Abstract
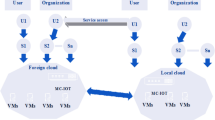
Intrusion Detection Systems (IDS) are utilized to identify malicious attacks and restore a secure state for the network, in cloud environment. Cloud assisted IDS having hybridized components from Machine Learning models has demonstrated better performance on parameters like Accuracy, DR and FPR. Machine Learning techniques facilitate accurate categorization and attack prediction with different IDS related databases. Some issues which need to be addressed are the selection or fusion of the sub set of features to be selected for analysis and detection of attacks considering high data sizes available and design of appropriate classification model. Using chosen features, computational Intelligence techniques provide better efficacy on a reiterative basis. The main issue to be addressed is the choice of a suitable scheme that provides better outcomes. This paper presents a Hybridized Meta-heuristic model that unified Deep Quantum Neural Network using Angular Separation Distance for feature fusion, White Shark- Dwarf Mongoose Optimization based on Fuzzy Classifier for parameter optimization, and Deep Residual Network classification model, to design effectual IDS in cloud platform. The proposed model performed with accuracy of 90.6%, F1-score of 90.2%, precision of 90.5% and recall of 90.5%.








Similar content being viewed by others
Data availability
No data and materials are available for this paper.
Code availability
The data and code can be given based on the request.
References
Aldosari F, Abualigah L, Almotairi KH (2022) A normal distributed dwarf mongoose optimization algorithm for global optimization and data clustering applications. Symmetry 14(5):1021
Bhingarkar S, Revathi ST, Kolli CS, and Mewada HK, (2022) An effective optimization enabled deep learning based Malicious behaviour detection in cloud computing. Int J Intell Robot Appl, pp1–14
BoT-IoT dataset taken from, “https://ieee-dataport.org/documents/bot-iot-dataset”, accessed on Nov (2021).
Braik M, Hammouri A, Atwan J, Al-Betar MA, Awadallah MA (2022) White shark optimizer: a novel bio-inspired meta-heuristic algorithm for global optimization problems. Knowl-Based Syst 243:108457
Devandar Rao B and Ramkumar Jayaraman (2023) A novel quantum identity authentication protocol without entanglement and preserving pre-shared key information. Quantum Information Processing, Springer (Post-Production), 22, Article No 92
Elmasry W, Akbulut A, Zaim AH (2021) A design of an integrated cloud-based intrusion detection system with third party cloud service. Open Comput Sci 11(1):365–379
Fatani A, Dahou A, Al-Qaness MA, Lu S, Elaziz MA (2021) Advanced feature extraction and selection approach using deep learning and Aquila optimizer for IoT intrusion detection system. Sensors 22(1):140
Jaber AN, Rehman SU (2020) FCM–SVM based intrusion detection system for cloud computing environment. Clust Comput 23(4):3221–3231
Jain YK, Bhandare SK (2011) Min max normalization based data perturbation method for privacy protection. Int J Comput Commun Technol 2(8):45–50
Jamil F, Kim D (2021) An ensemble of prediction and learning mechanism for improving accuracy of anomaly detection in network intrusion environments. Sustainability 13(18):10057
Karuppusamy L, Ravi J, Dabbu M, Lakshmanan S (2022) Chronological salp swarm algorithm based deep belief network for intrusion detection in cloud using fuzzy entropy. Int J Num Model Electr Netw Dev Field 35(1):2948
Kerstin B, Dmytro B, Terry F, Tobias O, Robert S and Ramona W, (2019) Efficient learning for deep quantum neural networks. Nature
Krishnaveni S, Sivamohan S, Sridhar SS, Prabakaran S (2021) Efficient feature selection and classification through ensemble method for network intrusion detection on cloud computing. Clust Comput 24(3):1761–1779
Liu Z, Qin T, Guan X, Jiang H, Wang C (2018) An integrated method for anomaly detection from massive system logs. IEEE Access 6:30602–30611
Munivara Prasad K, Rama Mohan Reddy A, VenugopalRao K (2017) BARTD: Bio-inspired anomaly based real time detection of under rated App-DDoS attack on web. J King Saud Univ Comput Inf Sci, Available online 14 Jul
NSL-KDD dataset taken from, “https://www.unb.ca/cic/datasets/nsl.html”, accessed on Nov (2021).
Prabhakaran V, Kulandasamy A (2021) Hybrid semantic deep learning architecture and optimal advanced encryption standard key management scheme for secure cloud storage and intrusion detection. Neural Comput Appl 33(21):14459–14479
Devendar Rao and Ramkumar Jayaraman, (2022) A novel QIA protocol based on Bell states position by Random selection. Int Conf Data Anal Manag, Poland
Shyla SI, Sujatha SS (2020) An efficient automatic intrusion detection in cloud using optimized fuzzy inference system. Int J Inf Secur Privacy (IJISP) 14(4):22–41
Singh P, Ranga V (2021) Attack and intrusion detection in cloud computing using an ensemble learning approach. Int J Inf Technol 13(2):565–571
Sugave S, Jagdale B (2020) Monarch-EWA: Monarch-earthworm-based secure routing protocol in IoT. Comput J 63(6):817–831
Wang W, Du X, Shan D, Qin R and Wang N, (2020) Cloud intrusion detection method based on stacked contractive auto-encoder and support vector machine. IEEE Trans Cloud Comput
Zhou S, Chen B, Zhang Y, Liu H, Xiao Y and Pan X, (2020) A feature extraction method based on feature fusion and its application in the text-driven failure diagnosis field.
Funding
No Funding is applicable.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest. The manuscript was written through contributions of all authors. All authors have given approval to the final version of the manuscript.
Ethical approval
The article has no research involving Human Participants and/or Animals.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Raj, M.G., Pani, S.K. Intrusion detection system using combination of deep residual fuzzy network and white shark-dwarf mongoose optimization. Soft Comput (2023). https://doi.org/10.1007/s00500-023-08569-z
Accepted:
Published:
DOI: https://doi.org/10.1007/s00500-023-08569-z