Abstract
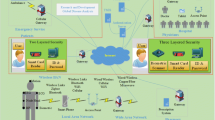
For Multimedia Medical Information System (MMIS), security and privacy are the significant measures. For the guarantee of MMIS significant measures, several authentication schemes have been proposed, though the authentication schemes fail to offer the measurable features, like Repetitive Registration, Verification Table, Mutual Authenticity with Key-Sharing, and Client Anonymity. In addition, the existing authentication schemes fail to provide the reasonable bandwidth utilization and signal congestion to improve the performance of the multimedia information system. Most importantly, the existing schemes fail to withstand against the attacks, like key-impersonation, man-in-the-middle, stolen-verifier and server-spoofing. In this research article, we thus propose and present an efficient Mutual Authentication Scheme (MAS) using bilinear-pairing system to enhance the security features of multimedia information system and it is specially designed and developed for purpose of telecare medicine system. To prove the significance of MAS protocol, this paper is analyzed experimentally the security features comparison, computational cost, execution efficiencies, signal congestion and bandwidth utilization using multimedia medical information system. The examination result is proven that the proposed protocol of MAS achieves better performance comparatively than the existing authentication schemes, such as Wang et al., Chen et al., Choi et al., Wu et al. and Yoon et al.



Similar content being viewed by others
References
Burrows M, Abadi M, Needham R (1990) A logic of authentication. ACM Trans Comput Syst 8:18–36
Chang X, Yang Y, Hauptmann AG, Xing EP, Yu Y-L(2015) Semantic concept discovery for large-scale zero-shot event detection. In: 2015 Twenty-Fourth International Joint Conference on Artificial Intelligence (IJCAI) p 2234–2240
Chang X, Yang Y, Xing E, Yu Y (2015) Complex event detection using semantic saliency and nearly-isotonic SVM. In: 2015 International Conference on Machine Learning (ICML) p 1348–1357
Chang X, Yu Y-L, Yang Y (2015) Searching persuasively: joint event detection and evidence recounting with limited supervision. In: 23rd ACM international conference on multimedia p 581–590
Chen L, Cheng Z, Smart NP (2007) Identity-based key agreement protocols from pairings. Int J Inf Secur 6:213–241
Choi KY, Hwang JY, Lee DH, Seo IS (2005) ID-based authenticated key agreement for low-power mobile devices. Proc. ACISP’05 494–505
Diffie W, Hellman M (1976) New directions in cryptology. IEEE Trans Inf Theory 22(6):644–654
ElGamal T (1985) A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans Inf Theory 31:469–472
Fang G, Huang G (2006) Improvement of recently proposed remote client authentication protocols, in http://eprint.iacr.org/2006/200
Galbraith S, Paterson K, Smart NP (2008) Pairings for cryptographers. Discret Appl Math 156:3113–3121
Hao X, Wang J, Yang Q, Yan X, Li P (2013) A chaotic map-based authentication scheme for telecare medicine information systems. J Med Syst 37(2):1–7
He D, Chen J, Hu J An ID-based client authentication with key agreement protocol for mobile Medical Information environment on ECC with provable security. Inform Fusion 13(3): 223–230
He DB, Chen JH, Zhang R (2011) A more secure authentication scheme for telecare medicine information systems. J Med Syst 36(3):1989–1995
He D, Hu H (2013) Cryptanalysis of a dynamic ID-based remote user authentication scheme with access control for multi-server environment. IEICE Trans Inf Syst E96-D(1):138–140
He D, Wang D, Wu S (2013) Cryptanalysis and improvement of a password-based remote user authentication scheme without smart cards. Inf Technol Control 42(2):170–177
Jakobsson M, Pointcheval D (2001) Mutual authentication for low-power mobile devices. Proc. FC’01 178–195
Jiang Q, Ma J, Ma Z, Li G (2013) A privacy enhanced authentication scheme for telecare medical information systems. J Med Syst 37(1):9897
Jiang P, Wen Q, Li W, Jin Z, Zhang H (2013) An anonymous user authentication with key agreement scheme without pairings for multiserver architecture using SCPKs. Sci World J 2013:8
Kumar P, Lee S, Lee H (2012) E-SAP: efficient-strong authentication protocol for healthcare applications using wireless medical sensor networks. Sensors 12:1625–1647
Lambrinoudakis C, Gritzalis S (2000) Managing medical and insurance information through a smart-card-based information system. J Med Syst 24(4):213–234
Lee WB, Lee CD (2008) A cryptographic key management solution for HIPAA privacy/security regulations. IEEE Trans Inf Technol Biomed 12(1):34–41
Liao E, Lee CC, Hwang MS (2006) A password authentication scheme over insecure networks. J Comput Syst Sci 72(4):727–740
Liu JY, Zhou AM, Gao MX (2008) A new mutual authentication scheme based on nonce and smart cards. Comput Commun 31(10):2205–2209
Ma Z, Yang Y, Xu Z, Sebe N, Yan S, Hauptmann A (2015) Event oriented dictionary learning for complex event detection. IEEE Trans Image Process 24(6):1867–1878
Mitsunari S, Sakai R, Kasahara M (2002) A new traitor tracing. IEICE Trans E85-A(2):481–484
Nam J, Lee J, Kim S, Won D (2005) DDH-based group key agreement in a mobile environment. J Syst Softw 78:73–83
Nie L, Akbari M, Li T, Chua T-S (2014) A joint local–global approach for medical terminology assignment. In: 2014 ACM SIGIR Conference p 24–27
Nie L, Li T, Akbari M, Shen J, Chua T-S (2014) WenZher: comprehensive vertical search for healthcare domain. In: 7th international ACM SIGIR conference on Research & development in information retrieval p 1245–1246
Nie L, Wang M, Zhang L, Yan S, Zhang B, Chua T-S (2014) Disease inference from health-related questions via sparse deep learning. IEEE Trans Knowl Data Eng 27(8):2107–2119
Nie L, Zhang L, Yang Y, Wang M, Hong R, Chua T-S (2015) Beyond doctors: future health prediction from multimedia and multimodal observations. In: 23rd ACM international conference on Multimedia p 591–600
Nie L, Zhao Y-L, Akbari M, Shen J, Chua T-S (2014) Bridging the vocabulary gap between health seekers and healthcare knowledge. IEEE Trans Knowl Data Eng 27(2):396–409
Rivest R, Shamir A, Adelman L (1978) A method for obtaining digital signature and public key cryptosystem. Commun ACM 21:120–126
Schnorr CP (1991) Efficient signature generation by smart cards. J Cryptol 4(3):161–174
Siddiqui Z, Abdullah AH, Khan MK, Alghamdi AS (2001) Smart environment as a service: three factor cloud based user authentication for telecare medical information system. J Med Syst 64:201–205
Tseng YM (2006) GPRS/UMTS-aided authentication protocol for wireless LANs. IEE Proc Commun 153:810–817
Tseng YM (2007) A resource-constrained group key agreement protocol for imbalance wireless networks. J Comput Secur 26:331–337
Tseng YM, Wu TY, Wu JD (2008) A pairing-based user authentication scheme for wireless clients with smart cards. Informatica 19:285–302
Wang S, Cao Z, Cao F (2008) Efficient identity-based authenticated key agreement protocol with PKG forward secrecy. Int J Netw Secur 7:181–186
Wei J, Hu X, Liu W (2012) An improved authentication scheme for telecare medicine information systems. J Med Syst 36(6):3597–3604
Wong DS, Chan AH (2001) Efficient and mutually authenticated key exchange for low power computing devices. Proc. ASIACRYPT’01 172–289
Wu T-Y, Tseng Y-M (2010) An efficient client authentication and key agreement protocol for mobile client–server environment. Comput Netw 54:1520–1530
Xu J, Zhu WT, Feng DG (2009) An improved smart card based password authentication scheme with provable security. Comput Stand Interfaces 31(4):723–728
Yan Y, Liu G, Ricci E, Subramanian R, Liu G, Sebe N (2014) Multi-task linear discriminant analysis for multi-view action recognition. IEEE Trans Image Process 23(12):5599–5611
Yan Y, Ricci E, Subramanian R, Lanz O, Sebe N (2013) No matter where you are: flexible graph-guided multi-task learning for multi-view head pose classification under target motion. In: 2013 I.E. International Conference on Computer Vision (ICCV) p 1177–1184
Yang CC, Wang RC, Liu WT (2005) Secure authentication scheme for session initiation protocol. J Comput Secur 24:381–386
Yau W-C, Phan RC-W (2013) Security analysis of a chaotic map-based authentication scheme for telecare medicine information systems. J Med Syst 37:993
Yoon E-J, Yoo K-Y (2010) A new efficient ID-based user authentication and key exchange protocol for mobile client–server environment. In: 2010 I.E. International Conference on Wireless Information Technology and Systems (ICWITS) p 1–4
Zhao Z (2014) An Efficient anonymous authentication scheme for wireless body area networks using elliptic curve cryptosystem. J Med Syst 38:13
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
David, D.B. Mutual authentication scheme for multimedia medical information systems. Multimed Tools Appl 76, 10741–10759 (2017). https://doi.org/10.1007/s11042-016-3268-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-3268-7