Abstract
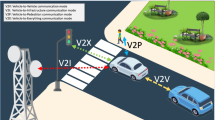
Vehicular ad hoc network (VANET) has been proposed to improve traffic safety and driving experience. This is realized by equipping vehicles with capacity to talk to each other. Vehicular communication security and privacy are viewed as a major obstacle to widely deploy VANET. Most existing works devote to the authenticity and identity anonymity of vehicle-to-vehicle (V2V) communications. In this paper, we investigate secure vehicle-to-infrastructure (V2I) communications for applications in which a traffic monitoring center collects information about the traffic and road status through VANET. We propose a scalable privacy-enhanced traffic monitoring (SPETM) framework. In this framework, the traffic monitoring center can collect authenticated individual vehicle driving status and the road usage information, with the help of the distributed roadside units (RSUs) who can simultaneously obtain local view of the traffic in their respective domains. Neither external attackers, malicious vehicles nor compromised RSUs can know the identity of the reporting vehicles, which guarantees enhanced privacy for vehicles. However, misbehaving vehicles abusing the privacy mechanisms can be jointly traced by the semi-trusted vehicle management authorities, which provides desirable liability in privacy-preserving vehicular reports. We instantiate a concrete SPETM scheme with well-established cryptographic technologies. Thorough analyses show that our scheme is secure and practical for deployment.

Similar content being viewed by others
References
(2006) IEEE trial-use standard for wireless access in vehicular environments security services for applications and management messages, IEEE Std. 1609.2-2006
(2009) Standard specification for telecommunications and information exchange between roadside and vehicle systems—5 GHz band dedicated short range communications (DSRC) medium access control (MAC) and physical layer (PHY) specifications, ASTM E2213–03. http://www.iteris.com/itsarch/html/standard/dsrc5ghz.htm
Boyen X, Waters B (2006) Compact group signatures without random oracles. In: Proceeding of Eurocrypt’06, Lecture Notes in Computer Science, vol. 4004, Springer, pp 427–444
Calandriello G, Papadimitratos P, Hubaux J-P, Lioy A (2011) On the performance of secure vehicular communication systems. IEEE Trans Dependable Secur Comput 8(6):898–912
Calandriello G, Papadimitratos P, Lioy A, Hubaux J-P (2007) Efficient and robust pseudonymous authentication in VANET. Montréal, QC, Canada. In: Proceeding of ACM international workshop on vehicular Ad Hoc networks-VANET, pp 19–28
Chaum D, Pedersen TP (1993) Wallet databases with observers. In: Proceeding of Crypto 1992. Lecture Notes in Computer Science 740:89–105
Damgård IB (1991) Towards practical public key systems secure against chosen ciphertext attacks. In: Proceeding of Crypto’91, Lecture Notes in Computer Science, vol. 576, Springer, pp 445–456
Daza V, Domingo-Ferrer J, Sebé F, Viejo A (2009) Trustworthy privacy-preserving car-generated announcements in vehicular ad hoc networks. IEEE Trans Veh Technol 58(4):1876–1886
Galbraith SD, Paterson KG, Smart NP (2008) Pairings for cryptographers. Discrete Applied Mathematics. 156(16):3113–3121
Haas JJ, Hu Y-C, Laberteaux KP (2011) Efficient certificate revocation list organization and distribution. IEEE J Sel Areas Commun 29(3):595–604
Hartmut S (2005) Organic computing C A new vision for distributed embedded systems. In: Proceeding of ISORC’05, IEEE, IEEE Computer Society, pp 201–203
http://www.sevecom.org/. 2010
Huang D, Misra S, Verma M, Xue G (2011) PACP: an efficient pseudonymous authentication-based conditional privacy protocol for VANETs. IEEE Trans Intell Transp Syst 12(3):736–746
Joux A (2004) A one round protocol for tripartite Diffie–Hellman. J Cryptol 17:263–276
Kamat P, Baliga A, Trappe W (2008) Secure, pseudonymous, and auditable communication in vehicular ad hoc networks. Secur Commun Netw 1(3):233–244
Kamat P, Baliga A, Trappe W (2006) An identity-based security framework for VANETs. In: Proceeding of third ACM Int’l workshop vehicular Ad Hoc networks (VANET’06), pp 94–95
Kocher PC (1996) Timing attacks on implementations of Diffie–Hellman, RSA, DSS, and other systems. In: Proceeding of Crypto 96, LNCS 1109, Springer, pp 104–113
Lin X, Sun X, Ho P-H, Shen X (2007) GSIS: a secure and privacy preserving protocol for vehicular communications. IEEE Trans Veh Technol 56(6):3442–3456
Lu R, Lin X, Luan TH, Liang X, Shen X (2012) Pseudonym changing at social spots: an effective strategy for location privacy in VANETs. IEEE Trans Veh Technol 61(1):86–96
Nguyen L, Safavi-Naini R (2005) Dynamic \(k\)-times anonymous authentication. In: Proceeding of ACNS 2005, LNCS 3531, Springer, pp 318–333
Qin B, Wu Q, Domingo-Ferrer J, Zhang L (2011) Preserving security and privacy in large-scale VANETs. In: Proceeding of ICICS 2011, LNCS 7043, Springer, pp 121–135
Raya M, Hubaux J-P (2007) Securing vehicular ad hoc networks. J Comput Secur 15(1):39–68
Ross PE (2015) Thus spoke the autobahn. IEEE Spectr 52(1):52–55
Schnorr CP (1990) Efficient identification and signatures for smart cards. In: Proceeding of Crypto’89, Lecture Notes in Computer Science, vol. 435, Springer, Berlin, pp 235–251
Shamir A (1979) How to share a secret. Communications of the ACM 22:612–613
Shamir A (1984) Identity based cryptosystems and signature schemes. In: Proceeding of Crypto 84, LNCS 196, Springer, pp 47–53
Standaert F, Malkin T, Yung M (2009) A unified framework for the analysis of side-channel key recovery attacks. In: Proceeding of Eurocrypt 2009, LNCS 5479, Springer, pp 443–461
Sun J, Zhang C, Zhang Y, Fang Y (2010) An identity-based security system for user privacy in vehicular ad hoc networks. IEEE Trans Parallel Distrib Syst 21(9):1227–1239
van den Berg E, Zhang T, Pietrowicz S (2009) Blend-in: a privacy-enhancing certificate-selection method for vehicular communication. IEEE Trans Veh Technol 58(9):5190–5198
Wasef A, Lu R, Lin X, Shen X (2010) Complementing public key infrastructure to secure vehicular ad hoc networks. IEEE Wirel Commun 17(5):22–28
Wasef A, Jiang Y, Shen X (2010) DCS: an efficient distributed-certificate-service scheme for vehicular networks. IEEE Trans Veh Technol 59(2):533–549
Wasef A, Shen X (2009) EDR: efficient decentralized revocation protocol for vehicular ad hoc networks. IEEE Trans Veh Technol 58(9):5214–5224
Wasef A, Shen X (2013) EMAP: expedite message authentication protocol for vehicular Ad Hoc networks. IEEE Trans Mobile Comput 12(1):78–89
WHO 2009 report (2010) http://whqlibdoc.who.int/publications/2009/9789241563840_eng
Wu Q, Domingo-Ferrer J, González-Nicolás U (2010) Balanced trustworthiness, safety and privacy in vehicle-to-vehicle communications. IEEE Trans Veh Technol 59(2):559–573
Zhang L, Wu Q, Solanas A, Domingo-Ferrer J (2010) A scalable robust authentication protocol for secure vehicular communications. IEEE Trans Veh Technol 59(4):1606–1617
Zhang C, Lu R, Lin X, Ho P, Shen X (2008) An efficient identity-based batch verification scheme for vehicular sensor networks. Proc. IEEE INFOCOM, pp 246–250
Acknowledgments
This paper is partially supported by the National Key Basic Research Program (973 program) under Project 2012CB315905, by the Natural Science Foundation under Projects 61370190, 61272501, 61173154, 61402029 and 61003214, by the Beijing Natural Science Foundation through Projects 4132056 and 4122041, by the Natural Science Foundation of Guangdong Province through Projects 2014A030313517 and S2012020011071, the Fundamental Research Funds for the Central Universities, and the Research Funds (No. 14XNLF02) of Renmin University of China, the Open Research Fund of the State Key Laboratory of Information Security, Open Project of Key Laboratory of Cryptologic Technology and Information Security, Ministry of Education, Shandong University (Institute of Information Engineering, Chinese Academy of Sciences and the Open Research Fund of Beijing Key Laboratory of Trusted Computing.
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by V. Loia.
Rights and permissions
About this article
Cite this article
Liu, Y., Ling, J., Wu, Q. et al. Scalable privacy-enhanced traffic monitoring in vehicular ad hoc networks. Soft Comput 20, 3335–3346 (2016). https://doi.org/10.1007/s00500-015-1737-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-015-1737-y