Abstract
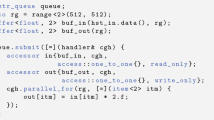
Pattern matching is the most time consuming task in many cybersecurity, bioinformatics and computational biological applications. Speeding up the pattern matching task is an essential step for the success of the aforementioned applications. Wu–Manber algorithm is one of the fastest and most widely used algorithms for multi-pattern matching. Many researchers focused on improving the performance of Wu–Manber algorithm and this work presents a novel attempt parallelize Wu–Manber and make it suitable for multi-core machines. This paper uses Kahn processing network (KPN) model to effectively parallelize data and functional tasks. KPN suggests a parallel programming model that can be utilized in today’s multi-core machines. Hence, we use the KPN model to tailor the execution of Wu–Manber algorithm by breaking down the complexity of data sharing and task processing. The data parallelization is implemented using concurrent executions of multiple KPNs. In addition, task parallelization is achieved within each executing KPN. A single KPN consists of two threads, a producer thread and a consumer thread. The proposed KPN-based parallelization achieves up to 4× speedup over the serial implementation of the algorithm. Finally, the algorithm performance scales well with increasing workloads and the speedup up remains almost constant with increasing number of attack signatures.









Similar content being viewed by others
References
Cpus: Core count vs. clock speed, which is better?—make tech easier. https://www.maketecheasier.com/cpus-core-count-vs-clock-speed/. Accessed 04 Jan 2017
Multiple core processors: Is more always better? https://www.lifewire.com/multiple-core-processors-832453. Accessed 04 Jan 2017
What is multi-core processor?—Definition from whatis.com. http://searchdatacenter.techtarget.com/definition/multi-core-processor. Accessed on 04 Jan 2017
Multithreaded programming (posix pthreads tutorial). https://randu.org/tutorials/threads/. Accessed 04 Jan 2017
Kahn, G.: The semantics of simple languages for parallel processing. In: The IFIP Congress, vol. 74 (1974)
Menard, C.: Mapping KPN-based applications to the NoC-based tomahawk architecture. Ph.D. Thesis, Master’s Thesis, TU Dresden, Mar 24, 2016. https://cfaed.tu-dresden.de/files/user/jcastrillon/theses/1603_Menard_DA.pdf (2016). Accessed 10 Oct 2016
Mohammad, M., Lin, E.-B., Darweesh, A., Howari, F.: Special B-spline tight framelet and it’s applications. J. Adv. Math. Comput. Sci. 29(5), 1–18 (2018). https://doi.org/10.9734/JAMCS/2018/43716
Parks, T.M.: Bounded scheduling of process networks. Ph.D. thesis, University of California, Berkeley, CA (1995)
Thiele, L., Bacivarov, I., Haid, W., Huang, K.: Mapping applications to tiled multiprocessor embedded systems. In: Seventh International Conference on Application of Concurrency to System Design, 2007. ACSD 2007, pp. 29–40. IEEE (2007)
Lee, E.A., Messerschmitt, D.G.: Synchronous data flow. Proc. IEEE 75(9), 1235–1245 (1987)
Kouzinopoulos, C.S., Assael, J.-A.M., Pyrgiotis, T.K., Margaritis, K.G.: A hybrid parallel implementation of the Aho–Corasick and Wu–Manber algorithms using NVIDIA CUDA and MPI evaluated on a biological sequence database. Int. J. Artif. Intell. Tools 24(01), 1540001 (2015)
Kouzinopoulos, C.S., Margaritis, K.G., Michailidis, P.D.: Parallel Processing of Multiple Pattern Matching Algorithms for Biological Sequences: Methods and Performance Results. INTECH Open Access Publisher, Vienna (2011)
Kharbutli, M., Aldwairi, M., Mughrabi, A.: Function and data parallelization of Wu–Manber pattern matching for intrusion detection systems. Netw. Protoc. Algorithms 4(3), 46–61 (2012)
Otoum, S., Kantarci, B., Mouftah, H.T.: On the feasibility of deep learning in sensor network intrusion detection. IEEE Netw. Lett. (2019). https://doi.org/10.1109/LNET.2019.2901792
Aloqaily, M., Otoum, S., Ridhawi, I.A., Jararweh, Y.: An intrusion detection system for connected vehicles in smart cities. Ad Hoc Netw. 90, 101842 (2019). https://doi.org/10.1016/j.adhoc.2019.02.001
Antonatos, S., Anagnostakis, K.G., Markatos, E.P.: Generating realistic workloads for network intrusion detection systems. In: ACM SIGSOFT Software Engineering Notes, vol. 29, pp. 207–215. ACM, New York (2004)
Aldwairi, M., Khamayseh, Y., Al-Masri, M.: Application of artificial bee colony for intrusion detection systems. Sec. Commun. Netw. 8(16), 2730–2740 (2015). https://doi.org/10.1002/sec.588
Wu, S., Manber, U.: A fast algorithm for multi-pattern searching. Technical Report
Aldwairi, M., Ekailan, N.: Hybrid pattern matching algorithm for intrusion detection systems. J. Inf Assur. Secur. 6(6), 512–521 (2011)
Horspool, R.N.: Practical fast searching in strings. Softw. Pract. Exp. 10(6), 501–506 (1980)
Boyer, R.S., Moore, J.S.: A fast string searching algorithm. Commun. ACM 20(10), 762–772 (1977)
Vrba, Ž., Halvorsen, P., Griwodz, C., Beskow, P., Espeland, H., Johansen, D.: The Nornir run-time system for parallel programs using Kahn process networks on multi-core machines-a flexible alternative to MapReduce. J. Supercomput. 63(1), 191–217 (2013)
Dean, J., Ghemawat, S.: Mapreduce: simplified data processing on large clusters. Commun. ACM 51(1), 107–113 (2008). https://doi.org/10.1145/1327452.1327492
Aldwairi, M., Abu-Dalo, A.M., Jarrah, M.: Pattern matching of signature-based IDS using Myers algorithm under MapReduce framework. EURASIP J. Inf. Secur. 2017(1), 9 (2017). https://doi.org/10.1186/s13635-017-0062-7
Sarveshwaran, V., Premalatha, J.: Intrusion detection of distributed denial of service attack in cloud. Clust. Comput. https://doi.org/10.1007/s10586-017-1149-0
Vimala, S., Khanaa, V., Chidambaram, N.: A study on supervised machine learning algorithm to improvise intrusion detection systems for mobile ad hoc networks. Clust. Comput. https://doi.org/10.1007/s10586-018-2686-x
Malik, A., Khan, F.: A hybrid technique using binary particle swarm optimization and decision tree pruning for network intrusion detection. Clust. Comput. https://doi.org/10.1007/s10586-017-0971-8
Aldwairi, M., Mardini, W., Alhowaide, A.: Anomaly payload signature generation system based on efficient tokenization methodology. Int. J. Commun. Antenna Propag. (IRECAP). https://doi.org/10.15866/irecap.v8i5.12794
Tran, T., Giraud, M., Varré, J.-S.: Bit-parallel multiple pattern matching. In: International Conference Parallel Processing and Applied Mathematics, pp. 292–301 (2012)
Pyrgiotis, T.K., Kouzinopoulos, C.S., Margaritis, K.G.: Parallel implementation of the Wu–Manber algorithm using the OpenCL framework. In: IFIP International Conference on Artificial Intelligence Applications and Innovations, pp. 576–583. Springer, New York (2012)
Huang, N.-F., Hung, H.-W., Lai, S.-H., Chu, Y.-M., Tsai, W.-Y.: A GPU-based multiple-pattern matching algorithm for network intrusion detection systems. In: 22nd International Conference on Advanced Information Networking and Applications-Workshops, 2008. AINAW 2008. IEEE, pp. 62–67 (2008)
Ramesh, M., Jeon, H.: Parallelizing deep packet inspection on GPU. In: 2018 IEEE Fourth International Conference on Big Data Computing Service and Applications (BigDataService), pp. 248–253 (2018). https://doi.org/10.1109/BigDataService.2018.00044
Ho, T., Cho, S., Oh, S.: Parallel multiple pattern matching schemes based on Cuckoo filter for deep packet inspection on graphics processing units. IET Inf. Secur. 12(4), 381–388 (2018). https://doi.org/10.1049/iet-ifs.2017.0421
Geilen, M., Basten, T.: Requirements on the execution of Kahn process networks. Programming Languages and Systems, pp. 319–334 (2003)
Aldwairi, M., Al-Khamaiseh, K.: Exhaust: optimizing Wu-Manber pattern matching for intrusion detection using bloom filters. In: 2015 2nd World Symposium on Web Applications and Networking (WSWAN), pp. 1–6 (2015). https://doi.org/10.1109/WSWAN.2015.7209081
Aldwairi, M., Alansari, D.: Exscind: fast pattern matching for intrusion detection using exclusion and inclusion filters. In: 2011 7th International Conference on Next Generation Web Services Practices, pp. 24–30 (2011). https://doi.org/10.1109/NWeSP.2011.6088148
Acknowledgements
This work is supported by Zayed University Research Incentive Fund Grant # 18054.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Aldwairi, M., Hamzah, A.Y. & Jarrah, M. KPN-based parallelization of Wu–Manber algorithm on multi-core machines. Cluster Comput 23, 725–734 (2020). https://doi.org/10.1007/s10586-019-02955-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-019-02955-9