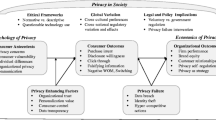
Abstract
Consumers of software often face an acquisition-mode decision, namely whether to purchase or pirate that software. In terms of consumer welfare, consumers who pirate software may stand in opposition to those who purchase it. Marketers also face a decision whether to attempt to thwart that piracy or to ignore, if not encourage it as an aid to their software’s diffusion, and policymakers face the decision whether to adopt interventionist policies, which are government-centric, or laissez faire policies, which are marketer-centric. Here in order to assess the decision-making of all three of these stakeholders, we focus on the consumer’s point-of-view as central and examine it by considering on a comparative basis the ethical dimension versus other dimensions, including economic, legal, and other salient consumer behavior considerations. Based on a survey of 689 software consumers conducted over the Internet, the results indicate that ethics as a factor is embedded in a multidimensional set of determinant factors influencing software piracy, including attitudes, legal aspects, social support, perceptions of economic loss and age. Policy and research implications, based on these findings, are provided.
Similar content being viewed by others
References
H. Aarts A. Dijksterhuis (2000) ArticleTitle‘Habits as Knowledge Structures: Automaticity in Goal-Directed Behavior’ Journal of Personality and Social Psychology 78 IssueID1 53–63
I. Ajzen M. Fishbein (1980) Understanding Attitudes and Predicting Social Behavior Prentice-Hall Englewood Cliffs, NJ
I. Ajzen M. Fishbein (1985) From Intentions to Actions: A Theory of Planned Behavior J. Hugland J. Beckman (Eds) Action-Control: From Cognitions to Behavior Springer Heidelberg 11–39
N. D. Albers-Miller (1999) ArticleTitle‘Consumer Misbehavior: Why People Buy Illicit Goods’ Journal of Business Ethics 16 IssueID3 273–287
Anonymous: 1999, ‘Technology has Become New Gender Gap, AAUW Says’, Research Technology Management 42(2), 8.
B. J. Babin L. A. Babin (1996) ArticleTitle‘Effects of Moral Cognitions and Consumer Emotions on Shoplifting Intentions’ Psychology and Marketing 13 IssueID8 785–802
L. Barton Y. Malhotra (1993) ArticleTitle‘International Infringement of Software as Intellectual Property’ Industrial Management and Data Systems 93 IssueID8 20–28 Occurrence Handle10.1108/02635579310043930
R. K. Basi (1999) ArticleTitleWWW Response Rates to Socio-Demographic Items Journal of the Market Research Society 41 IssueID4 397
D. J. Bem (1967) ArticleTitle‘Self-perception: An Alternative Interpretation of Cognitive Dissonance Phenomena’ Psychological Review 74 IssueID3 183–200
Y. Benkler (2001) ArticleTitle‘The Battle over the Institutional Ecosystem in the Digital Environment’ Association for Computing Machinery Communications of the ACM 44 IssueID2 84–90
P. N. Bloom (1989) ArticleTitle‘A Decision Model for Prioritizing and Addressing Consumer Information Problems’ Journal of Public Policy and Marketing 8 161–180
M. Bommer C. Gratto J. Gravander M Tuttle (1987) ArticleTitleA Behavioral Model of Ethical and Unethical Decision Making Journal of Business Ethics 6 IssueID4 265–280
M. K. Chang (1998) ArticleTitle‘Predicting Unethical Behavior: A Comparison of the Theory of Reasoned Action on the Theory of Planned Behavior’ Journal of Business Ethics 17 IssueID16 1825–1834
H. K. Cheng R. R Sims H. Teegen (1997) ArticleTitle‘To Purchase or to Pirate Software: An Empirical Study’ Journal of Management Information Systems 13 IssueID4 49–60
K. D. Christensen (1997) ArticleTitle‘Fighting Software Piracy in Cyberspace: Legal and Technological Solutions’ Law and Policy in International Business 28 IssueID2 435–475
G. Churchill Jr. A. (1979) ArticleTitle‘A Paradigm for Developing Better Measures of Marketing Constructs’ Journal of Marketing Research 16 IssueID1 64–73
C. Cobanoglu B. Warde P. J. Moreo (2001) ArticleTitle‘A Comparison of Mail, Fax and Web-based Survey Methods’ International Journal of Market Research 43 IssueID4 441–452
K. R. Conner R. P. Rumelt (1991) ArticleTitle‘Software Piracy: An Analysis of Protection Strategies’ Management Science 37 IssueID2 125–139 Occurrence Handle10.1287/mnsc.37.2.125
Coomber, R.: 1997, ‘Using the Internet for Survey Research,’ Sociological Research Online, 2(2). E-Journal on-line. Available from http://www.socresonline.org. uk/socresonline/2/2/2.html.
L. Copeland (2000) ArticleTitleOnline Auctions Fuel Software Piracy Computerworld 34 IssueID17 32
M. P. Couper (2000) ArticleTitle‘Web surveys: A review of issues and approaches’ Public Opinion Quarterly 64 IssueID4 464–494
D. Cox A. D. Cox G. P. Moschis (1990) ArticleTitle‘When Consumer Behavior Goes Bad: An Investigation of Adolescent Shoplifting’ Journal of Consumer Research 17 IssueID2 149–159
T. W. Dunfee N. Craig Smith W. T. Ross SuffixJr (1999) ArticleTitle‘Social Contracts and Marketing Ethics’ Journal of Marketing 63 IssueID3 14–32
M. M. Eining A. L. Christensen (1991) ‘A Psycho-Social Model of Software Piracy: The Development and Test of a Model’, R. Dejoie G. Fowler D. Paradice (Eds) Ethical Issues in Information Systems Boyd and Fraser Publishing Company Boston, MA
L. Fallan (1999) ArticleTitle‘Gender, Exposure to Tax Knowledge, and Attitudes towards Taxation: An Experimental Approach’ Journal of Business Ethics 18 IssueID2 173–184
P. Fruitman (2001) ‘Software Piracy Down in Most of Canada’, Computing Canada 27 IssueID24 9
K. Fukukawa (2002) ArticleTitle‘Developing a Framework for Ethically Questionable Behavior in Consumption’ Journal of Business Ethics 41 IssueID(1/2) 99–120
M. Givon V. Mahajan E. Muller (1995) ArticleTitle‘Software Piracy: Estimation of Lost Sales and the Impact on Software Diffusion’ Journal of Marketing 59 IssueID1 29–37
R. S. Glass W. A. Wood (1996) ArticleTitle‘Situational Determinants of Software Piracy: An Equity Theory Perspective’ Journal of Business Ethics 15 IssueID11 1189–1198
R. D. Gopal G. L. Sanders (1997) ArticleTitle‘Preventive and Deterrent Controls for Software Piracy’ Journal of Management Information Systems 13 IssueID4 29–47
S. J. Gould (1992) ‘Marketing Exchange as a Product of Perceived Value and Control’ J. N. Sheth (Eds) Research in Marketing JAI Press Greenwich, CT 115–146
Gould, S. J.: 1995, ‘Consumer Versus Consumer, Business Versus Business, Government Versus Government, Coalition Versus Coalition: A Multiparty, Regulatory Paradigm for Public Policy and Marketing,’ in P. S. Ellen and Patrick J. Kaufmann (eds.), Proceedings of the 1995 Marketing and Public Policy Conference (Georgia State University, Atlanta), pp. 93--96.
G. T. Gundlach P. E. Murphy (1993) ArticleTitle‘Ethical and Legal Foundations of Relational Marketing Exchanges’ Journal of Marketing 57 IssueID4 35–46
C. Hare (1999) ArticleTitle‘Towards an Ontology of Intellectual Property: A Suggested Reconstruction’ The American Journal of Economics and Sociology 58 IssueID2 285–297
S. Hinduja (2003) ArticleTitle‘Trends and Patterns Among Online Software Pirates’ Ethics and Information Technology 5 IssueID1 49–61
S. J. Hoch J. Deighton (1989) ArticleTitle‘Managing What Consumers Learn from Experience’ Journal of Marketing 53 IssueID2 1–20
N. F. Holsing D. C. Yen (1999) ArticleTitle‘Software Asset Management: Analysis, Development and Implementation’ Information Resources Management Journal 12 IssueID3 14–26
F. S. Houston J. B. Gassenheimer (1987) ArticleTitle‘Marketing and Exchange’ Journal of Marketing 51 IssueID4 3–18
F. S. Houston J. B. Gassenheimer J. M. Maskulka (1992) Marketing Exchange Transactions and Relationships Quorum Books Westport, CT
S. D. Hunt S. J. Vitell (1986) ArticleTitle‘A General Theory of Marketing Ethics’ Journal of Macromarketing 6 IssueID1 5–16
B. W. Husted (2000) ArticleTitle‘The Impact of National Culture on Software Piracy’ Journal of Business Ethics 26 IssueID3 197–211
T. M. Jones (1991) ArticleTitle‘Ethical Decision Making by Individuals in Organizations: An Issue-Contingent model’ Academy of Management Review 16 IssueID2 366–395
M. Katz C. Shapiro (1986) ArticleTitle‘Technology Adoption in the Presence of Network Externalities’ Journal of Political Economy 94 IssueID4 822–841
L. Kohlberg (1969) Stage and Sequence: The Cognitive Developmental Approach to Socialization D. Goslin (Eds) Handbook of Socialization Theory and Research Rand-McNally Chicago 347–480
S. W. Kopp T. A. Suter (1998) ArticleTitle‘Developments in Copyright Policy and Network Technologies: The First Generation’ Journal of Public Policy and Marketing 17 IssueID2 303–312
J. Kreie T. P. Cronan (1999) ArticleTitle‘Copyright, Piracy, Privacy, and Security Issues: Acceptable Or Unacceptable Actions For End Users?’ Journal of End User Computing 11 IssueID2 13–20
F.-Y. Kuo (2001) ArticleTitle‘Development and Validation of Ethical Computer Self-efficacy Measure: The Case of Softlifting’ Journal of Business Ethics 32 IssueID4 299–315
J. Langenderfer D. L. Cook (2001) ArticleTitle‘Copyright Policies and Issues Raised by A and M Records v Napster: ‘The Shot Heard ‘Round the World’ or ‘Not with a Bang but a Whimper?’ Journal of Public Policy and Marketing 20 IssueID2 280–288
J. M. Logsdon J. K. Thompson R. A. Reid (1994) ArticleTitle‘Software Piracy: Is It Related to Level of Moral Judgment?’ Journal of Business Ethics 13 IssueID11 849–857
M. L. Meuter A. L. Ostrom R. I. Roundtree M. J. Bitner (2000) ArticleTitle‘Self-Service Technologies: Understanding Customer Satisfaction with Technology-Based Service Encounters’ Journal of Marketing 64 IssueID3 50–64
T. W. Miller (2001) ArticleTitleCan We Trust the Data of Online Research? Marketing Research 13 IssueID2 26–32
M. Mosquera (1999) ArticleTitleThe High Price of Software Piracy Computer Reseller News 843 76
G. Nettler (1984) Explaining Crime McGraw-Hill New York
E. Oz (2001) ArticleTitle‘Organizational Commitment and Ethical Behavior: An Empirical Study of Information System Professionals’ Journal of Business Ethics 34 IssueID2 123–136
J. L. Ozanne R. P. Hill N. D. Wright (1998) ArticleTitle‘Juvenile Delinquents’ Use of Consumption as Cultural Resistance: Implications of Juvenile Reform Programs and Public Policy’ Journal of Public Policy and Marketing 17 IssueID2 185–196
J. P. Peter (1981) ArticleTitle‘Construct Validity: A Review of Basic Issues and Marketing Practices’ Journal of Marketing Research 18 IssueID2 133–145
L. D. Peters (2002) ArticleTitle‘Theory Testing in Social Research’ The Marketing Review 3 65–82
M. Y. A. Rawwas A. Singhapakdi (1998) ArticleTitle‘Do Consumers’ Ethical Beliefs Vary with Age? A Substantiation of Kohlberg’s Typology in Marketing’ Journal of Marketing Theory and Practice 6 IssueID2 26–38
J. Ray (1987) ArticleTitle‘Every Twelfth Shopper: Who Shoplifts and Why?’ Social Casework The Journal of Contemporary Social Work 68 234–239
R. E. Reidenbach D. P. Robin L. Dawson (1991) ArticleTitle‘An Application and Extension of a Multidimensional Ethics Scale to Selected Marketing Practices and Marketing Groups’ Journal of the Academy of Marketing Science 19 IssueID2 83–92
E. M. Rogers (1983) Diffusion of Innovations Free Press New York
D. Ruegger E. W. King (1992) ArticleTitle‘A Study of Effect of Age and Gender upon Student Business Ethics’ Journal of Business Ethics 11 IssueID3 179–186
P.M. Simpson D. Banerjee C.L. Simpson SuffixJr. (1994) ArticleTitle‘Softlifting: A Model of Motivating Factors’ Journal of Business Ethics 13 IssueID6 431–438
R. R. Sims H. K. Cheng H. Teegen (1996) ArticleTitle‘Toward a Profile of Student Software Piraters’ Journal of Business Ethics 15 IssueID8 839–849
D. Strutton S. J. Vitell L. E. Pelton (1994) ArticleTitle‘How Consumers May Justify Inappropriate Behavior in Market Settings: An Application on the Techniques of Neutralization’ Journal of Business Research 30 IssueID3 253–260
C. Summers E. Markusen (1992) ArticleTitle‘Computers, Ethics, and Collective Violence’ Journal of Systems and Software 17 IssueID1 91–103
W. R. Swinyard H. Rinne A. K. Kau (1990) ArticleTitle‘The Morality of Software Piracy: A Cross-Cultural Analysis’ Journal of Business Ethics 9 655–664
L. Takeyama (1997) ArticleTitle‘The Intertemporal Consequences of Unauthorized Reproduction of Intellectual Property’ Journal of Law and Economics 40 IssueID2 511–522
T. Tamai (1998) ArticleTitle‘Abstraction Oriented Property of Software and Its Relation to Patentability’ Information and Software Technology 40 IssueID(5/6) 253–257
B. Tan (2002) ArticleTitle‘Understanding Consumer Ethical Decision Making with Respect to Purchase of Pirated Software’ The Journal of Consumer Marketing 19 IssueID(2/3) 96–111
H. Taylor (1999/2000) ArticleTitleDoes Internet Research Work? Journal of the Market Research Society 42 IssueID1 51–63
J. Y. L. Thong C.-S. Yap (1998) ArticleTitle‘Testing an Ethical Decision-making Theory: The Case of Softlifting’ Journal of Management Information Systems 15 IssueID1 213–237
L. K. Treviono S. A. Youngblood (1990) ArticleTitleBad Apples in Bad Barrels: A Causal Analysis of Ethical Decision-Making Behavior Journal of Applied Psychology 75 IssueID4 378–385
G. R. Wagman S. B. Schofield (1999) ArticleTitle‘The Competitive Advantage of Intellectual Property’, S.A.M Advanced Management Journal 64 IssueID3 4–8
S. C. Wagner G. L. Sanders (2001) ArticleTitle‘Considerations in Ethical Decision-making and Software Piracy’ Journal of Business Ethics 29 IssueID(1/2) 161–167
O. E. Williamson (1985) The Economic Institutions of Capitalism The Free Press New York
www.spa.org/piracy/default.asp, SIIA/KPMG: 2002a, ‘Nearly 30% Acquiring Software Via the Internet Could be Classified as Pirates.’ Internet on-line. Available from Software and Information IndustryAssociation (SIIA), Washington, DC.
www.spa.org/piracy/default.asp: 2002b, ‘Five Years: $59.2 Billion Lost Software Industry Suffers From Cumulative Impact of Global Software Piracy; Publisher Losses Total $12.2 Billion in 1999.’ Available from Software & Information Industry Association (SIIA), Washington, DC.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Gupta, P.B., Gould, S.J. & Pola, B. “To Pirate or Not to Pirate”: A Comparative Study of the Ethical Versus Other Influences on the Consumer’s Software Acquisition-Mode Decision. J Bus Ethics 55, 255–274 (2004). https://doi.org/10.1007/s10551-004-0991-1
Issue Date:
DOI: https://doi.org/10.1007/s10551-004-0991-1