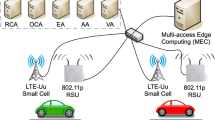
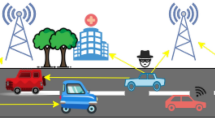
Abstract
The quick revolution on the wireless communication technologies had opened the gate towards promising implementations; Vehicular-Ad-hoc Networks (VANETs) and the safety-enhancing applications provided by the Internet of Vehicles (IoV) paradigm are one of them. By periodically broadcasting safety-beacons, vehicles can ensure a better safety-driving experience since beacons contain fine-grained location that is sent to the neighborhood. Nevertheless, some attacks basing on falsify or encrypt location-related data are threatening the road-safety considerably. In this paper, and by assuming a GPS-spoofing attack originated from Unmanned-Aircraft-Vehicles (UAV) system, we provide a Security-Aware Monitoring Approach (SAMA) that protects vehicles against such location abusing by allowing the Law-Side Authority (LSA) to monitor the potential malicious or tricked vehicles. SAMA is Implemented using the triangulation concept via Received-Signal-Strength-Indicator (RSSI) in conjunction with C++ map and multimap data-structures. The performances of SAMA are evaluated in terms of location-estimation precision and beacons collection per type.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Shilin, P., Kirichek, R., Paramonov, A., Koucheryavy, A.: Connectivity of VANET segments using UAVs. In: Internet of Things, Smart Spaces, and Next Generation Networks and Systems, pp. 492–500. Springer, Cham (2016), https://doi.org/10.1007/978-3-319-23126-6
Karagiannis, G., et al.: Vehicular networking: a survey and tutorial on requirements, architectures, challenges, standards and solutions. IEEE Commun. Surv. Tutor. 13(4), 584–616 (2011)
Chen, S., et al.: Vehicle-to-everything (v2x) services supported by LTE-based systems and 5g. IEEE Commun. Stand. Mag. 1(2), 70–76 (2017)
Sun, S.-H., Hu, J.-L., Peng, Y., Pan, X.-M., Zhao, L., Fang, J.-Y.: Support for vehicle-to-everything services based on LTE. IEEE Wirel. Commun. 23(3), 4–8 (2016)
Parkinson, B.W., Enge, P., Axelrad, P., Spilker, Jr., J.J.: Global Positioning System: Theory and Applications, Vol. II. American Institute of Aeronautics and Astronautics, Reston (1996)
Babaghayou, M., Labraoui, N., Ari, A.A.A.: Location-privacy evaluation within the extreme points privacy (EPP) scheme for VANET users. Int. J. Strat. Inf. Technol. Appl. 10(2), 44–58 (2019)
Saeed, N., Ahmad, W., Bhatti, D.M.S.: Localization of vehicular ad-hoc networks with RSS based distance estimation. In: 2018 International Conference on Computing, Mathematics and Engineering Technologies (iCoMET), pp. 1–6. IEEE (2018)
Kerrache, C.A., Calafate, C.T., Cano, J.-C., Lagraa, N., Manzoni, P.: Trust management for vehicular networks: an adversary-oriented overview. IEEE Access 4, 9293–9307 (2016)
Al-Sultan, S., Al-Doori, M.M., Al-Bayatti, A.H., Zedan, H.: A comprehensive survey on vehicular ad hoc network. J. Netw. Comput. Appl. 37, 380–392 (2014)
Babaghayou, M., Labraoui, N., Ari, A.A.A., Gueroui, A.M.: Transmission range changing effects on location privacy-preserving schemes in the internet of vehicles. Int. J. Strat. Inf. Technol. Appl. 10(4), 33–54 (2019)
Ferrag, M.A., Babaghayou, M., Yazici, M.A.: Cyber security for fog-based smart grid SCADA systems: solutions and challenges. J. Inf. Secur. Appl. 52,(2020)
Babaghayou, M., Labraoui, N., Ferrag, M.A., Maglaras, L.: Between location protection and overthrowing: a contrariness framework study for smart vehicles. In: 39th IEEE International Conference on Consumer Electronics (ICCE). IEEE (2020)
Babaghayou, M., Labraoui, N., Ari, A.A.A., Lagraa, N., Ferrag, M.A.: Pseudonym change-based privacy-preserving schemes in vehicular ad-hoc networks: a survey. J. Inf. Secur. Appl. 55 (2020)
Hasrouny, H., Samhat, A.E., Bassil, C., Laouiti, A.: VANET security challenges and solutions: a survey. Veh. Commun. 7, 7–20 (2017)
Yao, Y., Xiao, B., Yang, G., Hu, Y., Wang, L., Zhou, X.: Power control identification: a novel Sybil attack detection scheme in VANETs using RSSI. IEEE J. Select. Areas Commun. 37(11), 2588–2602 (2019)
Tchakounté, F., Calvin, K.A., Ari, A.A.A., Mbogne, D.J.F.: A smart contract logic to reduce hoax propagation across social media. J. King Saud. Univ. Comput. Inf. Sci. (2020)
Ferrag, M.A., Maglaras, L., Ahmim, A., Derdour, M., Janicke, H.: RDTIDS: rules and decision tree-based intrusion detection system for internet-of-things networks. Fut. Internet 12(3), 44 (2020)
Risbud, P., Gatsis, N., Taha, A.: Vulnerability analysis of smart grids to GPS spoofing. IEEE Trans. Smart Grid 10(4), 3535–3548 (2018)
Shepard, D.P., Humphreys, T.E., Fansler, A.A.: Evaluation of the vulnerability of phasor measurement units to GPS spoofing attacks. Int. J. Crit. Infrastruct. Prot. 5(3–4), 146–153 (2012)
Warner, J.S., Johnston, R.G.: GPS spoofing countermeasures. Homel. Secur. J. 25(2), 19–27 (2003)
Kosmanos, D., et al.: A novel intrusion detection system against spoofing attacks in connected electric vehicles. Array 5, 100013 (2020)
Shakhatreh, H., et al.: Unmanned aerial vehicles UAVs): a survey on civil applications and key research challenges. IEEE Access 7, 48 572–48 634 (2019)
Freudiger, J., Raya, M., Félegyházi, M., Papadimitratos, P., Hubaux, J.-P.: Mix-zones for location privacy in vehicular networks. In: ACM Workshop on Wireless Networking for Intelligent Transportation Systems (WiN-ITS), No. LCA-CONF-2007-016 (2007)
Wasef, A., Shen, X.S.: Rep: location privacy for VANETs using random encryption periods. Mobile Netw. Appl. 15(1), 172–185 (2010)
Ying, B., Makrakis, D., Mouftah, H.T.: Dynamic mix-zone for location privacy in vehicular networks. IEEE Commu. Lett. 17(8), 1524–1527 (2013)
Ahmad, M., Farid, M.A., Ahmed, S., Saeed, K., Asharf, M., Akhtar, U.: Impact and detection of GPS spoofing and countermeasures against spoofing. In: 2019 2nd International Conference on Computing, Mathematics and Engineering Technologies (iCoMET), pp. 1–8. IEEE (2019)
Noh, J., et al.: Tractor beam: safe-hijacking of consumer drones with adaptive GPS spoofing. ACM Trans. Privacy Secur. 22(2), 1–26 (2019)
Guo, Y., Wu, M., Tang, K., Tie, J., Li, X.: Covert spoofing algorithm of UAV based on GPS/INS-integrated navigation. IEEE Trans. Veh. Technol. 68(7), 6557–6564 (2019)
Bahl, p., Padmanabhan, V.N.: Radar: an in-building RF-based user location and tracking system. In: Proceedings IEEE INFOCOM 2000 Conference on Computer Communications, Nineteenth Annual Joint Conference of the IEEE Computer and Communications Societies (Cat. No. 00CH37064), vol. 2. pp. 775–784. IEEE (2000)
Youssef, M.A., Agrawala, A., Shankar, A.U.: WLAN location determination via clustering and probability distributions. In: Proceedings of the First IEEE International Conference on Pervasive Computing and Communications, 2003 (PerCom 2003), pp. 143–150. IEEE (2003)
Svečko, J., Malajner, M., Gleich, D.: Distance estimation using RSSI and particle filter. ISA Trans. 55, 275–285 (2015)
Jiang, D., Delgrossi, L.: IEEE 802.11 p: Towards an international standard for wireless access in vehicular environments. In: VTC Spring 2008-IEEE Vehicular Technology Conference, pp. 2036–2040. IEEE (2008)
Tengler, S., Auflick, J.: Vehicle on-board unit. US Patent 7,554,435, 30 June 2009
Park, S., Aslam, B., Turgut, D., Zou, C.C.: Defense against sybil attack in vehicular ad hoc network based on roadside unit support. In: MILCOM 2009–2009 IEEE Military Communications Conference, pp. 1–7. IEEE (2009)
Sumra, I.A., Ahmad, I., Hasbullah, H., et al.: Behavior of attacker and some new possible attacks in vehicular ad hoc network (VANET). In: Sumrain, I.A., et al. (eds.) 3rd International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT), pp. 1–8. IEEE (2011)
Wegener, S., et al.: UAV autonomous operations for airborne science missions. In: AIAA 3rd “Unmanned Unlimited” Technical Conference, Workshop and Exhibit, 2004, p. 6416 (2004)
Haq, S., Bashir, A., Sholla, S.: Cloud of things: architecture, research challenges, security threats, mechanisms and open challenges. Jordan. J. Comput. Inf. Technol. 06(04), 415–433 (2020)
Babaghayou, A., Labraoui, N., Ari, A.A.A., Ferrag, M.A., Maglaras, L.: The impact of the adversary’s eavesdropping stations on the location privacy level in internet of vehicles. In: 2020 5th South-East Europe Design Automation, Computer Engineering, Computer Networks and Social Media Conference (SEEDA-CECNSM), 2020, pp. 1–6 (2020)
\({\rm {{<}map{>}}}\). http://www.cplusplus.com/reference/map. Accessed 01 Dec 2021
Du, J., Diouris, J.-F., Wang, Y.: A RSSI-based parameter tracking strategy for constrained position localization. EURASIP J. Adv. Signal Process. 2017(1), 77 (2017)
Sommer, C., German, R., Dressler, F.: Bidirectionally coupled network and road traffic simulation for improved IVC analysis. IEEE Trans. Mobile Comput. 10(1), 3–15 (2011)
Emara, K.: Poster: PREXT: privacy extension for veins VANET simulator. In: IEEE Vehicular Networking Conference (VNC). 2016, pp. 1–2. IEEE (2016)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 ICST Institute for Computer Sciences, Social Informatics and Telecommunications Engineering
About this paper
Cite this paper
Babaghayou, M., Labraoui, N., Ari, A.A.A., Lagraa, N., Ferrag, M.A., Maglaras, L. (2022). SAMA: Security-Aware Monitoring Approach for Location Abusing and UAV GPS-Spoofing Attacks on Internet of Vehicles. In: Jin, H., Liu, C., Pathan, AS.K., Fadlullah, Z.M., Choudhury, S. (eds) Cognitive Radio Oriented Wireless Networks and Wireless Internet. CROWNCOM WiCON 2021 2021. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, vol 427. Springer, Cham. https://doi.org/10.1007/978-3-030-98002-3_25
Download citation
DOI: https://doi.org/10.1007/978-3-030-98002-3_25
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-98001-6
Online ISBN: 978-3-030-98002-3
eBook Packages: Computer ScienceComputer Science (R0)