering: use of the theory of reasoned action. Inf Manag 41(1):1–11
Xu C, Ryan S, Prybutok V, Wen C (2012) It is not for fun: an examination of social network site usage. Inf Manag 49(5):210–217
Xu F, Michael K, Chen X (2013) Factors affecting privacy disclosure on social network sites: an integrated model. Electron Commer Res 13(2):151–168
Young AL, Quan-Haase A (2009) Information revelation and internet privacy concerns on social network sites: a case study of FaceBook. Paper presented at the Proceedings of the Fourth International Conference on Communities and Technologies, University Park, PA, USA
Author information
Authors and Affiliations
Corresponding author
Appendix: Measurement instrument
Appendix: Measurement instrument
ATS1\(^{\mathrm{a}}\) | Sharing stuff (pictures, videos, opinions) with other SNS members is good |
ATS2 | Sharing stuff (pictures, videos, opinions) with other SNS members is important |
ATS3\(^{\mathrm{a}}\) | Sharing stuff (pictures, videos, opinions) with other SNS members is an enjoyable experience |
ATS4 | Sharing stuff (pictures, videos, opinions) with other SNS members is valuable |
ATS5 | Sharing stuff (pictures, videos, opinions) with other SNS members is a wise move |
SD1 | I have my personal information (such as real name, email, cell phone number, photo, current town, sexual orientation) on my SNS |
SD2 | I have shared stuff (pictures, videos, opinions) with my friends, family, and colleagues through my SNS |
SD3 | I have shared my ideas, opinions, and recommendations through my SNS |
SN1 | My family thinks that I should share stuff (pictures, etc.) on my SNS |
SN2\(^{\mathrm{a}}\) | My close friends think that I should share stuff (pictures, etc.) on my SNS |
SN3 | My classmates or colleagues think I should share stuff (pictures, etc.) on my SNS |
SN4\(^{\mathrm{a}}\) | In general, I try to follow my family’s expectations |
SN5 | In general, I accept and carry out my friends’ expectations |
SN6 | In general, I respect and put in practice my classmates’ and colleagues’ expectations |
ST1 | In general, people can be trusted |
ST2\(^{\mathrm{a}}\), \(^{\mathrm{b}}\) | I think that people try to take advantage of me if they get the chance |
ST3 | People try to be fair |
ST4 | People try to be helpful |
ST5\(^{\mathrm{a}}\), \(^{\mathrm{b}}\) | People are just looking out for themselves |
ST6\(^{\mathrm{a}}\) | In general, my SNS friends can be trusted |
ST7\(^{\mathrm{a}}\), \(^{\mathrm{b}}\) | My SNS friends would try to take advantage of me if they got the chance |
ST8 | My SNS friends try to be fair |
ST9\(^{\mathrm{a}}\) | My SNS friends try to be helpful |
ST10\(^{\mathrm{a}}\), \(^{\mathrm{b}}\) | My SNS friends are just looking out for themselves |
TS1 | My SNS is a trustworthy social network |
TS2 | I can count on my SNS to protect my privacy |
TS3 | I can count on my SNS to protect my personal information from unauthorized use |
TS4 | My SNS can be relied on to keep its promises |
SR1 | How often do you login to your SNS? |
SR2 | How often do you share stuff (pictures, videos, opinions)? |
SR3\(^{\mathrm{a}}\) | On average, how much time do you spend on each visit? |
Rights and permissions
About this article
Cite this article
Salehan, M., Kim, D.J. & Koo, C. A study of the effect of social trust, trust in social networking services, and sharing attitude, on two dimensions of personal information sharing behavior. J Supercomput 74, 3596–3619 (2018). https://doi.org/10.1007/s11227-016-1790-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-016-1790-z