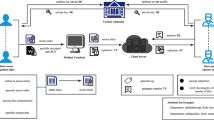
Abstract
Online personal health record (PHR) is more inclined to shift data storage and search operations to cloud server so as to enjoy the elastic resources and lessen computational burden in cloud storage. As multiple patients’ data is always stored in the cloud server simultaneously, it is a challenge to guarantee the confidentiality of PHR data and allow data users to search encrypted data in an efficient and privacy-preserving way. To this end, we design a secure cryptographic primitive called as attribute-based multi-keyword search over encrypted personal health records in multi-owner setting to support both fine-grained access control and multi-keyword search via Ciphertext-Policy Attribute-Based Encryption. Formal security analysis proves our scheme is selectively secure against chosen-keyword attack. As a further contribution, we conduct empirical experiments over real-world dataset to show its feasibility and practicality in a broad range of actual scenarios without incurring additional computational burden.




Similar content being viewed by others
Notes
m2-ABKS also supports user revocation (UR), the majority of existing UR schemes can be attached to m2-ABKS without any variation. As it is beyond the focus of this paper, we will not discuss the detail of UR in m2-ABKS due to space limit.
References
Wang, C., Wang, Q., Ren, K., and et al: Privacy-preserving public auditing for data storage security in cloud computing. In: Proceedings of 29th IEEE International Conference on Computer Communications (INFOCOM’10), pp. 525–533. doi:10.1109/INFCOM.2010.5462173 2010.
Ren, Y. J., Shen, J., Wang, J., et al, Mutual verifiable provable data auditing in public cloud storage. J. Intern. Technol. 16(2):68–81, 2015.
Yu, S. C., Wang, C., Ren, K., et al: Achieving secure, scalable, and fine-grained data access control in cloud computing. In: Proceedings of 29th IEEE International Conference on Computer Communications (INFOCOM’10), pp. 534–542. doi:10.1109/INFCOM.2010.5462174 2010.
Boneh, D., Crescenzo, G. D., Ostrovsky, R., et al: Public key encryption with keyword search. In: Proceedings of 23th International Conference on Theory and Applications of Cryptographic Techniques (EUROCRYPT’04), pp. 506–522. doi:10.1007/b97182 2004.
Fu, Z. J., Ren, K., Shu, J.G., and et al: Enabling personalized search over encrypted outsourced data with efficiency improvement. IEEE Transactions on Parallel and Distributed Systems. doi:10.1109/TPDS.2015.2506573 2015.
Goyal, V., Pandey, O., Sahai, A., and et al: Attribute-based encryption for fine-grained access control of encrypted data. In: Proceedings of 13th ACM Conference on Computer and Communications Security (CCS’06), pp. 89–98. doi:10.1145/1180405.1180418 2006.
Bethencourt, J., Sahai, A., Water, B: Ciphertext-policy attribute-based encryption. In: Proceedings of 28th IEEE Symposium on Security and Privacy (S&P’07), pp. 321–334. doi:10.1109/SP.2007.11 2007.
Sun, W. H., Yu, S. C., Lou, W. J., and et al: Protecting your right: attribute-based keyword search with fine-grained owner-enforced search authorization in the cloud. In: Proceedings of 33th IEEE International Conference on Computer Communications (INFOCOM’14), pp. 226–234. doi:10.1109/INFOCOM.2014.6847943 2014.
Li, M., Yu, S. C., Ren, K., and et al: Securing personal health records in cloud computing: patient-centric and fine-grained data access control in multi-owner settings. In: Proceedings of 6th International ICST Conference on Security and Privacy in Communication Networks (SecureComm’10), pp. 89–106. doi:10.1007/978-3-642-16161-2 2010.
Hwang, Y. H., and Lee, P. J: Public key encryption with conjunctive keyword search and its extension to a multi-user system. In: Proceedings of first International Conference on Pairing-Based Cryptography (Pairing’07), pp. 2–22. doi:10.1007/978-3-540-73489-5 2007.
Zheng, Q. J., Xu, S. H., Ateniese, G: VABKS: Verifiable attribute-based keyword search over outsourced encrypted data. In: Proceedings of 33th IEEE International Conference on Computer Communications (INFOCOM’14), pp. 522–530. doi:10.1109/INFOCOM.2014.6847976 2014.
Boneh, D., Boyen, X., Goh, E. J: Hierarchical identity based encryption with constant size ciphertext. In: Proceedings of 24th Annual International Conference on Theory and Applications of Cryptographic Techniques (EUROCRYPT’05), pp. 440–456. doi:10.1007/b136415 2005.
Bellare, M., and Rogaway, P: Random oracles are practical: a paradigm for designing efficient protocols. In: Proceedings of first ACM Conference on Computer and Communications Security (CCS’93), pp. 62–73. doi:10.1145/168588.168596 1993.
Waters, B.: Ciphertext-policy attribute-based encryption: an expressive, efficient, and provably secure realization. In: Proceedings of 14th International Conference on Practice and Theory in Public Key Cryptography (PKC’11), pp. 53–70. doi:10.1007/978-3-642-19379-8
Curtmola, R., Garay, J. A., Kamara, S., and et al: Searchable symmetric Encryption: improved definitions and efficient constructions. In: Proceedings of 13th ACM Conference on Computer and Communications Security (CCS’06), pp. 79–88. doi:10.1145/1180405.1180417 2006.
Bellare, M., Boldyreva, A., O’Neill, A.: Deterministic and efficiently searchable encryption. In: Proceedings of 27th Annual International Conference on Advances in Cryptology (CRYPTO’07), pp. 535–552. doi:10.1007/978-3-540-74143-5 2007.
Boneh, D., and Waters, B.: Conjunctive, subset, and range queries on encrypted data. In: Proceedings of 4th Conference on Theory of Cryptography (TCC’07), pp. 535–55. doi:10.1007/978-3-540-70936-7 2007.
Katz, J., Sahai, A., Waters, B.: Predicate encryption supporting disjunctions, polynomial equations, and inner products. In: Proceedings of 27th Annual International Conference on Theory and Applications of Cryptographic Techniques (EUROCRYPT’08), pp. 146–162. doi:10.1007/978-3-540-78967-3 2008.
Li, J., Wang, Q., Cao, C., and et al: Fuzzy keyword search over encrypted data in cloud computing. In: Proceedings of 29th IEEE International Conference on Computer Communications (INFOCOM’10), pp. 1–5. doi:10.1109/INFCOM.2010.5462196 2010.
Cao, N., Wang, C., Li, M., and et al, Privacy-preserving multi-keyword ranked search over encrypted cloud data. IEEE Trans. Parallel Distrib. Syst. 25(1):222–233, 2014. doi:10.1109/TPDS.2013.45.
Miao, Y. B., Liu, J., Ma, J. F.: Fine-grained searchable encryption over encrypted data in multi-clouds. In: Proceeding of 10th International Conference on Wireless Algorithms, Systems, and Applications (WASA 2015), pp. 407–416. doi:10.1007/978-3-319-21837-3-40 2015.
Li, H. W., Liu, D. X., Dai, Y. S., and et al, Enabling efficient multi-keyword ranked search over encrypted mobile cloud data through blind storage. IEEE Trans. Emerging Topics Comput. 3(1):127–138, 2015. doi:10.1109/TETC.2014.2371239.
Fu, Z. J., Sun, X. M., Liu, Q., et al, Achieving efficient cloud search services: multi-keyword ranked search over encrypted cloud data supporting parallel computing. IEICE Trans. Commun. E98-B(1):190–200, 2015.
Xia, Z. H., Wang, X. H., Sun, X. M., et al, A secure and dynamic multi-keyword ranked search scheme over encrypted cloud data. IEEE Trans. Parallel Distrib. Syst. 27(2):340–352, 2016. doi:10.1109/TPDS.2015.2401003.
Bao, F., Deng, R. H., Ding, X. H., et al: Private query on encrypted data in multi-user settings. In: Proceedings of 4th International Conference on Information Security Practice and Experience (ISPEC’08), pp. 71–85. doi:10.1007/978-3-540-79104-1 2008.
Ostrovsky, R., Sahai, A., Waters, B.: Attribute-based encryption with non-monotonic access structures. In: Proceedings of 14th ACM Conference on Computer and Communications Security (CCS’07), pp. 195–203. doi:10.1145/1315245.1315270 2007.
Chase, M., and Chow, S.M.S: Improving privacy and security in multi-authority attribute-based encryption. In: Proceedings of 16th ACM Conference on Computer and Communications Security (CCS’09), pp. 121–130. doi:10.1145/1653662.1653678 2009.
Lewko, B. A., Okamoto, T., Sahai, A., and et al, Fully secure functional encryption: Attribute-basedencryption and (hierarchical) inner product encryption. In: Proceedings of 29th Annual International Conference on Theory and Applications of Cryptographic Techniques (EUROCRYPT’10), pp. 62–91. doi:10.1007/978-3-642-13190-5, 2010.
Wang, C. J., Li, W. T., Li, Y., and et al: A ciphertext-policy attribute-based encryption scheme supporting keyword search function. In: Proceeding of 5th International Symposium on Cyberspace Safety and Security (CSS 2013), pp. 377–386. doi:10.1007/978-3-319-03584-0-28 2013.
Khader, D.: Introduction to attribute based searchable encryption. In: Proceeding of 11th International Conference on Communications and Multimedia Security (Communications and Multimedia Security 2014), pp. 131–135. doi:10.1007/978-3-662-44885-4-11 2014.
Liang, K. T., and Susilo, W., Searchable attribute-based mechanism with efficient data sharing for secure cloud storage. IEEE Trans. Inf. Forens. Secur. 10(9):1981–1992, 2015. doi:10.1109/TIFS.2015.2442215.
Acknowledgments
This work was supported by the National High Technology Research and Development Program (863 Program) (No. 2015AA016007, No. 2015AA017203), the Key Program of NSFC (No. U1405255, No. U1135002), the Changjiang Scholars and Innovation Research Team in University (No. IRT1078), the Fundamental Research Funds for the Center Universities (No. JY10000903001) and the Major Nature Science Foundation of China (No. 61370078, No. 61309016).
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection on Mobile Systems
Rights and permissions
About this article
Cite this article
Miao, Y., Ma, J., Liu, X. et al. m2-ABKS: Attribute-Based Multi-Keyword Search over Encrypted Personal Health Records in Multi-Owner Setting. J Med Syst 40, 246 (2016). https://doi.org/10.1007/s10916-016-0617-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-016-0617-z